- Sep 22, 2014
- 1,767
Recently a member posted in the forums about a new ransomware that was appending the .surprise extension to encrypted files. When I received the sample, I learned that what I had was an loader that executed a heavily modifiedEDA2 ransomware variant from memory. That was interesting enough, but soon reports started coming in that the those who were infected were being done so via TeamViewer connections.
The first ransomware installed via TeamViewer?
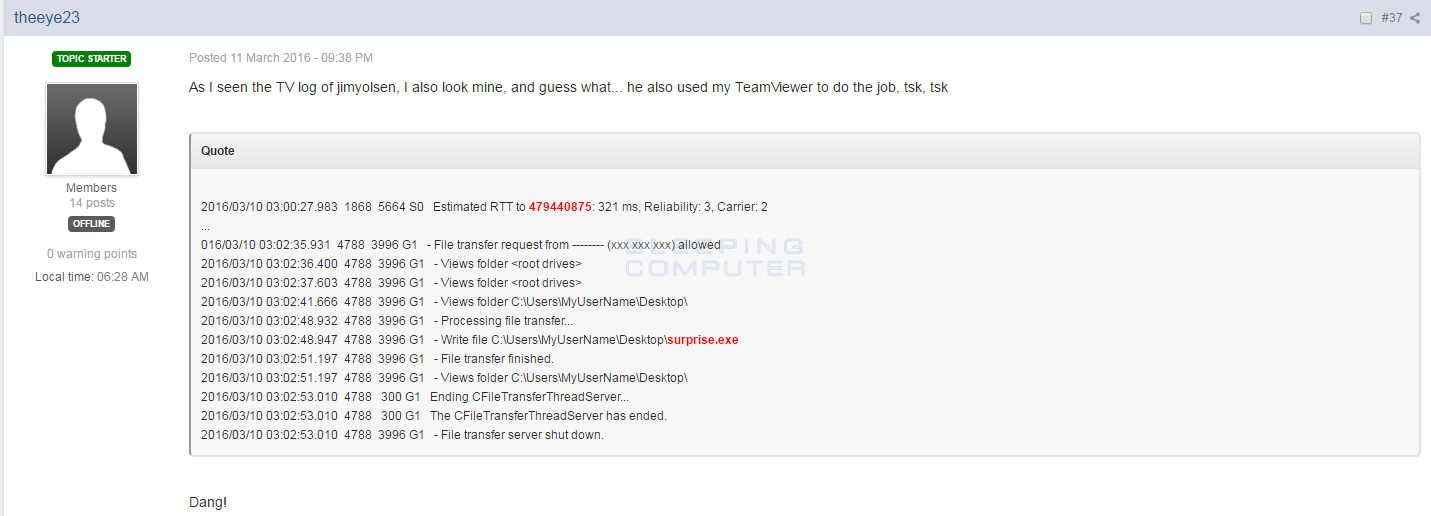
As more reports started to come in from Surprise victims, a disturbing trend was discovered. All of the victim's had TeamViewer installed and logs showed that someone connected to their machine using TeamViewer and uploaded the Surprise.exe files to their desktop.
Post showing a TeamViewer Log
As more logs were posted, it could be seen that there were two TeamViewer IDs that were used by the attackers to upload the ransomware to the computer and execute it. These IDs were 479441239 and 479440875.
Once it was discovered that TeamViewer was involved, I immediately reached out to TeamViewer support to try and get someone who was part of their security team to either call me or email me so we could discuss this attack.Talking to one of the security team members, I was told that the associated IDs have already been disabled so that they could no longer be used on TeamViewer. I was also told, that it appears that the connections made by the ransomware developer were using the credentials of the victim. TeamViewer felt that some of these accounts may have been included in account dumps, where their credentials were retrieved by the ransomware devs.
On checking various databases, I did find that more than half of the victims were listed on theHave I been pwned? Check if your email has been compromised in a data breach site.
At this point, the Surprise ransomware appeared to have gone dark, so we are unable to investigate this further.
Executing from memory to bypass behavior detection
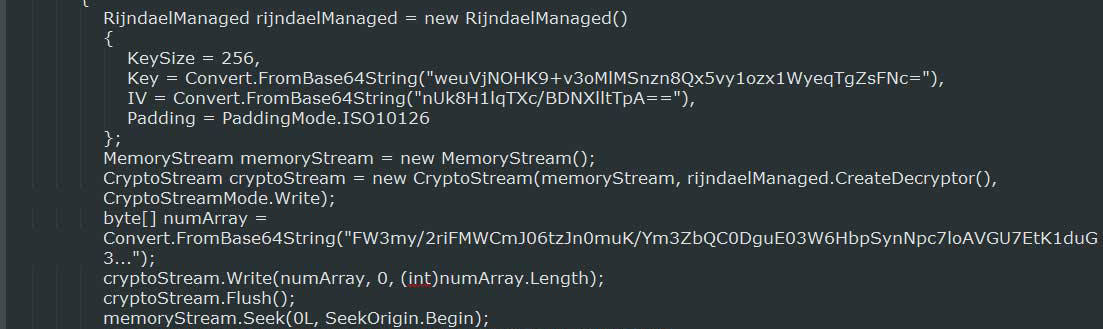
Another interesting characteristic that we saw in the Surprise Ransomware is that the executable itself does not contain any of the encryption functions or other behavior associated with ransomware programs. Instead it contained another executable that transformed into an encrypted BASE64 encoded string. At runtime this string is decrypted, loaded into memory, and then executed directly from there.
This method is being used to not only try to bypass AV signature definitions, but also behavior detection. Behavior detection is becoming the best way to detect and stop ransomware as signature detections have become easily bypassed. By trying to offload the encryption functions, typically targeted by behavior analysis, into an file executed from memory, they are hoping it would not be detected. Thankfully, this is not the case.
Below is some partial source code showing how they are using this technique:
Executing a file from memory
So far this has not helped, as the malicious behavior will still be detected when the ransomware is launched from memory.
The Surprise Ransomware Encryption Process
As already explained, this ransomware is distributed via TeamViewer connections to the victim's computer, which the ransomware developer will use to upload a file called Surprise.exe to the victim's desktop. Once this file is launched, it will decrypt a encrypted BASE64 encoded executable into memory and launch this executable from there.
Once launched, the ransomware will attempt to connect to its Command & Control server where it will send the victim's computer name and username and retrieve a public encryption key. This key will then be used to encrypt a generated AES encryption key, which is then sent back to the Command & Control server.
The ransomware will now begin to scan the all fixed disks on the computer for files that contain a particular file extension. When it finds a matching file, it will encrypt it with the AES encryption key and append the.surprise extension to it. The targeted file extensions are:
.asf, .pdf, .xls, .docx, .xlsx, .mp3, .waw, .jpg, .jpeg, .txt, .rtf, .doc, .rar, .zip, .psd, .tif, .wma, .gif, .bmp, .ppt, .pptx, .docm, .xlsm, .pps, .ppsx, .ppd, .eps, .png, .ace, .djvu, .tar, .cdr, .max, .wmv, .avi, .wav, .mp4, .pdd, .php, .aac, .ac3, .amf, .amr, .dwg, .dxf, .accdb, .mod, .tax2013, .tax2014, .oga, .ogg, .pbf, .ra, .raw, .saf, .val, .wave, .wow, .wpk, .3g2, .3gp, .3gp2, .3mm, .amx, .avs, .bik, .dir, .divx, .dvx, .evo, .flv, .qtq, .tch, .rts, .rum, .rv, .scn, .srt, .stx, .svi, .swf, .trp, .vdo, .wm, .wmd, .wmmp, .wmx, .wvx, .xvid, .3d, .3d4, .3df8, .pbs, .adi, .ais, .amu, .arr, .bmc, .bmf, .cag, .cam, .dng, .ink, .jif, .jiff, .jpc, .jpf, .jpw, .mag, .mic, .mip, .msp, .nav, .ncd, .odc, .odi, .opf, .qif, .xwd, .abw, .act, .adt, .aim, .ans, .asc, .ase, .bdp, .bdr, .bib, .boc, .crd, .diz, .dot, .dotm, .dotx, .dvi, .dxe, .mlx, .err, .euc, .faq, .fdr, .fds, .gthr, .idx, .kwd, .lp2, .ltr, .man, .mbox, .msg, .nfo, .now, .odm, .oft, .pwi, .rng, .rtx, .run, .ssa, .text, .unx, .wbk, .wsh, .7z, .arc, .ari, .arj, .car, .cbr, .cbz, .gz, .gzig, .jgz, .pak, .pcv, .puz, .rev, .sdn, .sen, .sfs, .sfx, .sh, .shar, .shr, .sqx, .tbz2, .tg, .tlz, .vsi, .wad, .war, .xpi, .z02, .z04, .zap, .zipx, .zoo, .ipa, .isu, .jar, .js, .udf, .adr, .ap, .aro, .asa, .ascx, .ashx, .asmx, .asp, .indd, .asr, .qbb, .bml, .cer, .cms, .crt, .dap, .htm, .moz, .svr, .url, .wdgt, .abk, .bic, .big, .blp, .bsp, .cgf, .chk, .col, .cty, .dem, .elf, .ff, .gam, .grf, .h3m, .h4r, .iwd, .ldb, .lgp, .lvl, .map, .md3, .mdl, .nds, .pbp, .ppf, .pwf, .pxp, .sad, .sav, .scm, .scx, .sdt, .spr, .sud, .uax, .umx, .unr, .uop, .usa, .usx, .ut2, .ut3, .utc, .utx, .uvx, .uxx, .vmf, .vtf, .w3g, .w3x, .wtd, .wtf, .ccd, .cd, .cso, .disk, .dmg, .dvd, .fcd, .flp, .img, .isz, .mdf, .mds, .nrg, .nri, .vcd, .vhd, .snp, .bkf, .ade, .adpb, .dic, .cch, .ctt, .dal, .ddc, .ddcx, .dex, .dif, .dii, .itdb, .itl, .kmz, .lcd, .lcf, .mbx, .mdn, .odf, .odp, .ods, .pab, .pkb, .pkh, .pot, .potx, .pptm, .psa, .qdf, .qel, .rgn, .rrt, .rsw, .rte, .sdb, .sdc, .sds, .sql, .stt, .tcx, .thmx, .txd, .txf, .upoi, .vmt, .wks, .wmdb, .xl, .xlc, .xlr, .xlsb, .xltx, .ltm, .xlwx, .mcd, .cap, .cc, .cod, .cp, .cpp, .cs, .csi, .dcp, .dcu, .dev, .dob, .dox, .dpk, .dpl, .dpr, .dsk, .dsp, .eql, .ex, .f90, .fla, .for, .fpp, .jav, .java, .lbi, .owl, .pl, .plc, .pli, .pm, .res, .rsrc, .so, .swd, .tpu, .tpx, .tu, .tur, .vc, .yab, .aip, .amxx, .ape, .api, .mxp, .oxt, .qpx, .qtr, .xla, .xlam, .xll, .xlv, .xpt, .cfg, .cwf, .dbb, .slt, .bp2, .bp3, .bpl, .clr, .dbx, .jc, .potm, .ppsm, .prc, .prt, .shw, .std, .ver, .wpl, .xlm, .yps, .1cd, .bck, .html, .bak, .odt, .pst, .log, .mpg, .mpeg, .odb, .wps, .xlk, .mdb, .dxg, .wpd, .wb2, .dbf, .ai, .3fr, .arw, .srf, .sr2, .bay, .crw, .cr2, .dcr, .kdc, .erf, .mef, .mrw, .nef, .nrw, .orf, .raf, .rwl, .rw2, .r3d, .ptx, .pef, .srw, .x3f, .der, .pem, .pfx, .p12, .p7b, .p7c, .jfif, .exif, .rar
When encrypting files it will skip any files that contain the $ symbol or contain the c:\windows and c:\program strings in the filename.
When the ransomware finishes encrypting the computer, it will create 3 files on the desktop. These files and their contents are:
What happened to your files ?
All of your files were protected by a strong encryption.
There is no way to decrypt your files without the key.
If your files not important for you just reinstall your system.
If your files is important just email us to discuss the price and how to decrypt your files.
You can email us to nowayout@protonmail.com and nowayout@sigaint.org
Write your Email to both email addresses PLS
We accept just BITCOIN if you dont know what it is just google it.
We will give instructions where and how you buy bitcoin in your country.
Price depends on how important your files and network is.it could be 0.5 bitcoin to 25 bitcoin.
You can send us a 1 encrypted file for decryption.
Feel free to email us with your country and computer name and username of the infected system.
Unfortunately, at this time there is no way to decrypt the files encrypted by this infection for free.
Files associated with the Surprise Ransomware
%Desktop%\DECRYPTION_HOWTO.Notepad
%Desktop%\surprise.bat
%Desktop%\Encrypted_Files.Notepad
The first ransomware installed via TeamViewer?
As more reports started to come in from Surprise victims, a disturbing trend was discovered. All of the victim's had TeamViewer installed and logs showed that someone connected to their machine using TeamViewer and uploaded the Surprise.exe files to their desktop.

Post showing a TeamViewer Log
As more logs were posted, it could be seen that there were two TeamViewer IDs that were used by the attackers to upload the ransomware to the computer and execute it. These IDs were 479441239 and 479440875.
Once it was discovered that TeamViewer was involved, I immediately reached out to TeamViewer support to try and get someone who was part of their security team to either call me or email me so we could discuss this attack.Talking to one of the security team members, I was told that the associated IDs have already been disabled so that they could no longer be used on TeamViewer. I was also told, that it appears that the connections made by the ransomware developer were using the credentials of the victim. TeamViewer felt that some of these accounts may have been included in account dumps, where their credentials were retrieved by the ransomware devs.
On checking various databases, I did find that more than half of the victims were listed on theHave I been pwned? Check if your email has been compromised in a data breach site.
At this point, the Surprise ransomware appeared to have gone dark, so we are unable to investigate this further.
Executing from memory to bypass behavior detection
Another interesting characteristic that we saw in the Surprise Ransomware is that the executable itself does not contain any of the encryption functions or other behavior associated with ransomware programs. Instead it contained another executable that transformed into an encrypted BASE64 encoded string. At runtime this string is decrypted, loaded into memory, and then executed directly from there.
This method is being used to not only try to bypass AV signature definitions, but also behavior detection. Behavior detection is becoming the best way to detect and stop ransomware as signature detections have become easily bypassed. By trying to offload the encryption functions, typically targeted by behavior analysis, into an file executed from memory, they are hoping it would not be detected. Thankfully, this is not the case.
Below is some partial source code showing how they are using this technique:

Executing a file from memory
So far this has not helped, as the malicious behavior will still be detected when the ransomware is launched from memory.
The Surprise Ransomware Encryption Process
As already explained, this ransomware is distributed via TeamViewer connections to the victim's computer, which the ransomware developer will use to upload a file called Surprise.exe to the victim's desktop. Once this file is launched, it will decrypt a encrypted BASE64 encoded executable into memory and launch this executable from there.
Once launched, the ransomware will attempt to connect to its Command & Control server where it will send the victim's computer name and username and retrieve a public encryption key. This key will then be used to encrypt a generated AES encryption key, which is then sent back to the Command & Control server.
The ransomware will now begin to scan the all fixed disks on the computer for files that contain a particular file extension. When it finds a matching file, it will encrypt it with the AES encryption key and append the.surprise extension to it. The targeted file extensions are:
.asf, .pdf, .xls, .docx, .xlsx, .mp3, .waw, .jpg, .jpeg, .txt, .rtf, .doc, .rar, .zip, .psd, .tif, .wma, .gif, .bmp, .ppt, .pptx, .docm, .xlsm, .pps, .ppsx, .ppd, .eps, .png, .ace, .djvu, .tar, .cdr, .max, .wmv, .avi, .wav, .mp4, .pdd, .php, .aac, .ac3, .amf, .amr, .dwg, .dxf, .accdb, .mod, .tax2013, .tax2014, .oga, .ogg, .pbf, .ra, .raw, .saf, .val, .wave, .wow, .wpk, .3g2, .3gp, .3gp2, .3mm, .amx, .avs, .bik, .dir, .divx, .dvx, .evo, .flv, .qtq, .tch, .rts, .rum, .rv, .scn, .srt, .stx, .svi, .swf, .trp, .vdo, .wm, .wmd, .wmmp, .wmx, .wvx, .xvid, .3d, .3d4, .3df8, .pbs, .adi, .ais, .amu, .arr, .bmc, .bmf, .cag, .cam, .dng, .ink, .jif, .jiff, .jpc, .jpf, .jpw, .mag, .mic, .mip, .msp, .nav, .ncd, .odc, .odi, .opf, .qif, .xwd, .abw, .act, .adt, .aim, .ans, .asc, .ase, .bdp, .bdr, .bib, .boc, .crd, .diz, .dot, .dotm, .dotx, .dvi, .dxe, .mlx, .err, .euc, .faq, .fdr, .fds, .gthr, .idx, .kwd, .lp2, .ltr, .man, .mbox, .msg, .nfo, .now, .odm, .oft, .pwi, .rng, .rtx, .run, .ssa, .text, .unx, .wbk, .wsh, .7z, .arc, .ari, .arj, .car, .cbr, .cbz, .gz, .gzig, .jgz, .pak, .pcv, .puz, .rev, .sdn, .sen, .sfs, .sfx, .sh, .shar, .shr, .sqx, .tbz2, .tg, .tlz, .vsi, .wad, .war, .xpi, .z02, .z04, .zap, .zipx, .zoo, .ipa, .isu, .jar, .js, .udf, .adr, .ap, .aro, .asa, .ascx, .ashx, .asmx, .asp, .indd, .asr, .qbb, .bml, .cer, .cms, .crt, .dap, .htm, .moz, .svr, .url, .wdgt, .abk, .bic, .big, .blp, .bsp, .cgf, .chk, .col, .cty, .dem, .elf, .ff, .gam, .grf, .h3m, .h4r, .iwd, .ldb, .lgp, .lvl, .map, .md3, .mdl, .nds, .pbp, .ppf, .pwf, .pxp, .sad, .sav, .scm, .scx, .sdt, .spr, .sud, .uax, .umx, .unr, .uop, .usa, .usx, .ut2, .ut3, .utc, .utx, .uvx, .uxx, .vmf, .vtf, .w3g, .w3x, .wtd, .wtf, .ccd, .cd, .cso, .disk, .dmg, .dvd, .fcd, .flp, .img, .isz, .mdf, .mds, .nrg, .nri, .vcd, .vhd, .snp, .bkf, .ade, .adpb, .dic, .cch, .ctt, .dal, .ddc, .ddcx, .dex, .dif, .dii, .itdb, .itl, .kmz, .lcd, .lcf, .mbx, .mdn, .odf, .odp, .ods, .pab, .pkb, .pkh, .pot, .potx, .pptm, .psa, .qdf, .qel, .rgn, .rrt, .rsw, .rte, .sdb, .sdc, .sds, .sql, .stt, .tcx, .thmx, .txd, .txf, .upoi, .vmt, .wks, .wmdb, .xl, .xlc, .xlr, .xlsb, .xltx, .ltm, .xlwx, .mcd, .cap, .cc, .cod, .cp, .cpp, .cs, .csi, .dcp, .dcu, .dev, .dob, .dox, .dpk, .dpl, .dpr, .dsk, .dsp, .eql, .ex, .f90, .fla, .for, .fpp, .jav, .java, .lbi, .owl, .pl, .plc, .pli, .pm, .res, .rsrc, .so, .swd, .tpu, .tpx, .tu, .tur, .vc, .yab, .aip, .amxx, .ape, .api, .mxp, .oxt, .qpx, .qtr, .xla, .xlam, .xll, .xlv, .xpt, .cfg, .cwf, .dbb, .slt, .bp2, .bp3, .bpl, .clr, .dbx, .jc, .potm, .ppsm, .prc, .prt, .shw, .std, .ver, .wpl, .xlm, .yps, .1cd, .bck, .html, .bak, .odt, .pst, .log, .mpg, .mpeg, .odb, .wps, .xlk, .mdb, .dxg, .wpd, .wb2, .dbf, .ai, .3fr, .arw, .srf, .sr2, .bay, .crw, .cr2, .dcr, .kdc, .erf, .mef, .mrw, .nef, .nrw, .orf, .raf, .rwl, .rw2, .r3d, .ptx, .pef, .srw, .x3f, .der, .pem, .pfx, .p12, .p7b, .p7c, .jfif, .exif, .rar
When encrypting files it will skip any files that contain the $ symbol or contain the c:\windows and c:\program strings in the filename.
When the ransomware finishes encrypting the computer, it will create 3 files on the desktop. These files and their contents are:
- %Desktop%\DECRYPTION_HOWTO.Notepad ransom note.
- %Desktop%\surprise.bat, which executes the vssadmin.exe Delete Shadows /All /Quiet to remove Shadow Volume Copies.
- %Desktop%\Encrypted_Files.Notepad file that contains a list of encrypted files
What happened to your files ?
All of your files were protected by a strong encryption.
There is no way to decrypt your files without the key.
If your files not important for you just reinstall your system.
If your files is important just email us to discuss the price and how to decrypt your files.
You can email us to nowayout@protonmail.com and nowayout@sigaint.org
Write your Email to both email addresses PLS
We accept just BITCOIN if you dont know what it is just google it.
We will give instructions where and how you buy bitcoin in your country.
Price depends on how important your files and network is.it could be 0.5 bitcoin to 25 bitcoin.
You can send us a 1 encrypted file for decryption.
Feel free to email us with your country and computer name and username of the infected system.
Unfortunately, at this time there is no way to decrypt the files encrypted by this infection for free.
Files associated with the Surprise Ransomware
%Desktop%\DECRYPTION_HOWTO.Notepad
%Desktop%\surprise.bat
%Desktop%\Encrypted_Files.Notepad
