- Jul 22, 2014
- 2,525
This past Saturday security researchers Kafeine, MalwareHunterteam, BroadAnalysis, and David Martínez discovered a new ransomware being distributed through EITest into the RIG exploit kit. As this ransomware was only distributed for one day and does not securely encrypt files, it makes me believe that this may have been a test distribution run.
While the colors and interface used by this ransomware have a striking resemblance to CTB-Locker/Critroni, it is written in a different language and there are no distinguishing strings in the ransom notes or executables. Since it's programmed in Python and the script is called cl.py, I will be referring to it as PyCL in this article.
PyCL Distributed through EITest and the RIG Exploit Kit
Starting on Saturday, numerous researchers noticed that EITest was pushing visitors to the RIG exploit kit, which was distributing this new PyCL ransomware. This was done through hacked sites that redirected the visitor to RIG, which would then try and exploit vulnerabilities on the computer in order to install the ransomware.
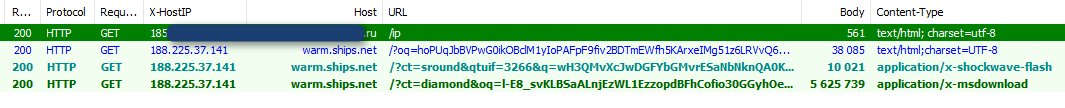
Fiddler Capture of EITest
Source: Kafeine
According to Kafeine, EITest was distributing both Cerber and PyCL at the same time. The PyCL distribution, though, only lasted for that one day.
Could PyCL be Part of a RaaS?
....
.....
Since this ransomware does not currently delete the original files, those who are infected do not have to worry about losing their files. If this changes, though, the ransomware will be further analyzed for weakness that can be exploited to decrypt files for free.
....
While the colors and interface used by this ransomware have a striking resemblance to CTB-Locker/Critroni, it is written in a different language and there are no distinguishing strings in the ransom notes or executables. Since it's programmed in Python and the script is called cl.py, I will be referring to it as PyCL in this article.
PyCL Distributed through EITest and the RIG Exploit Kit
Starting on Saturday, numerous researchers noticed that EITest was pushing visitors to the RIG exploit kit, which was distributing this new PyCL ransomware. This was done through hacked sites that redirected the visitor to RIG, which would then try and exploit vulnerabilities on the computer in order to install the ransomware.

Fiddler Capture of EITest
Source: Kafeine
According to Kafeine, EITest was distributing both Cerber and PyCL at the same time. The PyCL distribution, though, only lasted for that one day.
Could PyCL be Part of a RaaS?
....
.....
Since this ransomware does not currently delete the original files, those who are infected do not have to worry about losing their files. If this changes, though, the ransomware will be further analyzed for weakness that can be exploited to decrypt files for free.
....
Last edited:
