A critical remote code execution (RCE) vulnerability in the popular open-source torrent client qBittorrent left users exposed for over 14 years due to a lack of SSL certificate validation in its DownloadManager class.
The issue, which was introduced via a commit in April 2010, was finally addressed earlier this week with the release of qBittorrent version 5.0.1. Discovered and reported by cybersecurity researcher J. Sharp from Sharp Security, the vulnerability could allow attackers to conduct RCE attacks and compromise users via Man-in-the-middle (MITM) attacks by exploiting hardcoded URLs used by the application.
Vulnerability overview
The problem originates from the DownloadManager class within qBittorrent, which bypassed SSL certificate validation for any downloaded file across multiple features, including torrent downloads, RSS feeds, and search engine functions. This behavior meant that qBittorrent trusted any SSL certificate — whether expired, self-signed, or malicious — across several critical functionalities, creating numerous attack vectors.
Sharp’s report highlighted that several code paths impacted users, including:
Python Installation Prompt on Windows: The Windows version of qBittorrent attempts to install or update Python by downloading an executable from a hardcoded URL whenever Python is absent. If users select “Yes” to the automatic prompt, qBittorrent downloads and installs a Python executable in passive mode without verification. This process has been present since version 3.2.1 (2015) and affected versions up to 5.0.0.
Browser Hijacking Through Update Checks: The software checks for updates through an RSS feed from a hardcoded URL. In an MITM scenario, an attacker could modify the XML data, redirecting users to malicious URLs disguised as legitimate update downloads. While qBittorrent’s open-source nature allows signature verification, this process is neither automatic nor enforced.
RSS Feed Vulnerability: The application also processes user-configured RSS feeds without validating URLs, enabling arbitrary URL injection. When users click on these injected URLs, they could unknowingly download malware. Additionally, this RSS feed component, combined with CVE-2019-13640, could allow RCE through manipulated torrent metadata.
Automatic Geolocation Data Download: qBittorrent automatically fetches a MaxMind GeoIP database from a hardcoded URL, decompressing it upon receipt. Any vulnerabilities within the decompression library could be exploited to execute arbitrary code, although the latest code mitigates this risk through improved buffer handling.
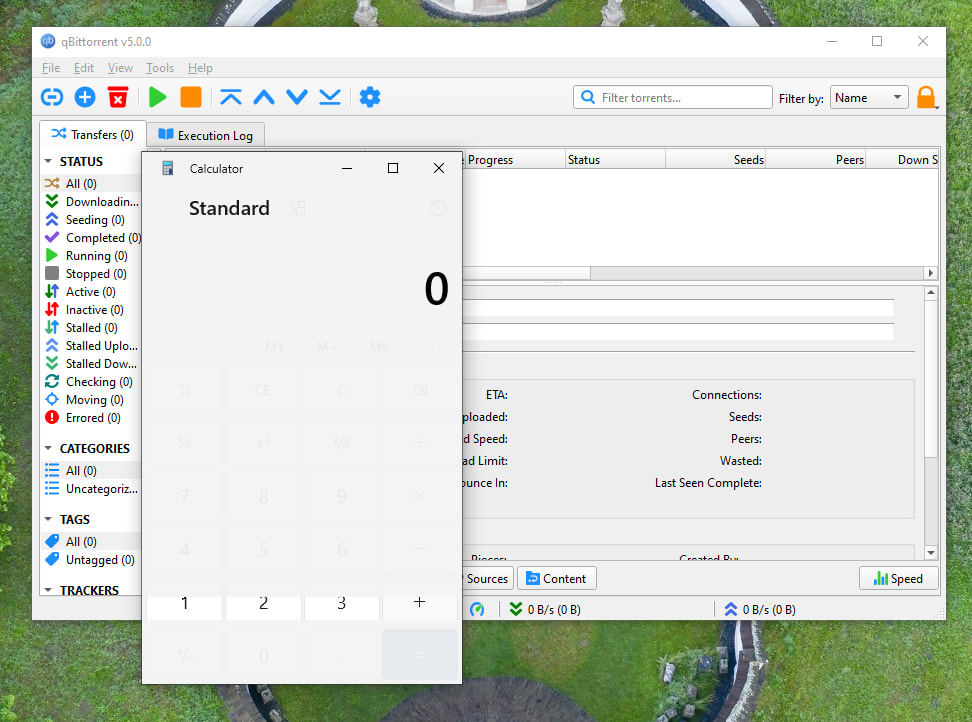
Launching Windows Calculator through qBittorrent via process injection
Sharp Security
Impact and exploitation scenarios
qBittorrent, a widely used open-source torrent client with millions of users, provides essential features for torrent downloading, search engine plugins, and RSS feed integration. While generally considered secure, the absence of SSL certificate validation introduced a significant threat to user security, especially in regions with restrictive internet policies where MITM attacks are prevalent. With this vulnerability, a malicious actor could exploit hardcoded URLs to inject harmful software or harvest data without detection.
The lack of SSL verification allows several types of MITM attacks. Sharp demonstrated exploit possibilities with the mitmproxy tool, showcasing how an attacker could use scripted replacements to achieve one of the following scenarios:
- An attacker could replace the Python executable URL to deliver malware, gaining remote access with minimal user interaction.
- Update URL modification to redirect users to fake updates, leading to malicious downloads, browser hijacking, and potential system compromise.
- Attackers could poison RSS feeds, tricking users into clicking on compromised links and unknowingly executing harmful code.
qBittorrent developers addressed this vulnerability by implementing certificate verification on October 12, 2024. However, the first fully patched release, version 5.0.1, was published on October 28, 2024. To protect themselves, users should upgrade to that version immediately. If impossible, they should stop using earlier versions of qBittorrent and preferably switch to a different client.