FortiGuard Labs has identified continued botnet activity exploiting vulnerabilities in D-Link routers, demonstrating how legacy security flaws remain a persistent threat. Two botnets, “FICORA” and “CAPSAICIN,” were found targeting vulnerabilities in aging D-Link firmware, including flaws disclosed nearly a decade ago.
The
analysis, conducted in October and November 2024, focused on the Mirai-based “FICORA” and the Kaiten-variant “CAPSAICIN”, both of which leverage weaknesses in the Home Network Administration Protocol (HNAP) interface.
Devices affected include several D-Link models with firmware versions dating back to CVE-2015-2051, CVE-2019-10891, CVE-2022-37056, and CVE-2024-33112. Vulnerable devices include D-Link DIR-645, DIR-806, GO-RT-AC750, and DIR-845L routers. Attackers exploit these vulnerabilities to execute commands remotely, enabling them to control affected devices, often using them in Distributed Denial of Service (DDoS) attacks.
FICORA: global impact
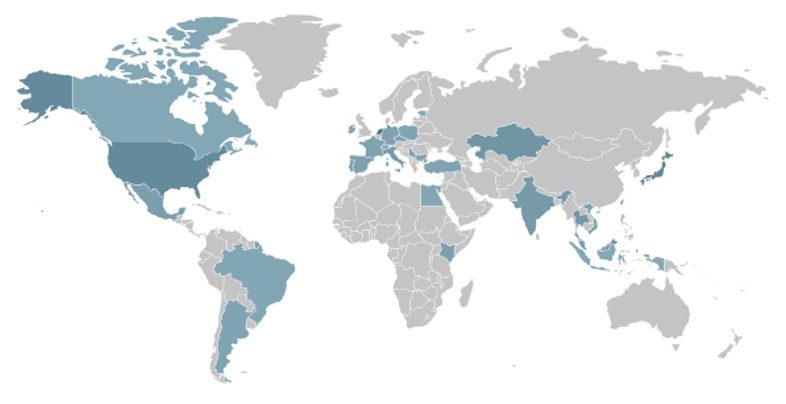
The FICORA botnet was observed initiating attacks from servers in the Netherlands and infecting devices worldwide. Its attack chain begins by downloading and executing a malicious shell script named “multi”, which uses tools like wget, curl, tftp, and ftpget to distribute malware to various Linux architectures, including ARM, MIPS, PowerPC, and x86 variants.
The malware uses ChaCha20 encryption for C2 server configurations, features brute-force attack functionality using hard-coded username-password pairs, while it also employs a script that terminates competing malware processes such as “dvrHelper.” FICORA has been linked to a series of UDP, TCP, and DNS flood DDoS attacks, making it a potent tool for disruption.
FICORA's spread worldwide
Fortinet
CAPSAICIN: short-lived but focused
The CAPSAICIN botnet, active primarily on October 21 and 22, 2024, heavily targeted East Asian countries. Delivered via a malicious script named “bins.sh”, it infects multiple Linux architectures and immediately eliminates other botnet processes to ensure exclusive execution.
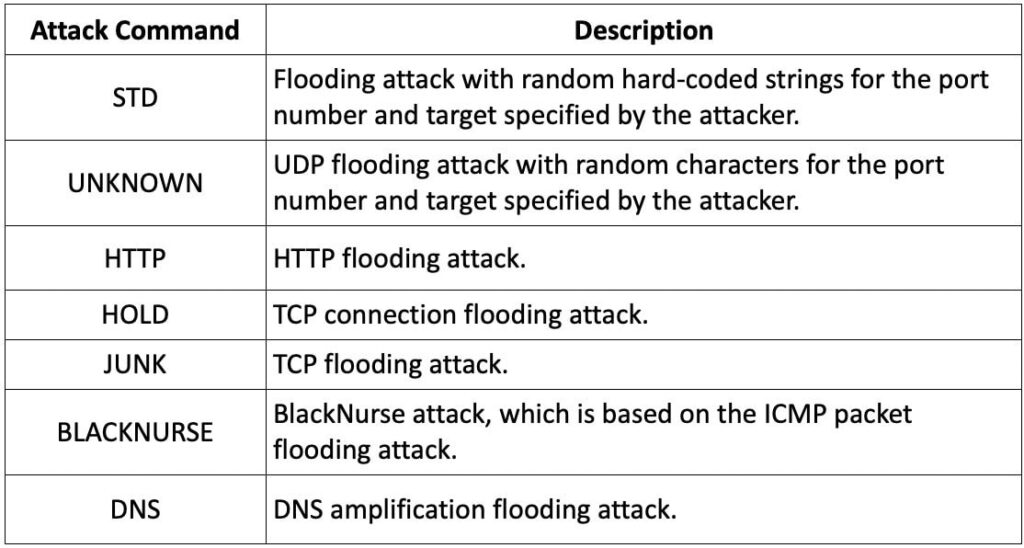
Upon infecting a device, CAPSAICIN establishes a connection with its C2 server, transmitting OS information and a unique identifier, and executes a range of C2 commands, including setting up environment variables and triggering DDoS attacks. The malware also utilizes a “help” function embedded in its code for attackers, detailing parameters for its functions. Researchers believe CAPSAICIN is derived from the Keksec group's botnets, with hard-coded version indicators confirming its lineage.
CAPSAICIN's DDoS commands
Fortinet
D-Link, a major provider of networking equipment, has faced criticism recently for shipping
insecure firmware and
refusing to issue fixing patches for EoL devices still
used by tens of thousands. While the vulnerabilities in question were patched years ago, many devices remain unpatched or unsupported due to end-of-life status, leaving them exposed to exploitation.
Users are advised to update their router firmware, replace aging devices, separate IoTs from critical systems, and monitor for suspicious activity like the appearance of new admin users or change of DNS settings.