Over 100,000 sites have been impacted in a supply chain attack by the Polyfill.io service after a Chinese company acquired the domain and the script was modified to redirect users to malicious and scam sites.
A
polyfill is code, such as JavaScript, that adds modern functionality to older browsers that do not usually support it. For example, it adds JavaScript functions that are not available for older browsers but are present in modern ones.
The polyfill.io service is used by
hundreds of thousands of sites to allow all visitors to use the same codebase, even if their browsers do not support the same modern features as newer ones.
Polyfill.io supply chain attack
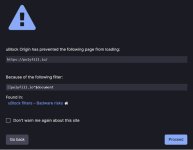
Today, cybersecurity company Sansec warned that the polyfill.io domain and service was
purchased earlier this year by a Chinese company named 'Funnull' and the script has been modified to introduce malicious code on websites in a supply chain attack.
"However, in February this year, a Chinese company bought the domain and the Github account. Since then, this domain was caught injecting
malware on mobile devices via any site that embeds cdn.polyfill.io,"
explains Sansec.
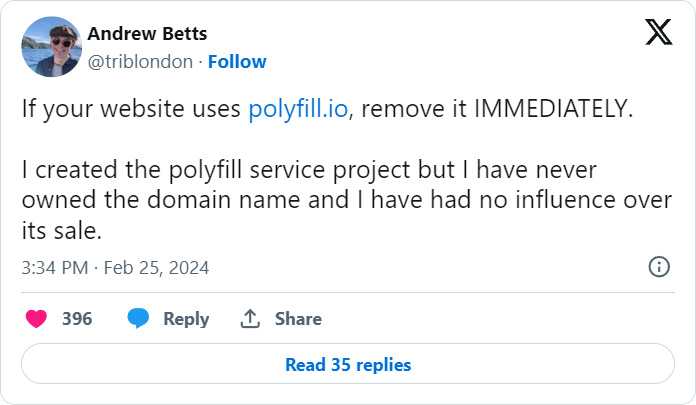
When the polyfill.io was purchased, the project developer warned that he never owned the polyfill.io site and that all websites should remove it immediately. To reduce the risk of a potential supply chain attack,
Cloudflare and
Fastly set up their own mirrors of the Polyfill.io service so that websites could use a trusted service.