- Feb 4, 2016
- 2,520
Scientists from Florida International University and Bloomberg have created a custom two-factor authentication (2FA) system that relies on users taking a photo of a personal object.
The act of taking the photo comes to replace the cumbersome process of using crypto-based hardware security keys (e.g., YubiKey devices) or entering verification codes received via SMS or voice call.
The new system is named Pixie, and researchers argue it is more secure than the aforementioned solutions.
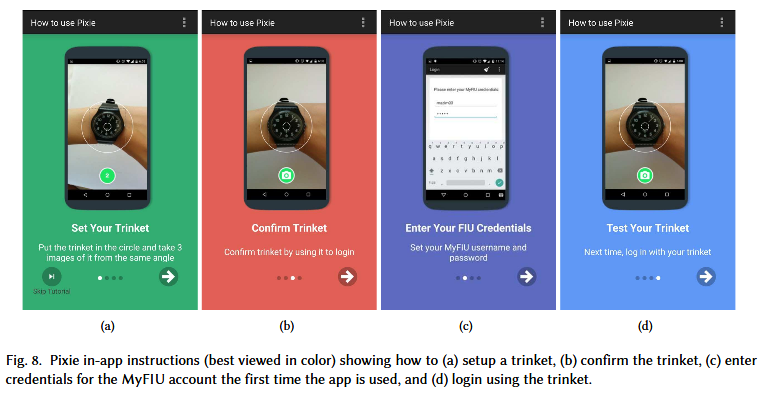
Pixie lets users authenticate with a photo of a favorite object
Pixie works by requiring users to choose an object as their 2FA key. When they set up the Pixie 2FA protection, they take an initial photo of the object that will be used for reference. Every time users try to log into their account again, they re-take a photo of the same object, and an app installed on their phone compares the two photos.
Pixie has a false accept rate of only 0.09%
In automated tests, Pixie achieved a false accept rate below 0.09% in a brute force attack with 14.3 million authentication attempts — nine wrong identifications every 10,000 login attempts.
Furthermore, in a test with 42 participants that took place over eight days in three different sessions, researchers say that "Pixie outperforms text-based passwords on memorability, speed, and user preference."
Pixie app available
Researchers are still working on the Pixie system, but you can get the app from this GitHub repository and test it out.
The research team presented the Pixie 2FA system at this month's Association for Computing Machinery on Interactive, Mobile, Wearable and Ubiquitous Technologies.
A scientific paper describing their system is available here, and is entitled "Camera Based Two Factor Authentication Through Mobile and Wearable Devices."
