The Rex Linux malware is not as widespread and efficient as initially thought, and currently, the multi-featured Rex malware is only in command of a tiny botnet of around 150 devices.
Discovered this May, researchers initially thought this malware was a ransomware that exploited vulnerable Drupal sites to encrypt their files and ask for a ransom fee.
A later analysis released over the summer showed that the malware behind those initial infections also had many features such as the ability to launch DDoS attacks, mine for crypto-currency, talk to fellow Rex bots via the DHT P2P protocol, and self-propagate to other devices on its own.
Rex used for DDoS extortion schemes
Researchers said that the group behind this trojan used the malware more as a penetration tool, rather than a DDoS botnet. They leveraged its ability to propagate to Linux-based devices using exploits in Drupal, WordPress, and Magento sites, but also applications such as Exagrid, Apache Jetspeed, and AirOS home routers.
Once they infected these targets, the crooks would send the webmaster an email, threatening with DDoS attacks. In these emails, the Rex gang tried to pose as the infamous Armada Collective, reminiscent of a popular DDoS-for-Bitcoin extortion tactic also discovered by CloudFlare earlier in the year.
Discovered this May, researchers initially thought this malware was a ransomware that exploited vulnerable Drupal sites to encrypt their files and ask for a ransom fee.
A later analysis released over the summer showed that the malware behind those initial infections also had many features such as the ability to launch DDoS attacks, mine for crypto-currency, talk to fellow Rex bots via the DHT P2P protocol, and self-propagate to other devices on its own.
Rex used for DDoS extortion schemes
Researchers said that the group behind this trojan used the malware more as a penetration tool, rather than a DDoS botnet. They leveraged its ability to propagate to Linux-based devices using exploits in Drupal, WordPress, and Magento sites, but also applications such as Exagrid, Apache Jetspeed, and AirOS home routers.
Once they infected these targets, the crooks would send the webmaster an email, threatening with DDoS attacks. In these emails, the Rex gang tried to pose as the infamous Armada Collective, reminiscent of a popular DDoS-for-Bitcoin extortion tactic also discovered by CloudFlare earlier in the year.
French researcher Benkow, of Stormshield Security, the man who analyzed the malware over the summer, has continued to track its activity.
In a recent update on his Rex research, the security expert says that the Rex group has continued its DDoS extortion business, but in recent emails, they're now masquerading as members of the Anonymous hacker collective.
Rex incorporates Mirai features
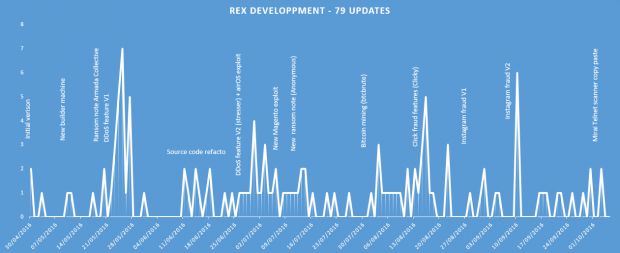
Additionally, he also says that the malware's evolution has continued, with the group behind it adding new features.
Rex malware feature evolution
The most notable change he detected was source code borrowed from the Mirai malware, the malware responsible for today's most devastating DDoS attacks, on targets such as French ISP OVH, managed DNS provider Dyn, and the site of journalist Brian Krebs.
Rex's authors have taken the recently leaked Mirai source code and have added some of its components to their trojan.
Rex's Mirai integration fails spectacularly
Benkow points out that initially, the Rex group ported the Mirai component that scans for vulnerable devices and brute-forces their Telnet port.
This experiment didn't go as well as the Rex gang had hoped. Benkow, who tracked Rex's evolution, says the Rex variant that included the Mirai Telnet scanner was very buggy, and only managed to infect around ten devices before the Rex gang decided to scrape it and implement Mirai's SSH scanner instead.
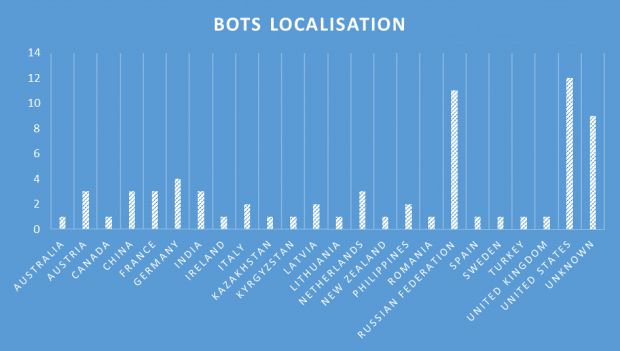
Despite the effort put into porting features from a more successful IoT/Linux malware, Rex failed to match Mirai's capabilities, and according to his data, Benkow says that at the moment, the Rex P2P botnet only has around 150 bots, a laughable botnet statistic for a group that threatens companies with DDoS attacks.
Because of these and many other coding snafus, Benkow is not convinced that Rex is the threat that he believed to be in August, when he released his first research.
"Regarding how the bot master uses this botnet, we can easily conclude that it may not be part of a big cyber gang, Rex Botnet looks more like an experimental botnet," the researcher said.