- Jul 22, 2014
- 2,525
Over 1 million Internet of Things (IoT) devices have been compromised in recent months and added to DDoS botnets created with the help of a malware family known as Gafgyt, but also as Lizkebab, BASHLITE, and Torlus.
You may also know the malware as LizardStresser, the name of the DDoS toolkit that the infamous Lizard Squad hacking crew developed for their botnet, and later released online.
The impact of this decision has had serious repercussions on the DDoS landscape. At the end of June, network security vendor Arbor Networks revealed it identified over 100 DDoS botnets built using this toolkit.
Over 1 million IoT devices currently compromised
According to recent research released by Level 3 in collaboration with Flashpoint, this tool has now compromised over one million IoT devices.
These IoT gadgets represent 96 percent of the total number of Gafgyt bots involved in recent DDoS attacks.
The vast majority of these IoT devices, 95 percent according to Level 3, are DVR devices and IP cameras. Only 4 percent are home routers and 1 percent Linux web servers.
DVR systems are the favorite targets
Level 3 says that white-label DVRs manufactured by Dahua Technology were the most commonly infected devices.
DVRs are one of the favorite devices to compromise with DDoS bots. At the end of June, web security vendor Sucuri discovered a 25,000-strong botnet of DVRs and CCTV systems that were using TVT hardware. This botnet had been created by a different malware, much more sophisticated than Gafgyt.
Gafgyt, which is coded in C, is a relatively simplistic bot. Gafgyt botnets can only launch UDP and TCP floods, don't support reflection DDoS attacks, and use a simplistic C&C server structure.
Level 3 says it is very easy to take down Gafgyt botnets just by seizing their central command and control server. Nevertheless, since botnets are created by brute-forcing devices using their default credentials, attackers can re-infect the devices and build a new botnet in a few hours or days.
Botnet of 120,000 devices observed online
According to telemetry data gathered by watching Gafgyt botnets, C&C servers usually live for around 13 days. The largest botnet discovered by Level 3's team contained 120,000 bots.
Threat actors don't need huge bot numbers to launch potent attacks. A medium botnet of just a few thousand clients is able to launch DDoS attacks of hundreds of Gbps.
Because most of the bots are infected IP cameras and DVRs, these devices tend to have large bandwidth connections in order to relay video feeds, which also ensures crooks have big DDoS cannons at their disposal.
Botnets target devices running Linux-based firmware
The simplicity of these botnets also shows when you realize that crooks control them via IRC channels. Gafgyt bots connect to a private IRC chat room, where the crook posts instructions as chat messages. All bots connected to the chat room read the message and execute it.
Gafgyt bots are one of the main contributors to the underground world of DDoS-for-hire services.
Because Gafgyt bots target IoT devices running a stripped-down version of the Linux OS, specifically modified to work with low resources, running security software on these devices is out of the question. Protecting devices against infection falls on users, who almost always fail miserably.
Security experts recommend that owners change the default credentials of their IoT devices, place them on private networks, accessible via VPNs, or behind a firewall that's able to block unknown users from reaching their management and authentication ports.
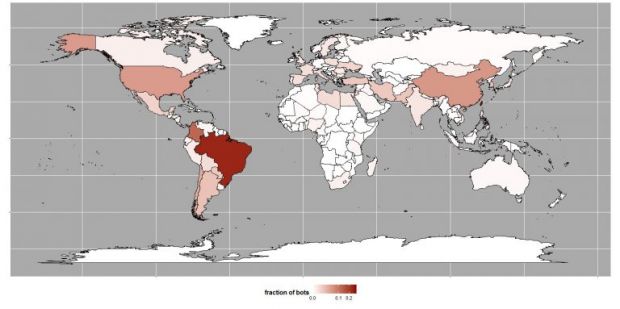
Geographical distribution of Gafgyt bots
You may also know the malware as LizardStresser, the name of the DDoS toolkit that the infamous Lizard Squad hacking crew developed for their botnet, and later released online.
The impact of this decision has had serious repercussions on the DDoS landscape. At the end of June, network security vendor Arbor Networks revealed it identified over 100 DDoS botnets built using this toolkit.
Over 1 million IoT devices currently compromised
According to recent research released by Level 3 in collaboration with Flashpoint, this tool has now compromised over one million IoT devices.
These IoT gadgets represent 96 percent of the total number of Gafgyt bots involved in recent DDoS attacks.
The vast majority of these IoT devices, 95 percent according to Level 3, are DVR devices and IP cameras. Only 4 percent are home routers and 1 percent Linux web servers.
DVR systems are the favorite targets
Level 3 says that white-label DVRs manufactured by Dahua Technology were the most commonly infected devices.
DVRs are one of the favorite devices to compromise with DDoS bots. At the end of June, web security vendor Sucuri discovered a 25,000-strong botnet of DVRs and CCTV systems that were using TVT hardware. This botnet had been created by a different malware, much more sophisticated than Gafgyt.
Gafgyt, which is coded in C, is a relatively simplistic bot. Gafgyt botnets can only launch UDP and TCP floods, don't support reflection DDoS attacks, and use a simplistic C&C server structure.
Level 3 says it is very easy to take down Gafgyt botnets just by seizing their central command and control server. Nevertheless, since botnets are created by brute-forcing devices using their default credentials, attackers can re-infect the devices and build a new botnet in a few hours or days.
Botnet of 120,000 devices observed online
According to telemetry data gathered by watching Gafgyt botnets, C&C servers usually live for around 13 days. The largest botnet discovered by Level 3's team contained 120,000 bots.
Threat actors don't need huge bot numbers to launch potent attacks. A medium botnet of just a few thousand clients is able to launch DDoS attacks of hundreds of Gbps.
Because most of the bots are infected IP cameras and DVRs, these devices tend to have large bandwidth connections in order to relay video feeds, which also ensures crooks have big DDoS cannons at their disposal.
Botnets target devices running Linux-based firmware
The simplicity of these botnets also shows when you realize that crooks control them via IRC channels. Gafgyt bots connect to a private IRC chat room, where the crook posts instructions as chat messages. All bots connected to the chat room read the message and execute it.
Gafgyt bots are one of the main contributors to the underground world of DDoS-for-hire services.
Because Gafgyt bots target IoT devices running a stripped-down version of the Linux OS, specifically modified to work with low resources, running security software on these devices is out of the question. Protecting devices against infection falls on users, who almost always fail miserably.
Security experts recommend that owners change the default credentials of their IoT devices, place them on private networks, accessible via VPNs, or behind a firewall that's able to block unknown users from reaching their management and authentication ports.

Geographical distribution of Gafgyt bots
