silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,178
In a new report released today by AhnLab Security Emergency response Center (ASEC), researchers explain how APT37 is now using a new malware strain called 'M2RAT' that uses a shared memory section for commands and data exfiltration and leaves very few operational traces on the infected machine.
The recent attacks observed by ASEC started in January 2023, when the hacking group sent phishing emails containing a malicious attachment to their targets.
Opening the attachment triggers the exploitation of an old EPS vulnerability (CVE-2017-8291) in the Hangul word processor commonly used in South Korea. The exploit will cause shellcode to run on a victim's computer that downloads and executes a malicious executed stored within a JPEG image.
This JPG image file uses steganography, a technique that allows hiding code inside files, to stealthily introduce the M2RAT executable ("lskdjfei.exe") onto the system and inject it into "explorer.exe."
The M2RAT backdoor acts as a basic remote access trojan that performs keylogging, data theft, command execution, and the taking of screenshots from the desktop.
The screenshot-snapping function is activated periodically and works autonomously without requiring a specific operator command.
The malware supports the following commands, which collect information from the infected device and then send it back to the C2 server for the attackers to review.
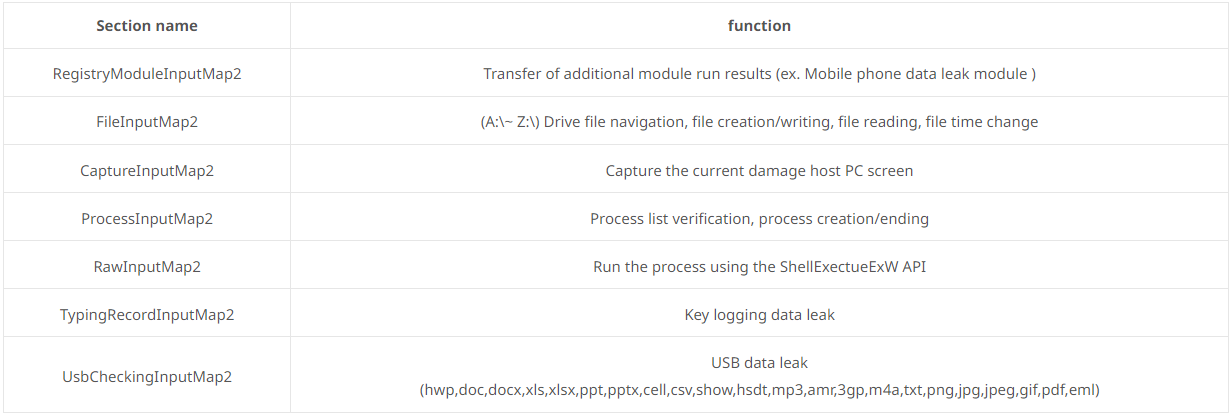
Supported CMD commands (ASEC)

RedEyes hackers use new malware to steal data from Windows, phones
The APT37 threat group (aka 'RedEyes' or 'ScarCruft') has been spotted using a new evasive malware named 'M2RAT' along with steganography to attack specific individuals for intelligence collection.