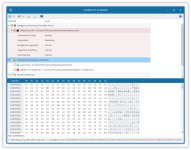
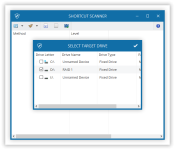
Basically, this application works as a regular Antivirus Scanner: it will scan available attached storage Medias (Fixed Hard Drives and Removable Hard Drives) and lists all existing shortcuts.
For each and every shortcut our application will determine whether or not the shortcut is:
A shortcut is considered 'Broken' if the target application or target folder points to a non-existing location. A broken shortcut is not something we could consider harmful but worth to be removed since the shortcut itself become useless.
A shortcut is considered 'Suspicious' when it contain arguments.
Finally a shortcut is considered 'Dangerous' when multiple flags are triggered.
This method detected 100% of Malicious Shortcuts we used to test the application. It also was totally effective against recent malware and phishing campaigns.
Download Phrozen Software™ - Official Website
For each and every shortcut our application will determine whether or not the shortcut is:
- Broken
- Suspicious
- Dangerous
A shortcut is considered 'Broken' if the target application or target folder points to a non-existing location. A broken shortcut is not something we could consider harmful but worth to be removed since the shortcut itself become useless.
A shortcut is considered 'Suspicious' when it contain arguments.
Most shortcut with arguments could be completely legit, but you should consider taking a look and validate whether or not the shortcut is not calling suspicious applications or parameters. Be careful then when removing them after the scan.
Finally a shortcut is considered 'Dangerous' when multiple flags are triggered.
- If the target application points to a command prompt (Terminal, PowerShell, Ubuntu Bash)
- If it contains dangerous keywords often used to create malicious shortcuts
- An argument overflow, which means that the shortcut command line is more than the Microsoft Windows limitation of 260 characters (MAX PATH)
- Shortcut file size is above 4KiB
- Contains arguments plus one of above flags
This method detected 100% of Malicious Shortcuts we used to test the application. It also was totally effective against recent malware and phishing campaigns.


(!) In a possible future version of this application we might add a pro-active protection to detect shortcuts when they are created and extracted from an archive. If you wish to see this feature added let us know, it will depend our workload and how many users this program will attract.
Download Phrozen Software™ - Official Website
