- Jan 24, 2011
- 9,378
A new trojan identified as Trojan.Mutabaha.1 uses a recently disclosed UAC bypass technique to install a heavily modified Outfire browser that replaces the user's native Google Chrome browser.
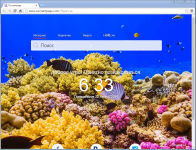
Outfire, which is a Chromium-based browser, looks very much like Chrome, with minimal changes to its setup. As such, the browser makes a fine choice for tricking the user into thinking they're using Chrome, when they're not.
Mutabaha was created between August 15 and 18
The Mutabaha trojan is one of the latest additions to the malware market. At this moment, researchers don't know how crooks are distributing the trojan to victims, but they found out how it infects their computers.
Russian security vendor Dr.Web says the trojan uses a UAC bypass technique to execute a series of files and commands on infected PCs without triggering the Windows UAC (User Account Control) alert.
The technique was only recently disclosed by two security researchers on August 15, two weeks ago. Their UAC bypass technique, which we explained in a previous article, uses the Windows Event Viewer built-in utility to skirt UAC protections.
Dr.Web says that Mutabaha appeared just three days after researchers published their UAC bypass method. When users run the trojan, it uses a system registry key to launch a program with elevated privileges that downloads and installs a malware dropper and a BAT file.
Crooks replace default Chrome with new browser called Outfire
This malware dropper downloads the Outfire browser and installs it automatically. After the installation ends, the BAT (Windows Batch) file deletes the malware dropper.
During installation, Outfire adds itself to the Windows Registry to gain boot persistence, removes Google Chrome shortcuts from the system, and imports Chrome settings into its own.
Read more: Trojan Uses Recently Disclosed UAC Bypass to Install Fake Chrome Browser

Outfire, which is a Chromium-based browser, looks very much like Chrome, with minimal changes to its setup. As such, the browser makes a fine choice for tricking the user into thinking they're using Chrome, when they're not.
Mutabaha was created between August 15 and 18
The Mutabaha trojan is one of the latest additions to the malware market. At this moment, researchers don't know how crooks are distributing the trojan to victims, but they found out how it infects their computers.
Russian security vendor Dr.Web says the trojan uses a UAC bypass technique to execute a series of files and commands on infected PCs without triggering the Windows UAC (User Account Control) alert.
The technique was only recently disclosed by two security researchers on August 15, two weeks ago. Their UAC bypass technique, which we explained in a previous article, uses the Windows Event Viewer built-in utility to skirt UAC protections.
Dr.Web says that Mutabaha appeared just three days after researchers published their UAC bypass method. When users run the trojan, it uses a system registry key to launch a program with elevated privileges that downloads and installs a malware dropper and a BAT file.
Crooks replace default Chrome with new browser called Outfire
This malware dropper downloads the Outfire browser and installs it automatically. After the installation ends, the BAT (Windows Batch) file deletes the malware dropper.
During installation, Outfire adds itself to the Windows Registry to gain boot persistence, removes Google Chrome shortcuts from the system, and imports Chrome settings into its own.
Read more: Trojan Uses Recently Disclosed UAC Bypass to Install Fake Chrome Browser
