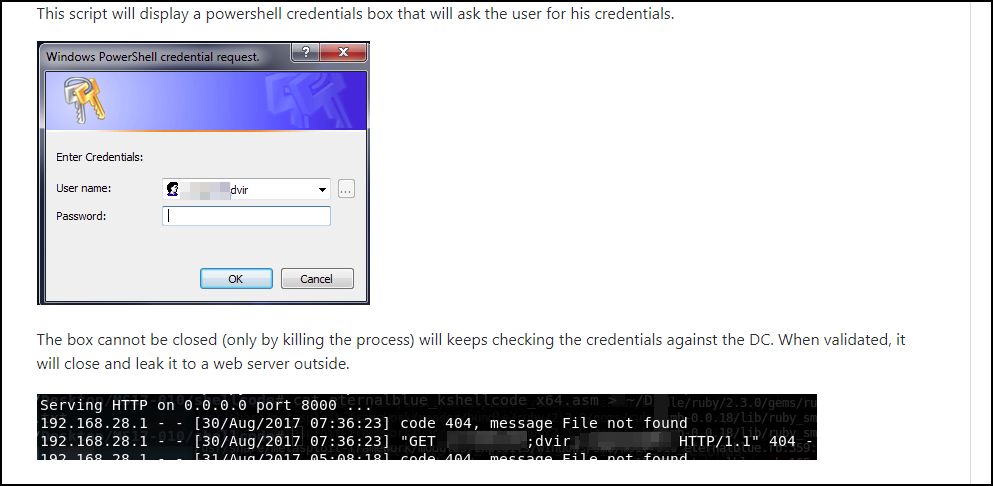
A new PowerShell script was posted on Github recently that prompts a victim to enter their login credentials, checks if they are correct, and then sends the credentials to a remote server. This allows an attacker to distribute the script and harvest domain login credentials from their victims.
Description on Github
This Github script utilizes the Get-Credential PowerShell cmdlet to display the login prompt that asks the user to enter their credentials. When the user enters their credentials, the script will try to use them to authenticate to the victim's domain, and if successful, will send the credentials to a remote server. If the entered credentials are incorrect, the script will keep prompting the user to enter their credentials.
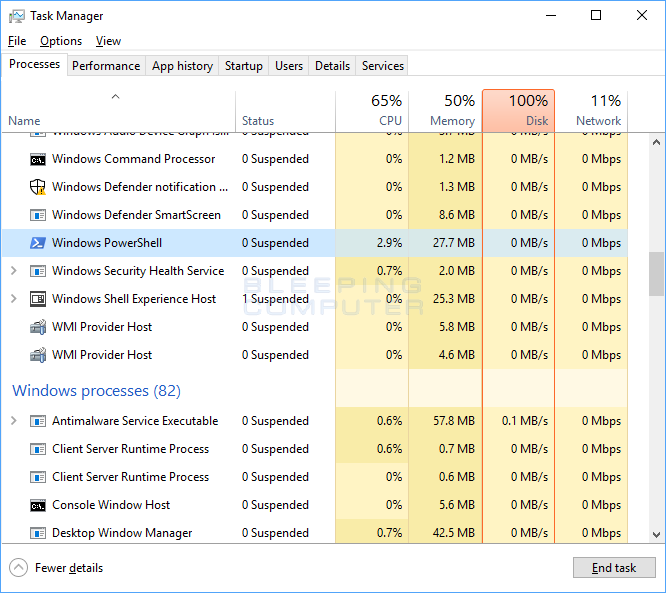
At this point the only way to terminate the prompt, is to open Task Manager, look for a process called "Windows PowerShell", and then terminate it.
Task Manager
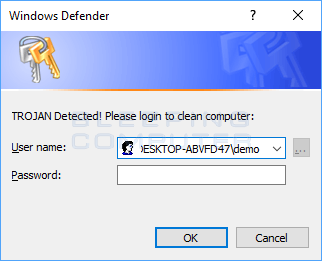
Thankfully, the login prompt displayed by this particular script makes it easy to spot as the alert will be titled "Windows PowerShell credential request" and will contain a blue ribbon with a set of keys as shown below.
....
........
...
............