Top ad-blocking plugin uBlock Origin has come under fire for being a little too eager in its quest to murder nasty stuff on the internet: it prevents browsers from sounding the alarm on hacking attacks.
At the heart of the matter is a fairly new technology called content security policy reporting, or CSP reporting. It's documented here as a W3C draft, here by Google, and over here by Mozilla. Websites can use CSPs to whitelist the scripting code that's allowed to run on their pages, thus stopping attackers from injecting malicious JavaScript into browsers that hijack users' logged-in accounts.
It's supposed to kill cross-site-scripting, aka XSS, attacks, and automatically report hacking attempts back to the website's administrators. It's very handy.
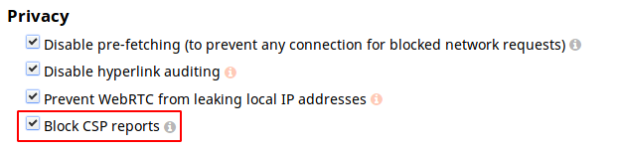
However, uBlock Origin is blocking browsers from sending these CSP alerts, infosec consultant Scott Helme reported on Monday in a bug report on the uBlock Origin GitHub repo. The free Chrome and Firefox plugin bins all CSP reports if any script neutered to protect the user's privacy is allowed onto the page, such as a defanged Google Analytics script.
In his bug report, Helme wrote:
uBO is blocking the sending of legitimate CSP reports. I have a policy setup on Scott Helme which fires multiple reports that are all blocked.
uBlock Origin developer Raymond Hill replied that this is "by design," and that the plugin kills all CSP alerts if any neutered scripts, such as Google traffic analytics, are allowed to run. He added users could manually whitelist Google Analytics for a particular site to avoid any CSP reports being suppressed, and closed the bug:
uBO will block CSP reports if it injects at least one neutered script in a page. This is what is happening on Scott Helme, uBO is injecting a neutered Google Analytics script. In such case, uBO conservatively assumes that the injected script is what is causing the CSP reports and blocks them. If you create an allow rule for Google Analytics for that site, the CSP reports are not blocked.
The trouble is that websites won't receive alerts from browsers when uBlock Origin is installed and miscreants are trying to execute XSS attacks. That means site developers and admins may be unaware of attempts to exploit weaknesses in their code, vulnerabilities may not be addressed, and people may end up losing control of their accounts if attacked. Ultimately, Helme and others want to end uBlock Origin's broad blockade of CSP alerts.
"uBO can block Google Analytics without interfering with CSP reports. The two things aren't related, they're choosing to prevent the CSP report being sent," Helme told El Reg. Troy Hunt, who runs the Have I Been Pwned website, added: "This is the problem: if you've got an XSS risk on your site, for example, a browser running uBlock Origin can no longer report it to you."
Hill countered that CSP reports are a potential privacy issue, in that it is data phoned home to a remote server. “CSP reporting helps a host to fix their own problems in configuring their server, it does not help at all to fix users' own problems. CSP reports are not for the benefits of users – to say so is just marketing,” he argued.
Essentially, uBlock Origin is trying to stop Google Analytics from tracking people across the web. Hill warned that spurious CSP reports may be generated when it neuters scripts, and it blocks these reports to prevent information leakage.
Helme told El Reg that uBlock Origin’s blanket policy was not only unworkable but ill-conceived. Any information reported back to a website from one of its own webpages should be known to the website anyway: the site generated the page, after all.
“uBO is taking unilateral and indiscriminate action against all reports,” Helme explained. “If they want to restrict reports caused by them then fair enough, but to stop the site sending any reports about security incidents just seems dangerous at best.
“I don't see how sending a CSP report to a reporting service is any more privacy violating than loading an image, script or stylesheet from a content delivery network. 99.99999 per cent of users aren't even going to know about CSP so suggesting that users can manually whitelist this to make it work is a non-starter."
The issue has sparked a lively debate on social media. Techie Dmitry Chestnykh, a uBlock Origin user, argued that the plugin is enhancing user privacy: "CSP reporting is not a security feature for users, CSP blocking is. It's not user's responsibility to report that your site is broken."
Paul Moore, a UK-based chief information security officer with an interest in web privacy, disagreed. "It seems bizarre that a plugin to aid security and privacy not only breaks enhanced user agent features but actively refuses to fix it," he said.
Meanwhile, Hill has since reopened Helme's bug to reinvestigate the matter, noting: "I will look into whether it is possible and practical for uBO to block only whatever CSP reports are fired as a result of uBO doing its job."
In short, if you use uBlock Origin, for now, your browser can't warn websites when they and their users are under attack from account and session hijackers.
uBlock Origin ad-blocker knocked for blocking hack attack squawking
At the heart of the matter is a fairly new technology called content security policy reporting, or CSP reporting. It's documented here as a W3C draft, here by Google, and over here by Mozilla. Websites can use CSPs to whitelist the scripting code that's allowed to run on their pages, thus stopping attackers from injecting malicious JavaScript into browsers that hijack users' logged-in accounts.
It's supposed to kill cross-site-scripting, aka XSS, attacks, and automatically report hacking attempts back to the website's administrators. It's very handy.
However, uBlock Origin is blocking browsers from sending these CSP alerts, infosec consultant Scott Helme reported on Monday in a bug report on the uBlock Origin GitHub repo. The free Chrome and Firefox plugin bins all CSP reports if any script neutered to protect the user's privacy is allowed onto the page, such as a defanged Google Analytics script.
In his bug report, Helme wrote:
uBO is blocking the sending of legitimate CSP reports. I have a policy setup on Scott Helme which fires multiple reports that are all blocked.
uBlock Origin developer Raymond Hill replied that this is "by design," and that the plugin kills all CSP alerts if any neutered scripts, such as Google traffic analytics, are allowed to run. He added users could manually whitelist Google Analytics for a particular site to avoid any CSP reports being suppressed, and closed the bug:
uBO will block CSP reports if it injects at least one neutered script in a page. This is what is happening on Scott Helme, uBO is injecting a neutered Google Analytics script. In such case, uBO conservatively assumes that the injected script is what is causing the CSP reports and blocks them. If you create an allow rule for Google Analytics for that site, the CSP reports are not blocked.
The trouble is that websites won't receive alerts from browsers when uBlock Origin is installed and miscreants are trying to execute XSS attacks. That means site developers and admins may be unaware of attempts to exploit weaknesses in their code, vulnerabilities may not be addressed, and people may end up losing control of their accounts if attacked. Ultimately, Helme and others want to end uBlock Origin's broad blockade of CSP alerts.
"uBO can block Google Analytics without interfering with CSP reports. The two things aren't related, they're choosing to prevent the CSP report being sent," Helme told El Reg. Troy Hunt, who runs the Have I Been Pwned website, added: "This is the problem: if you've got an XSS risk on your site, for example, a browser running uBlock Origin can no longer report it to you."
Hill countered that CSP reports are a potential privacy issue, in that it is data phoned home to a remote server. “CSP reporting helps a host to fix their own problems in configuring their server, it does not help at all to fix users' own problems. CSP reports are not for the benefits of users – to say so is just marketing,” he argued.
Essentially, uBlock Origin is trying to stop Google Analytics from tracking people across the web. Hill warned that spurious CSP reports may be generated when it neuters scripts, and it blocks these reports to prevent information leakage.
Helme told El Reg that uBlock Origin’s blanket policy was not only unworkable but ill-conceived. Any information reported back to a website from one of its own webpages should be known to the website anyway: the site generated the page, after all.
“uBO is taking unilateral and indiscriminate action against all reports,” Helme explained. “If they want to restrict reports caused by them then fair enough, but to stop the site sending any reports about security incidents just seems dangerous at best.
“I don't see how sending a CSP report to a reporting service is any more privacy violating than loading an image, script or stylesheet from a content delivery network. 99.99999 per cent of users aren't even going to know about CSP so suggesting that users can manually whitelist this to make it work is a non-starter."
The issue has sparked a lively debate on social media. Techie Dmitry Chestnykh, a uBlock Origin user, argued that the plugin is enhancing user privacy: "CSP reporting is not a security feature for users, CSP blocking is. It's not user's responsibility to report that your site is broken."
Paul Moore, a UK-based chief information security officer with an interest in web privacy, disagreed. "It seems bizarre that a plugin to aid security and privacy not only breaks enhanced user agent features but actively refuses to fix it," he said.
Meanwhile, Hill has since reopened Helme's bug to reinvestigate the matter, noting: "I will look into whether it is possible and practical for uBO to block only whatever CSP reports are fired as a result of uBO doing its job."
In short, if you use uBlock Origin, for now, your browser can't warn websites when they and their users are under attack from account and session hijackers.
uBlock Origin ad-blocker knocked for blocking hack attack squawking
Last edited: