silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,746
- 123,926
- 8,399
SquirrelWaffle, a new malware loader, is mal-spamming malicious Microsoft Office documents to deliver Qakbot malware and the penetration-testing tool Cobalt Strike – two of the most common threats regularly observed targeting organizations around the world.
Cisco Talos researchers said on Tuesday that they got wind of the malspam campaigns beginning in mid-September, when they saw the boobytrapped Office documents working to infect systems with SquirrelWaffle in the initial stage of the infection chain.
The campaigns are using stolen email threads to come off as replies in those threads, similar to how the virulent Emotet malware – typically spread via malicious emails or text messages – works. “The campaigns themselves feature several similar characteristics to the campaigns previously seen associated with established threats like Emotet,” Cisco Talos researchers explained.
“Due to the prevalence of these campaigns, organizations should be aware of SQUIRRELWAFFLE and the way it could be used by attackers to further compromise corporate networks,” they advised.
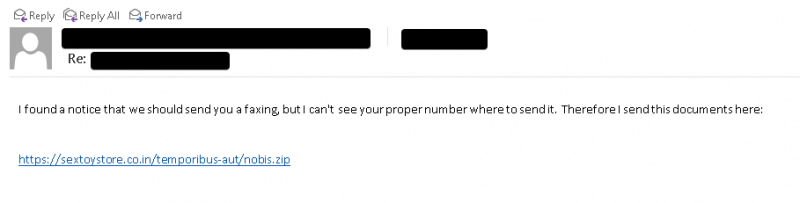
The SquirrelWaffle emails typically contain hyperlinks to malicious ZIP archives being hosted on attacker-controlled web servers, researchers said. An example of one of the malspam emails is shown below.
Most of the messages – 76 percent – are written in English. But the language used in the reply message shifts to match what was used in the original email thread, “demonstrating that there is some localization taking place dynamically,” Cisco Talos said. Besides English, the top five languages being used also include French, German, Dutch and Polish.

SquirrelWaffle Loader Malspams, Packs Qakbot, Cobalt Strike
SquirrelWaffle, a new malware loader, is mal-spamming malicious Microsoft Office documents to deliver Qakbot malware and the penetration-testing tool Cobalt Strike – two of the most common threats regularly observed targeting organizations around the world. Cisco Talos researchers said on...