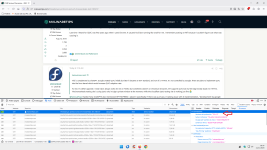
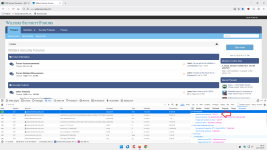
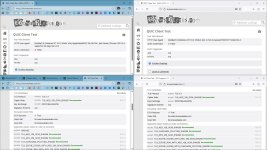
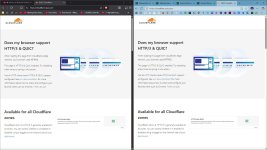
It is interesting to note that Browserleaks.com has implemented the QUIC + ECH test:
QUIC Client Test - QUIC+HTTP/3 Fingerprinting
Please also note that not all websites use QUIC, even if your browser has enabled QUIC by default.
MT uses QUIC:
If you do not want your browser to use QUIC, you must disable it.
QUIC Client Test - QUIC+HTTP/3 Fingerprinting
Please also note that not all websites use QUIC, even if your browser has enabled QUIC by default.
MT uses QUIC:

If you do not want your browser to use QUIC, you must disable it.