The overall numbers of malware families employing SSL to protect their C&C server communications have gone up dramatically, a Blue Coat report reveals.
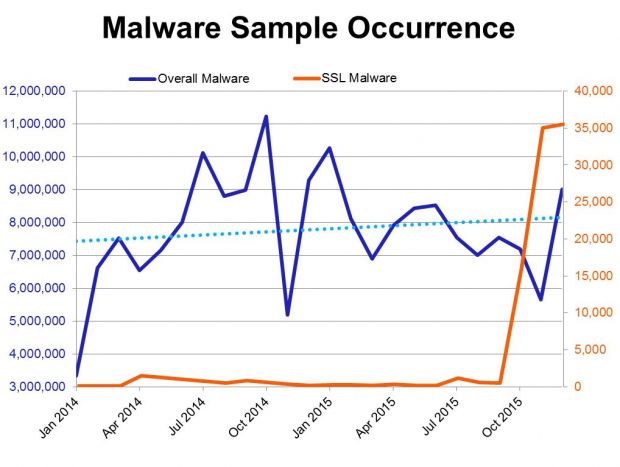
Researchers say that both the number of malware samples detected each month and the total number of active C&C servers are on the rise. For both categories, the security firm claims it observed a huge spike in SSL deployment starting with the end of 2015.
The company explains it analyzed cyber-criminal activity from January 2014 up to December 2015 and used data from the SSL Blacklist site, which keep tracks of abused or bad SSL certificates, often deployed in criminal activities.
The report analyzed detections and the infrastructure of common malware families known to implement SSL to protect themselves. Some of these malware variants included names such as Dridex, KINS, Shylock, URLzone, TeslaCrypt, CryptoLocker, TorrentLocker, CryptoWall, Upatre, Gootkit, Geodo, Tinba, Gozi, VMZeus, Redyms, Vawtrack, Qadars, Spambot, Emotee, and Retefe.
Researchers say that both the number of malware samples detected each month and the total number of active C&C servers are on the rise. For both categories, the security firm claims it observed a huge spike in SSL deployment starting with the end of 2015.
The company explains it analyzed cyber-criminal activity from January 2014 up to December 2015 and used data from the SSL Blacklist site, which keep tracks of abused or bad SSL certificates, often deployed in criminal activities.
The report analyzed detections and the infrastructure of common malware families known to implement SSL to protect themselves. Some of these malware variants included names such as Dridex, KINS, Shylock, URLzone, TeslaCrypt, CryptoLocker, TorrentLocker, CryptoWall, Upatre, Gootkit, Geodo, Tinba, Gozi, VMZeus, Redyms, Vawtrack, Qadars, Spambot, Emotee, and Retefe.
Number of C&C servers using SSL grows 200 times
Researchers discovered that, during the two-year period they analyzed, malware samples, employing SSL or not, both went up.
Malware samples deploying SSL have always been smaller in numbers when compared to the overall number, but something changed in October 2015, when the number of malware using SSL increased manifolds.
Blue Coat researchers saw SSL malware numbers going from 500 samples detected per month to 29,000 in the span of two months.
The same thing happened with the number of C&C servers that used SSL-protected connections to talk to their bots, which jumped from around 1,000 servers in Q1 2015 to 200,000 in Q3 2015.
Blue Coat considered C&C server any website or IP that crooks used as coordination points, malware download sites, data exfiltration points, and other Web-based operations points.
SSL malware recorded a big jump just before the holidays last year
"Looking at the timeframe of the spike, it coincided with the onset of the holiday season. As such, the spike could have been attributed to the launch of one or more large-scale campaigns with infrastructures based on those malware families," Blue Coat researchers noted.
Researchers also pointed out that the number of C&C servers grew well before the malware sample spike, something that is realistic since criminal gangs need to set up their C&C server infrastructure before initiating malware campaigns.
"What’s more, the massive jump in C&C servers is likely attributed to the malware utilizing Domain Generating Algorithms (DGA) for short-living Domains to build out a C&C infrastructure," the Blue Coat team said, explaining the humongous jump in numbers in the case of C&C servers.