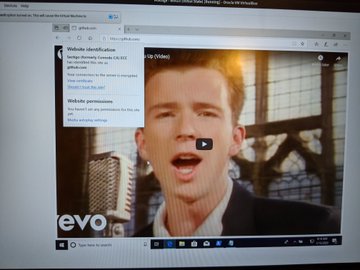
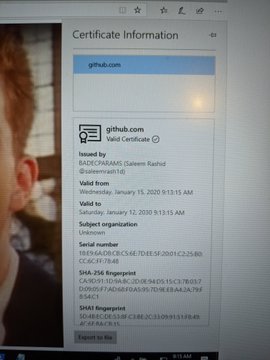
Two proof-of-concept exploits were publicly released for the major Microsoft crypto-spoofing vulnerability.
Two proof-of-concept (PoC) exploits have been publicly released for the recently-patched crypto-spoofing vulnerability found by the National Security Agency and reported to Microsoft.
The vulnerability (CVE-2020-0601) could enable an attacker to spoof a code-signing certificate (necessary for validating executable programs in Windows) in order to make it appear like an application was from a trusted source. The flaw made headlines when it was disclosed earlier this week as part of Microsoft’s January Patch Tuesday security bulletin. It marked the first time the NSA had ever publicly reported a bug to Microsoft.
The two PoC exploits were published to GitHub on Thursday. Either could potentially allow an attacker to launch MitM (man-in-the-middle) attacks – allowing an adversary to spoof signatures for files and emails and fake signed-executable code inside programs that are launched inside Windows. One PoC exploit was released by Kudelski Security and the other by a security researcher under the alias “Ollypwn”.
[Listen to further analysis of the Microsoft crypto flaw, below, on the Threatpost Podcast]
According to Microsoft’s advisory, the spoofing vulnerability exists in the way Windows CryptoAPI (Microsoft’s API that enables developers to secure Windows-based applications using cryptography) validates Elliptic Curve Cryptography (ECC) certificates. Kudelski Security in a blog post said they launched the PoC using a “curve P384” certificate, which uses ECC (specifically, the USERTrust ECC Certificate Authority). Researcher were able to craft a key used to sign the “curve P384” certificate with an arbitrary domain name. This certificate would subsequently be recognized by Windows’ CryptoAPI as trusted.
Another similar PoC exploit was publicly released by Denmark-based security expert “Ollypwn.”
“When Windows checks whether the certificate is trusted, it’ll see that it has been signed by our spoofed CA,” said “Ollypwn” in a write up of his PoC exploit. “It then looks at the spoofed CA’s public key to check against trusted CA’s. Then it simply verifies the signature of our spoofed CA with the spoofed CA’s generator – this is the issue.”
A third PoC exploit was developed by security expert Saleem Rashid; who said on Twitter, Wednesday, that the PoC allowed him to fake TLS certificates and set up sites that look like legitimate ones. However, Rashid did not make his PoC exploit code public.
1,179 people are talking about this
Researchers say that while the recently-released PoC exploits work, they show that the flaw is not easily exploitable for attackers, particularly because victims would also need to first visit a very specific website, making a targeted attack more difficult.
“In the end, please keep in mind that such a vulnerability is not at risk of being exploited by script kiddies or ransomware,” Kudelski Security researchers said in their analysis. “While it is still a big problem because it could have allowed a Man-in-the-Middle attack against any website, you would need to face an adversary that owns the network on which you operate, which is possible for nation-state adversaries, but less so for a script kiddie.”
Tech support site AskWoody agreed: “There’s no question the code works — but it has a prerequisite. In order to get bitten by the security hole, you have to first visit a specific site. That site will load a security certificate that’s instrumental in making the PoC code work. That severely limits the threat, eh?”
Despite the roadblocks to exploitation, security experts say that publicly-released PoC exploits can pave the way for future exploitation of CVE-2020-0601 by adversaries. Researchers urge Microsoft customers to make sure that their systems are up to date.
“Assume that this vulnerability has already been weaponized, probably by criminals and certainly by major governments,” Bruce Schneier said in a Wednesday analysis. “Even assume that the NSA is using this vulnerability — why wouldn’t it?”
Two proof-of-concept (PoC) exploits have been publicly released for the recently-patched crypto-spoofing vulnerability found by the National Security Agency and reported to Microsoft.
The vulnerability (CVE-2020-0601) could enable an attacker to spoof a code-signing certificate (necessary for validating executable programs in Windows) in order to make it appear like an application was from a trusted source. The flaw made headlines when it was disclosed earlier this week as part of Microsoft’s January Patch Tuesday security bulletin. It marked the first time the NSA had ever publicly reported a bug to Microsoft.
The two PoC exploits were published to GitHub on Thursday. Either could potentially allow an attacker to launch MitM (man-in-the-middle) attacks – allowing an adversary to spoof signatures for files and emails and fake signed-executable code inside programs that are launched inside Windows. One PoC exploit was released by Kudelski Security and the other by a security researcher under the alias “Ollypwn”.
[Listen to further analysis of the Microsoft crypto flaw, below, on the Threatpost Podcast]
According to Microsoft’s advisory, the spoofing vulnerability exists in the way Windows CryptoAPI (Microsoft’s API that enables developers to secure Windows-based applications using cryptography) validates Elliptic Curve Cryptography (ECC) certificates. Kudelski Security in a blog post said they launched the PoC using a “curve P384” certificate, which uses ECC (specifically, the USERTrust ECC Certificate Authority). Researcher were able to craft a key used to sign the “curve P384” certificate with an arbitrary domain name. This certificate would subsequently be recognized by Windows’ CryptoAPI as trusted.
Another similar PoC exploit was publicly released by Denmark-based security expert “Ollypwn.”
“When Windows checks whether the certificate is trusted, it’ll see that it has been signed by our spoofed CA,” said “Ollypwn” in a write up of his PoC exploit. “It then looks at the spoofed CA’s public key to check against trusted CA’s. Then it simply verifies the signature of our spoofed CA with the spoofed CA’s generator – this is the issue.”
A third PoC exploit was developed by security expert Saleem Rashid; who said on Twitter, Wednesday, that the PoC allowed him to fake TLS certificates and set up sites that look like legitimate ones. However, Rashid did not make his PoC exploit code public.
1,179 people are talking about this
Researchers say that while the recently-released PoC exploits work, they show that the flaw is not easily exploitable for attackers, particularly because victims would also need to first visit a very specific website, making a targeted attack more difficult.
“In the end, please keep in mind that such a vulnerability is not at risk of being exploited by script kiddies or ransomware,” Kudelski Security researchers said in their analysis. “While it is still a big problem because it could have allowed a Man-in-the-Middle attack against any website, you would need to face an adversary that owns the network on which you operate, which is possible for nation-state adversaries, but less so for a script kiddie.”
Tech support site AskWoody agreed: “There’s no question the code works — but it has a prerequisite. In order to get bitten by the security hole, you have to first visit a specific site. That site will load a security certificate that’s instrumental in making the PoC code work. That severely limits the threat, eh?”
Despite the roadblocks to exploitation, security experts say that publicly-released PoC exploits can pave the way for future exploitation of CVE-2020-0601 by adversaries. Researchers urge Microsoft customers to make sure that their systems are up to date.
“Assume that this vulnerability has already been weaponized, probably by criminals and certainly by major governments,” Bruce Schneier said in a Wednesday analysis. “Even assume that the NSA is using this vulnerability — why wouldn’t it?”