- Jan 8, 2017
- 1,320
The operators of some tech support scam websites have found a new trick to block visitors on their shady sites and scare non-technical users into paying for unneeded software or servicing fees.
The trick relies on using JavaScript code loaded on these malicious pages to initiate thousands of file download operations that quickly take up the user's memory resources, freezing Chrome on the scammer's site.
The trick is meant to drive panicked users into calling one of the tech support phone numbers shown on the screen. A GIF of one of these malicious sites freezing a Chrome browser running the latest version (64.0.3282.140) is embedded below.
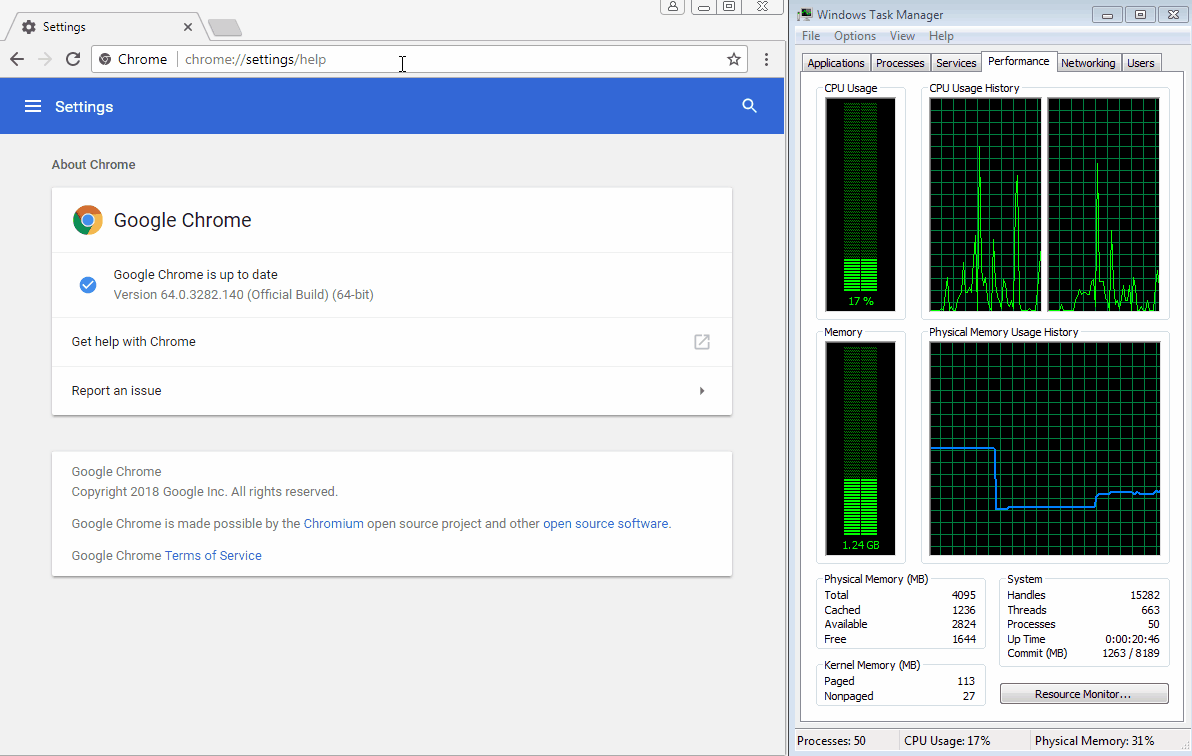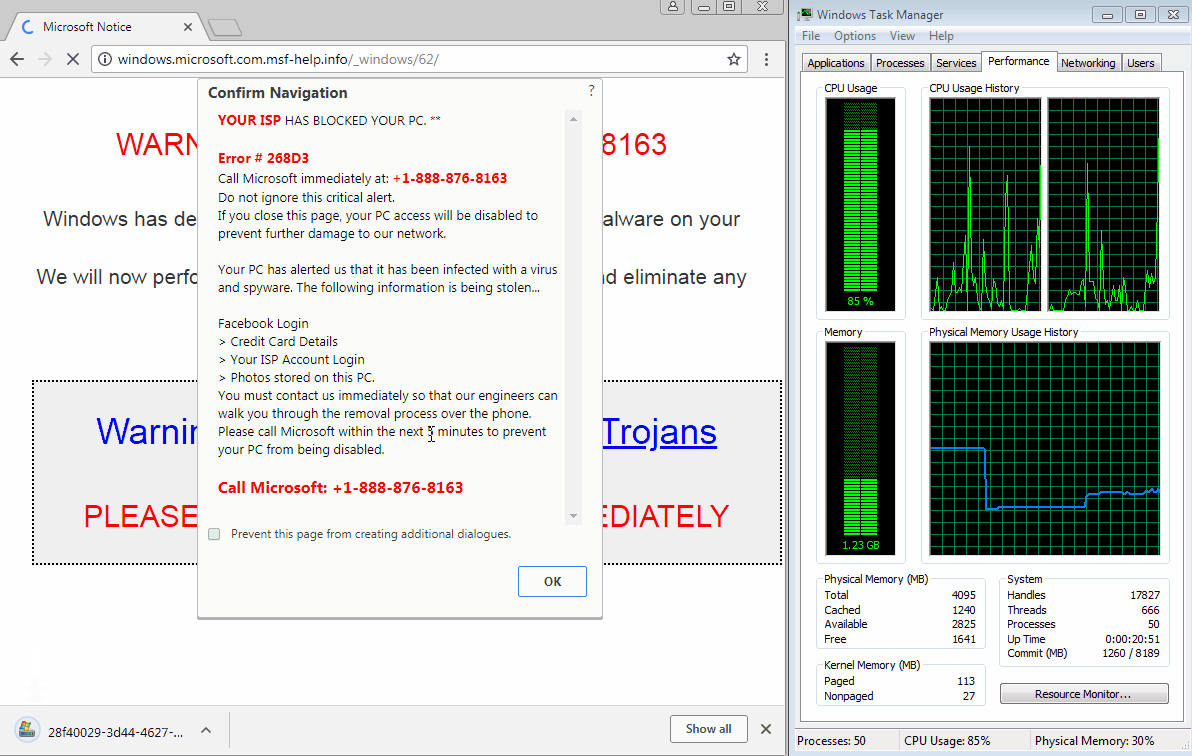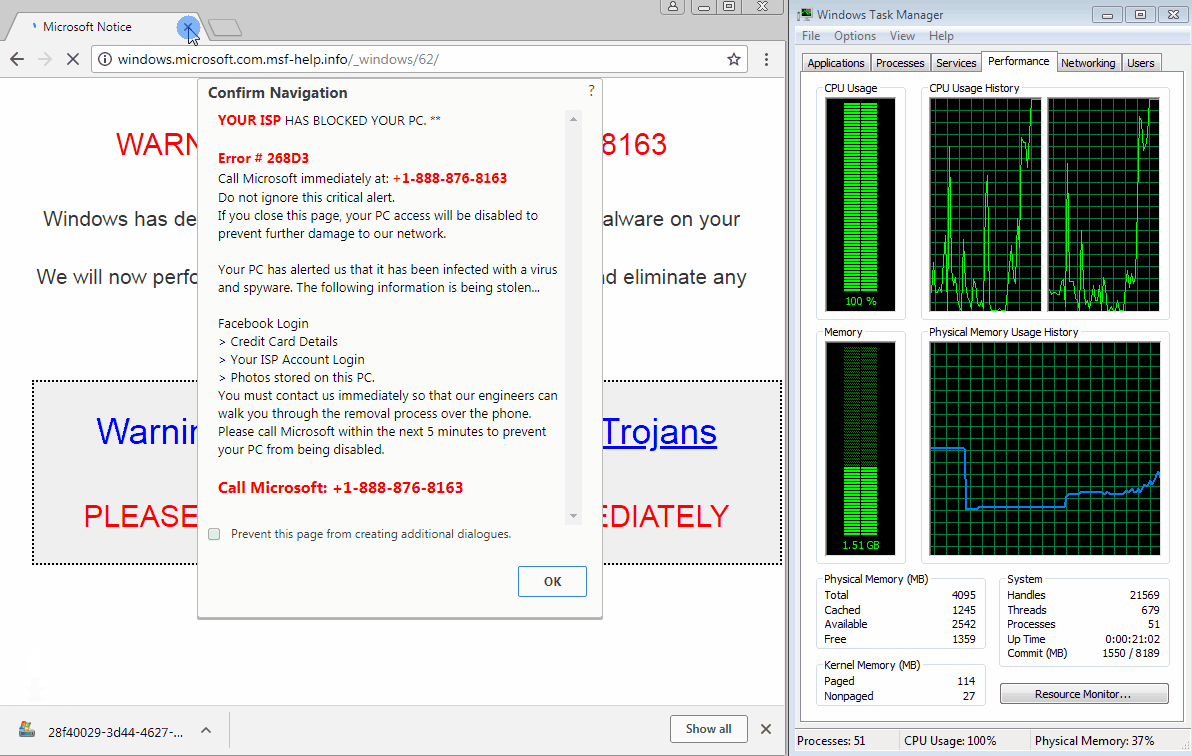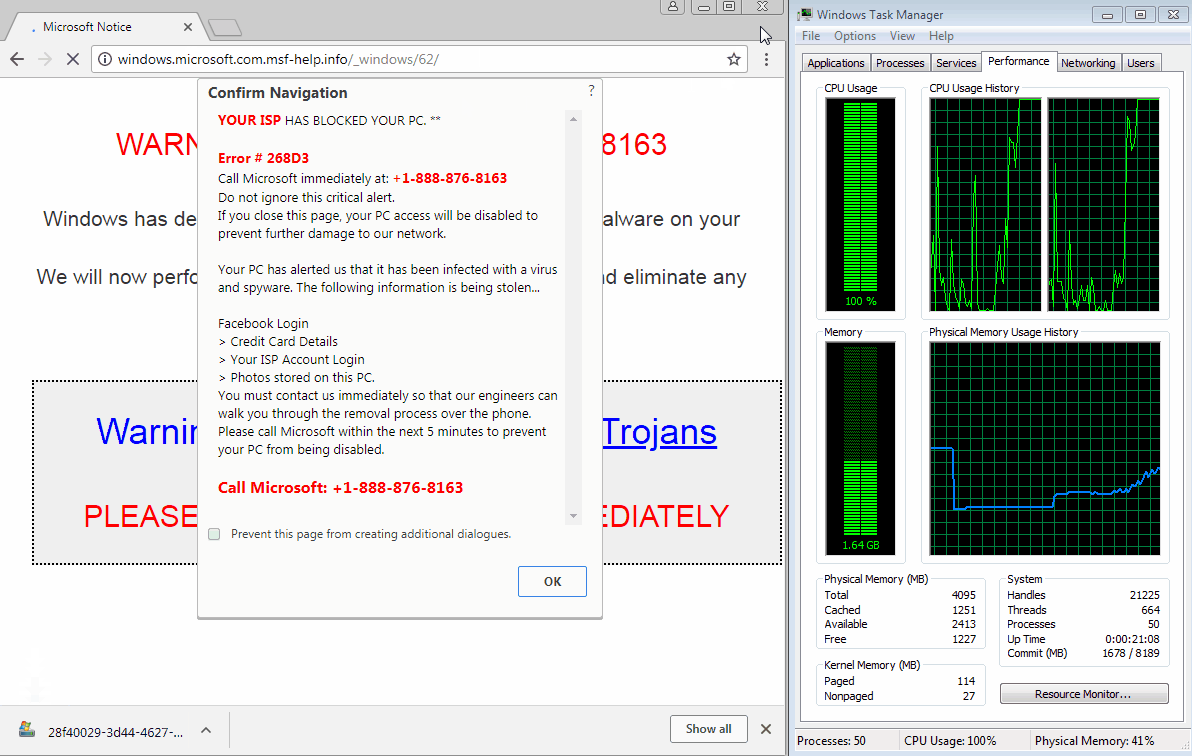
According to Jérôme Segura —Malwarebytes leading expert in tech support scam operations, malvertising, and exploit kits— this new trick utilizes the JavaScript Blob method and the window.navigator.msSaveOrOpenBlob function to achieve the "download bomb" that freezes Chrome.
The expert says the only way to escape the tech support website is to close Chrome via Windows Task Manager.
When the user restarts Chrome, if Chrome is configured to reload the previous session, Segura advises users to quickly close the shady site while the page is loading and before the malicious code has a chance to execute.
"Download bomb" trick spotted after Google fixed previous trick
Segura says he spotted tech support scammers abusing this new trick after Google engineers patched Chrome against a previous technique that utilized the history.pushState API to similarly freeze Chrome browsers on shady sites.
This "download bomb" trick only works in Chrome, Segura said. Users landing on the same shady URLs but using other browsers are served different pages.
Also on the front of shady sites pushing malicious content, users should also be aware of sites pushing fake Adobe Flash update packages laced with CPU miners, but also of similar shady sites pretending to provide Mozilla Firefox updates.
GIF image credits: Malwarebytes
Article Source: Scammers Use Download Bombs to Freeze Chrome Browsers on Shady Sites
The trick relies on using JavaScript code loaded on these malicious pages to initiate thousands of file download operations that quickly take up the user's memory resources, freezing Chrome on the scammer's site.
The trick is meant to drive panicked users into calling one of the tech support phone numbers shown on the screen. A GIF of one of these malicious sites freezing a Chrome browser running the latest version (64.0.3282.140) is embedded below.

According to Jérôme Segura —Malwarebytes leading expert in tech support scam operations, malvertising, and exploit kits— this new trick utilizes the JavaScript Blob method and the window.navigator.msSaveOrOpenBlob function to achieve the "download bomb" that freezes Chrome.
The expert says the only way to escape the tech support website is to close Chrome via Windows Task Manager.
When the user restarts Chrome, if Chrome is configured to reload the previous session, Segura advises users to quickly close the shady site while the page is loading and before the malicious code has a chance to execute.
"Download bomb" trick spotted after Google fixed previous trick
Segura says he spotted tech support scammers abusing this new trick after Google engineers patched Chrome against a previous technique that utilized the history.pushState API to similarly freeze Chrome browsers on shady sites.
This "download bomb" trick only works in Chrome, Segura said. Users landing on the same shady URLs but using other browsers are served different pages.
Also on the front of shady sites pushing malicious content, users should also be aware of sites pushing fake Adobe Flash update packages laced with CPU miners, but also of similar shady sites pretending to provide Mozilla Firefox updates.
GIF image credits: Malwarebytes
Article Source: Scammers Use Download Bombs to Freeze Chrome Browsers on Shady Sites

