- Sep 22, 2014
- 1,767
A ransomware called Cerber has been floating around for about a week, but we were not able to retrieve a sample until today. Thanks to @BiebsMalwareGuy and @MeegulWorth, samples were found and further analysis of the ransomware could be done. When infected, a victim's data files will be encrypted using AES encryption and will be told they need to pay a ransom of 1.24 bitcoins or ~500 USD to get their files back. Unfortunately, at this point there is no known way to decrypt a victim's encrypted files for free.
At this time we do not currently know how the Cerber ransomware is being distributed, but according to SenseCy, it is being offered as a service on a closed underground Russian forum. This means that it is probably a new Ransomware as a Service, or RaaS, where affiliates can join in order to distribute the ransomware, while the Cerber developers earn a commission from each ransom payment.
For anyone who is infected with this ransomware or wants to discuss the infection, we have a dedicated support topic here: CERBER Ransomware Support and Help Topic.
The Cerber Encryption Process
When first run, Cerber will check to see if the victim is from a particular country. If the computer appears to be from any of the following countries, it will terminate itself and not encrypt the computer.
Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, Uzbekistan
If the victim is not from one of the above countries, Cerber will install itself in the %AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\ folder and name itself after a random Windows executable. For example, when we performed our analysis of the ransomware it named itself autochk.exe. It will then configure Windows to automatically boot into Safe Mode with Networking on the next reboot using the following command:
C:\Windows\System32\bcdedit.exe" /set {current} safeboot network
Cerber will then configure itself itself to start automatically when you login to windows, execute as your screensaver when your computer is idle, and set a task to execute itself once every minute. In this phase, when the ransomware is executed it will show a fake system alert and begin a restart process. Until this restart is allowed to occur, it will continue to display fake system alerts. Examples of alerts you may see include:
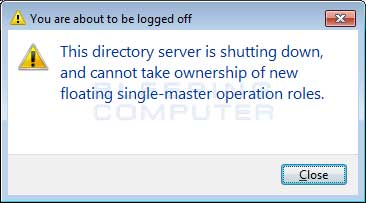
Shutdown Alert
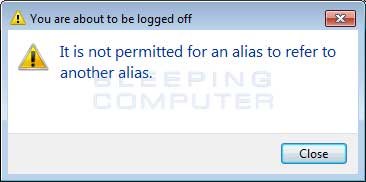
Shutdown Alert
For some unknown reason, the computer will then reboot into Safe Mode with Networking and once you login, will automatically shutdown again and reboot back into normal mode. Once it is booted into regular mode, the ransomware will execute and begin the encryption process of the victim's computer.
Thanks to Hasherazade's analysis of the ransomware, it was discovered that Cerber uses a JSON configuration filefor its settings when executed. This config file details what extensions to encrypt, what countries should not be encrypted, what files and folders to not encrypt, and various other configuration information.
When encrypting your data, Cerber will scan the victim's drive letters for any files that match certain file extensions. When it finds a matching data file, it will encrypt the file using AES-256 encryption, encrypt the file's name, and then add the .CERBER extension to it. As an example, the unencrypted file called test.doc may be renamed as Zu0ITC4HoQ.cerber after it has been encrypted. The currently targeted file extensions are:
.contact, .dbx, .doc, .docx, .jnt, .jpg, .mapimail, .msg, .oab, .ods, .pdf, .pps, .ppsm, .ppt, .pptm, .prf, .pst, .rar, .rtf, .txt, .wab, .xls, .xlsx, .xml, .zip, .1cd, .3ds, .3g2, .3gp, .7z, .7zip, .accdb, .aoi, .asf, .asp, .aspx, .asx, .avi, .bak, .cer, .cfg, .class, .config, .css, .csv, .db, .dds, .dwg, .dxf, .flf, .flv, .html, .idx, .js, .key, .kwm, .laccdb, .ldf, .lit, .m3u, .mbx, .md, .mdf, .mid, .mlb, .mov, .mp3, .mp4, .mpg, .obj, .odt, .pages, .php, .psd, .pwm, .rm, .safe, .sav, .save, .sql, .srt, .swf, .thm, .vob, .wav, .wma, .wmv, .xlsb, .3dm, .aac, .ai, .arw, .c, .cdr, .cls, .cpi, .cpp, .cs, .db3, .docm, .dot, .dotm, .dotx, .drw, .dxb, .eps, .fla, .flac, .fxg, .java, .m, .m4v, .max, .mdb, .pcd, .pct, .pl, .potm, .potx, .ppam, .ppsm, .ppsx, .pptm, .ps, .pspimage, .r3d, .rw2, .sldm, .sldx, .svg, .tga, .wps, .xla, .xlam, .xlm, .xlr, .xlsm, .xlt, .xltm, .xltx, .xlw, .act, .adp, .al, .bkp, .blend, .cdf, .cdx, .cgm, .cr2, .crt, .dac, .dbf, .dcr, .ddd, .design, .dtd, .fdb, .fff, .fpx, .h, .iif, .indd, .jpeg, .mos, .nd, .nsd, .nsf, .nsg, .nsh, .odc, .odp, .oil, .pas, .pat, .pef, .pfx, .ptx, .qbb, .qbm, .sas7bdat, .say, .st4, .st6, .stc, .sxc, .sxw, .tlg, .wad, .xlk, .aiff, .bin, .bmp, .cmt, .dat, .dit, .edb, .flvv, .gif, .groups, .hdd, .hpp, .log, .m2ts, .m4p, .mkv, .mpeg, .ndf, .nvram, .ogg, .ost, .pab, .pdb, .pif, .png, .qed, .qcow, .qcow2, .rvt, .st7, .stm, .vbox, .vdi, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .3fr, .3pr, .ab4, .accde, .accdr, .accdt, .ach, .acr, .adb, .ads, .agdl, .ait, .apj, .asm, .awg, .back, .backup, .backupdb, .bank, .bay, .bdb, .bgt, .bik, .bpw, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .ce1, .ce2, .cib, .craw, .crw, .csh, .csl, .db_journal, .dc2, .dcs, .ddoc, .ddrw, .der, .des, .dgc, .djvu, .dng, .drf, .dxg, .eml, .erbsql, .erf, .exf, .ffd, .fh, .fhd, .gray, .grey, .gry, .hbk, .ibank, .ibd, .ibz, .iiq, .incpas, .jpe, .kc2, .kdbx, .kdc, .kpdx, .lua, .mdc, .mef, .mfw, .mmw, .mny, .moneywell, .mrw, .myd, .ndd, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nwb, .nx2, .nxl, .nyf, .odb, .odf, .odg, .odm, .orf, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pdd, .pem, .plus_muhd, .plc, .pot, .pptx, .psafe3, .py, .qba, .qbr, .qbw, .qbx, .qby, .raf, .rat, .raw, .rdb, .rwl, .rwz, .s3db, .sd0, .sda, .sdf, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srw, .st5, .st8, .std, .sti, .stw, .stx, .sxd, .sxg, .sxi, .sxm, .tex, .wallet, .wb2, .wpd, .x11, .x3f, .xis, .ycbcra, .yuv
When searching for files to encrypt, Cerber will skip files that are named bootsect.bak, iconcache.db, thumbs.db, or wallet.dat or whose full pathname include the following strings:
:\$recycle.bin\
:\$windows.~bt\
:\boot\
:\drivers\
:\program files\
:\program files (x86)\
:\programdata\
:\users\all users\
:\windows\
\appdata\local\
\appdata\locallow\
\appdata\roaming\
\public\music\sample music\
\public\pictures\sample pictures\
\public\videos\sample videos\
\tor browser\
Furthermore, Cerber contains the ability to scan for and enumerate unmapped Windows shares and encrypt any data that is found on them. If the network setting is set to 1 in the configuration file, then Cerber will search for and encrypt any accessible network shares on your network, even if those shares are not mapped to the computer.
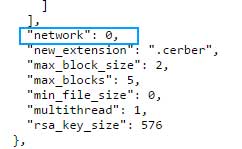
Network Setting
At this time, though this feature appears to be turned off in the configuration file, It is important for all system administrators to harden the security of their network shares as this feature is starting to become common in newer ransomware.
Last, but not least, Cerber will create 3 ransom notes on your desktop as well as in every folder that is encrypted. These files are called # DECRYPT MY FILES #.html, # DECRYPT MY FILES #.txt, and # DECRYPT MY FILES #.vbs. These ransom notes contain instructions on what has happened to your data and contain links to the Tor decryption service where you can make the ransom payment and retrieve the decryptor.
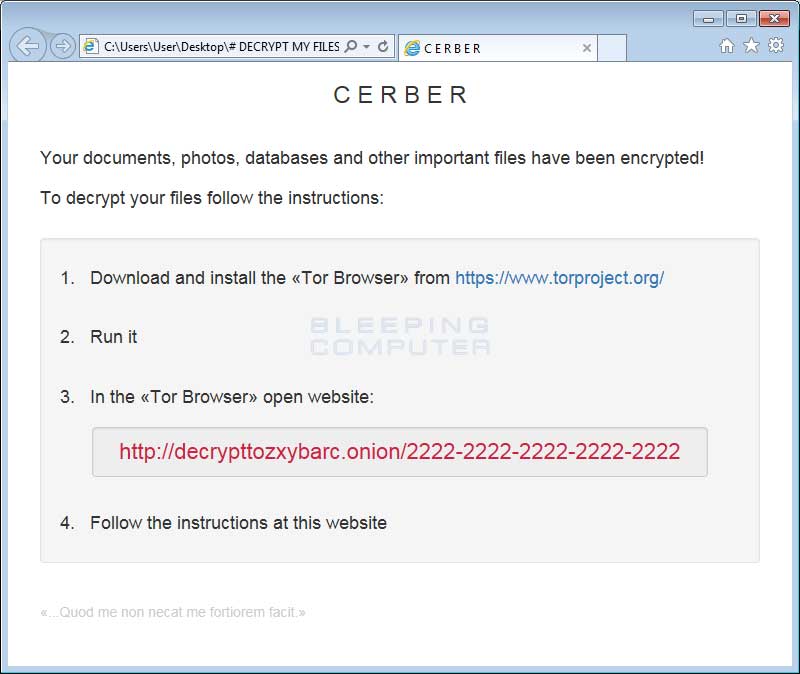
Cerber Ransom Note
At the bottom of each ransom note contains the Latin quote:
.Quod me non necat me fortiorem facit
- Cerber Ransom Note
In English, this translates to "That which does not kill me makes me stronger", which I am sure all of the victims appreciate.
To upset a victim even more, Cerber talks to you!
Once of the ransom notes that Cerber creates is a bit more "special" then the others. The # DECRYPT MY FILES #.vbs file contains VBScript, which will cause the victim's computer to speak to them.
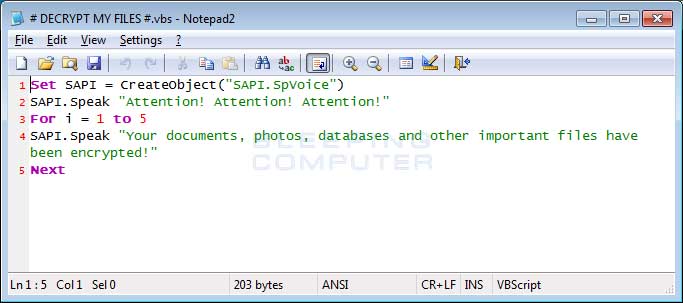
VBS Script
When the above script is executed, your computer will speak a message stating that your computer's files were encrypted and will repeat itself numerous times. This message can be listened to below:
here.
Once a victim makes a payment to the listed bitcoin address, their payment will be shown in the Payment History section of the decryptor page. After a certain amount of bitcoin transaction confirmations, this page will then provide a download link for the victim's unique decryptor.
As already said, unfortunately there is no way to decrypt your files for free. If you are a victim of this ransomware then your best option is to restore your files from a backup. For anyone who is infected with this ransomware or wants to discuss the infection, we have a dedicated support topic here: CERBER Ransomware Support and Help Topic.
Files associated with Cerber Ransomware
HKCU\Control Panel\Desktop\SCRNSAVE.EXE "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Command Processor\AutoRun "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\[random] "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\[random] "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
Registry entries associated with Cerber Ransomware
"%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
SOURCE
At this time we do not currently know how the Cerber ransomware is being distributed, but according to SenseCy, it is being offered as a service on a closed underground Russian forum. This means that it is probably a new Ransomware as a Service, or RaaS, where affiliates can join in order to distribute the ransomware, while the Cerber developers earn a commission from each ransom payment.
For anyone who is infected with this ransomware or wants to discuss the infection, we have a dedicated support topic here: CERBER Ransomware Support and Help Topic.
The Cerber Encryption Process
When first run, Cerber will check to see if the victim is from a particular country. If the computer appears to be from any of the following countries, it will terminate itself and not encrypt the computer.
Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, Uzbekistan
If the victim is not from one of the above countries, Cerber will install itself in the %AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\ folder and name itself after a random Windows executable. For example, when we performed our analysis of the ransomware it named itself autochk.exe. It will then configure Windows to automatically boot into Safe Mode with Networking on the next reboot using the following command:
C:\Windows\System32\bcdedit.exe" /set {current} safeboot network
Cerber will then configure itself itself to start automatically when you login to windows, execute as your screensaver when your computer is idle, and set a task to execute itself once every minute. In this phase, when the ransomware is executed it will show a fake system alert and begin a restart process. Until this restart is allowed to occur, it will continue to display fake system alerts. Examples of alerts you may see include:

Shutdown Alert

Shutdown Alert
For some unknown reason, the computer will then reboot into Safe Mode with Networking and once you login, will automatically shutdown again and reboot back into normal mode. Once it is booted into regular mode, the ransomware will execute and begin the encryption process of the victim's computer.
Thanks to Hasherazade's analysis of the ransomware, it was discovered that Cerber uses a JSON configuration filefor its settings when executed. This config file details what extensions to encrypt, what countries should not be encrypted, what files and folders to not encrypt, and various other configuration information.
When encrypting your data, Cerber will scan the victim's drive letters for any files that match certain file extensions. When it finds a matching data file, it will encrypt the file using AES-256 encryption, encrypt the file's name, and then add the .CERBER extension to it. As an example, the unencrypted file called test.doc may be renamed as Zu0ITC4HoQ.cerber after it has been encrypted. The currently targeted file extensions are:
.contact, .dbx, .doc, .docx, .jnt, .jpg, .mapimail, .msg, .oab, .ods, .pdf, .pps, .ppsm, .ppt, .pptm, .prf, .pst, .rar, .rtf, .txt, .wab, .xls, .xlsx, .xml, .zip, .1cd, .3ds, .3g2, .3gp, .7z, .7zip, .accdb, .aoi, .asf, .asp, .aspx, .asx, .avi, .bak, .cer, .cfg, .class, .config, .css, .csv, .db, .dds, .dwg, .dxf, .flf, .flv, .html, .idx, .js, .key, .kwm, .laccdb, .ldf, .lit, .m3u, .mbx, .md, .mdf, .mid, .mlb, .mov, .mp3, .mp4, .mpg, .obj, .odt, .pages, .php, .psd, .pwm, .rm, .safe, .sav, .save, .sql, .srt, .swf, .thm, .vob, .wav, .wma, .wmv, .xlsb, .3dm, .aac, .ai, .arw, .c, .cdr, .cls, .cpi, .cpp, .cs, .db3, .docm, .dot, .dotm, .dotx, .drw, .dxb, .eps, .fla, .flac, .fxg, .java, .m, .m4v, .max, .mdb, .pcd, .pct, .pl, .potm, .potx, .ppam, .ppsm, .ppsx, .pptm, .ps, .pspimage, .r3d, .rw2, .sldm, .sldx, .svg, .tga, .wps, .xla, .xlam, .xlm, .xlr, .xlsm, .xlt, .xltm, .xltx, .xlw, .act, .adp, .al, .bkp, .blend, .cdf, .cdx, .cgm, .cr2, .crt, .dac, .dbf, .dcr, .ddd, .design, .dtd, .fdb, .fff, .fpx, .h, .iif, .indd, .jpeg, .mos, .nd, .nsd, .nsf, .nsg, .nsh, .odc, .odp, .oil, .pas, .pat, .pef, .pfx, .ptx, .qbb, .qbm, .sas7bdat, .say, .st4, .st6, .stc, .sxc, .sxw, .tlg, .wad, .xlk, .aiff, .bin, .bmp, .cmt, .dat, .dit, .edb, .flvv, .gif, .groups, .hdd, .hpp, .log, .m2ts, .m4p, .mkv, .mpeg, .ndf, .nvram, .ogg, .ost, .pab, .pdb, .pif, .png, .qed, .qcow, .qcow2, .rvt, .st7, .stm, .vbox, .vdi, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .3fr, .3pr, .ab4, .accde, .accdr, .accdt, .ach, .acr, .adb, .ads, .agdl, .ait, .apj, .asm, .awg, .back, .backup, .backupdb, .bank, .bay, .bdb, .bgt, .bik, .bpw, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .ce1, .ce2, .cib, .craw, .crw, .csh, .csl, .db_journal, .dc2, .dcs, .ddoc, .ddrw, .der, .des, .dgc, .djvu, .dng, .drf, .dxg, .eml, .erbsql, .erf, .exf, .ffd, .fh, .fhd, .gray, .grey, .gry, .hbk, .ibank, .ibd, .ibz, .iiq, .incpas, .jpe, .kc2, .kdbx, .kdc, .kpdx, .lua, .mdc, .mef, .mfw, .mmw, .mny, .moneywell, .mrw, .myd, .ndd, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nwb, .nx2, .nxl, .nyf, .odb, .odf, .odg, .odm, .orf, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pdd, .pem, .plus_muhd, .plc, .pot, .pptx, .psafe3, .py, .qba, .qbr, .qbw, .qbx, .qby, .raf, .rat, .raw, .rdb, .rwl, .rwz, .s3db, .sd0, .sda, .sdf, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srw, .st5, .st8, .std, .sti, .stw, .stx, .sxd, .sxg, .sxi, .sxm, .tex, .wallet, .wb2, .wpd, .x11, .x3f, .xis, .ycbcra, .yuv
When searching for files to encrypt, Cerber will skip files that are named bootsect.bak, iconcache.db, thumbs.db, or wallet.dat or whose full pathname include the following strings:
:\$recycle.bin\
:\$windows.~bt\
:\boot\
:\drivers\
:\program files\
:\program files (x86)\
:\programdata\
:\users\all users\
:\windows\
\appdata\local\
\appdata\locallow\
\appdata\roaming\
\public\music\sample music\
\public\pictures\sample pictures\
\public\videos\sample videos\
\tor browser\
Furthermore, Cerber contains the ability to scan for and enumerate unmapped Windows shares and encrypt any data that is found on them. If the network setting is set to 1 in the configuration file, then Cerber will search for and encrypt any accessible network shares on your network, even if those shares are not mapped to the computer.

Network Setting
At this time, though this feature appears to be turned off in the configuration file, It is important for all system administrators to harden the security of their network shares as this feature is starting to become common in newer ransomware.
Last, but not least, Cerber will create 3 ransom notes on your desktop as well as in every folder that is encrypted. These files are called # DECRYPT MY FILES #.html, # DECRYPT MY FILES #.txt, and # DECRYPT MY FILES #.vbs. These ransom notes contain instructions on what has happened to your data and contain links to the Tor decryption service where you can make the ransom payment and retrieve the decryptor.

Cerber Ransom Note
At the bottom of each ransom note contains the Latin quote:
.Quod me non necat me fortiorem facit
- Cerber Ransom Note
In English, this translates to "That which does not kill me makes me stronger", which I am sure all of the victims appreciate.
To upset a victim even more, Cerber talks to you!
Once of the ransom notes that Cerber creates is a bit more "special" then the others. The # DECRYPT MY FILES #.vbs file contains VBScript, which will cause the victim's computer to speak to them.

VBS Script
When the above script is executed, your computer will speak a message stating that your computer's files were encrypted and will repeat itself numerous times. This message can be listened to below:
here.
Once a victim makes a payment to the listed bitcoin address, their payment will be shown in the Payment History section of the decryptor page. After a certain amount of bitcoin transaction confirmations, this page will then provide a download link for the victim's unique decryptor.
As already said, unfortunately there is no way to decrypt your files for free. If you are a victim of this ransomware then your best option is to restore your files from a backup. For anyone who is infected with this ransomware or wants to discuss the infection, we have a dedicated support topic here: CERBER Ransomware Support and Help Topic.
Files associated with Cerber Ransomware
HKCU\Control Panel\Desktop\SCRNSAVE.EXE "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Command Processor\AutoRun "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\[random] "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\[random] "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
Registry entries associated with Cerber Ransomware
"%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
SOURCE
Last edited by a moderator: