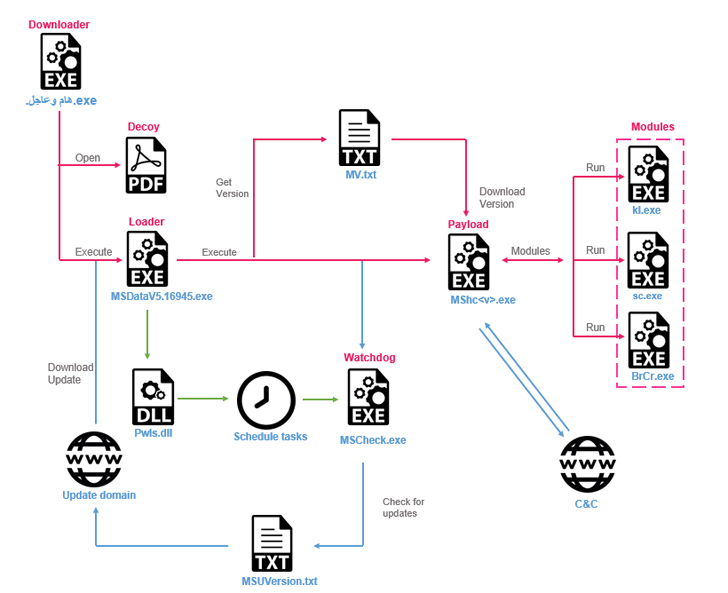
A new custom backdoor dubbed
Stealth Soldier has been deployed as part of a set of highly-targeted espionage attacks in North Africa.
"Stealth Soldier malware is an undocumented backdoor that primarily operates surveillance functions such as file exfiltration, screen and microphone recording, keystroke logging and stealing browser information," cybersecurity company Check Point
said in a technical report.
The ongoing operation is characterized by the use of command-and-control (C&C) servers that mimic sites belonging to the Libyan Ministry of Foreign Affairs. The earliest artifacts associated with the campaign date back to October 2022.
The attacks commence with potential targets downloading bogus downloader binaries that are delivered via social engineering attacks and act as a conduit for retrieving Stealth Soldier, while simultaneously displaying a decoy empty PDF file.
The custom modular implant, which is believed to be used sparingly, enables surveillance capabilities by gathering directory listings and browser credentials, logging keystrokes, recording microphone audio, taking screenshots, uploading files, and running PowerShell commands.