- Jul 27, 2015
- 5,458
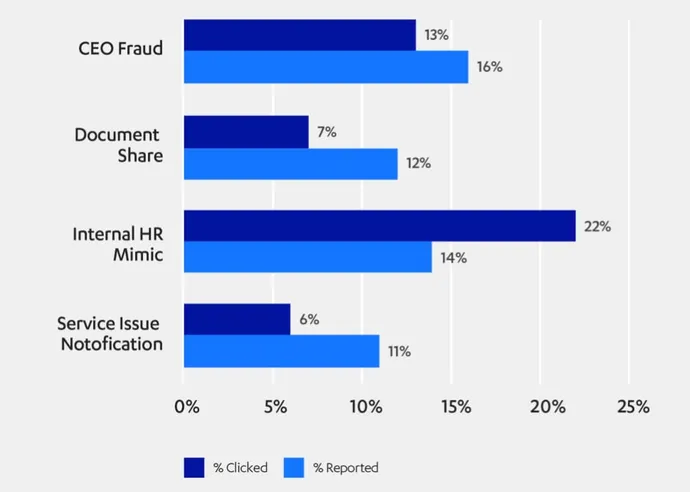
Quote : " There is a lot of received wisdom in the security industry about email phishing, wisdom that F-Secure wanted to challenge with hard data. To do so, we conducted a study, targeting 82,402 individuals from four organizations with one of four phishing emails. We recorded if they were susceptible (clicking on our links), asked those clickers some questions then interpreted the results.
The results of the study reinforced some classical thinking – no one will be surprised that the mock internal HR email threatening annual leave was the most effective – however, some results might challenge industry intuition. The most striking of these results is that those employed in IT related roles were just as susceptible as those in the rest of the business.
Two of the organizations we targeted had employees in departments described as IT and DevOps; roles which focus on computer technology. In one of these organizations those ‘technical’ departments were just as susceptible to our emails as the rest of the business (26% clicking in DevOps, 24% in IT and 25% across the organization overall). The other organization, however, saw these technical departments show far higher susceptibility than the organizational average (30% clicking in DevOps, 21% in IT, with the overall rate for the organization being 11%). Similarly, these groups were no better than the rest of the organization at reporting the emails as suspicious. "
" Two broad conclusions can be drawn from these results. Firstly, with their additional accesses, the consistent (or indeed advanced) susceptibility of technical staff and lack of enhanced reporting represents heightened risk. Second, a heightened general IT literacy, and likely phishing awareness, does not reduce susceptibility to email phishing. If those people employed in ‘technical’ roles are no better at preventing or defending against phishing attacks, why believe we can upskill ‘non-technical’ members of staff to be able to? Instead, we should develop robust security practices to enable those who are less susceptible can protect those who are more at risk.
Another important if less controversial finding from our study is that the rate that people will report suspicious emails as phishing is directly related to the process of reporting itself. Of the four organizations involved in our study, one did not provide reporting data, one relied on users sending on a suspicious email to a shared inbox, one was in the process of rolling out a reporting button in their email client, but had only deployed it to two groups, the rest forwarded the emails on. The final organization all had access to a button in their email client. In this last organization, with the button, staff reported 47% of the emails as suspicious. In the organization without a button at all only 13% of staff reported the email as suspicious. In the organization that was split, those with the reporting button reported 44% of the emails as suspicious while those without reported only 11%. Organizations must have a method for identifying malicious emails that have bypassed their technical protective measures. Once an email is in an inbox it is up to the owner of the inbox to deem it suspicious and alert the security teams. Failing to provide a single, simple method for reporting means you are likely to have only a quarter of the phishing emails reported than you would otherwise see with a button available. We strongly advise that all organizations implement a reporting button for all their email users. The subsequent problem of four times the number of reported emails to manually sift through should be solved by automation and triage.
Finally, on the issue of reporting for security, we must consider speed. Time is of the upmost importance to both attackers seeking to compromise your network, and to your security teams trying to prevent them. Our study found that in the first five minutes of an email being delivered, more than three times the number of people who report the email as suspicious will have fallen victim to it. After five minutes this number begins to even out and after 30 minutes you should expect more reports than clicks. It takes more time to review an email and decide it is suspicious, then to report it, than it takes to believe its rouse and fall victim. Removing barriers and having an effective method for dealing with reported emails quickly is essential to prevent damage from phishing.
- Humans will remain susceptible to phishing attacks, no matter their role.
- Support those who are more likely to spot a phishing attack with a single simple to use reporting method – ideally a button in their email client.
- Speed is of the essence, so arrange your security center to be able to triage and respond to the highest threat emails quickly.

Insight from a large-scale phishing study - F-Secure Blog
We conducted a phishing study, targeting 82,402 individuals from four organizations with one of four phishing emails.
Full study:
