HitMan pro detect SVChost.exe detected as suspicious. under C:\WINDOWS\system32\svchost.exe
Product . . . . . : Microsoft® Windows® Operating System
Publisher . . . . : Microsoft Corporation
Description . . . : Host Process for Windows Services
Version . . . . . : 10.0.14393.0
Copyright . . . . : © Microsoft Corporation. All rights reserved.
RSA Key Size . . . : 2048
Process Type . . . : Critical
LanguageID . . . . : 1033
Authenticode . . . : Valid.
Should I delete It.
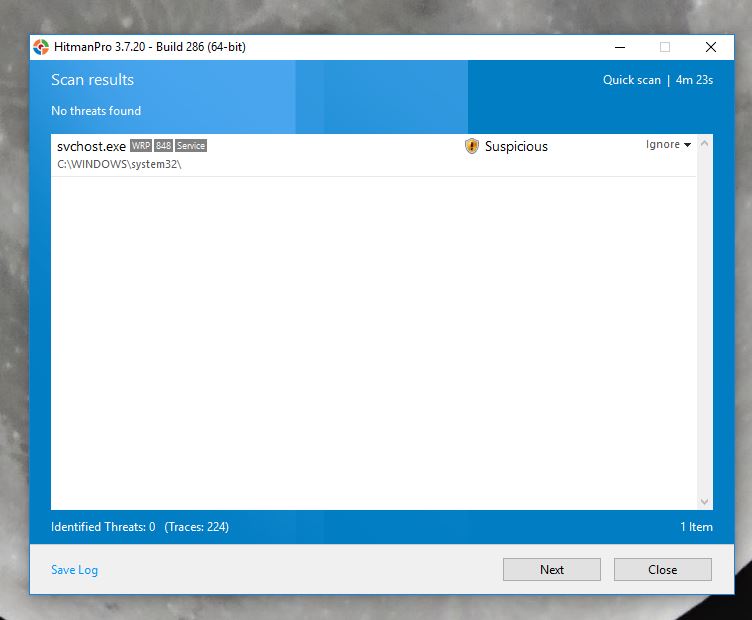
Product . . . . . : Microsoft® Windows® Operating System
Publisher . . . . : Microsoft Corporation
Description . . . : Host Process for Windows Services
Version . . . . . : 10.0.14393.0
Copyright . . . . : © Microsoft Corporation. All rights reserved.
RSA Key Size . . . : 2048
Process Type . . . : Critical
LanguageID . . . . : 1033
Authenticode . . . : Valid.
Should I delete It.