- Jul 22, 2014
- 2,525
- 1
- 23,394
- 3,488
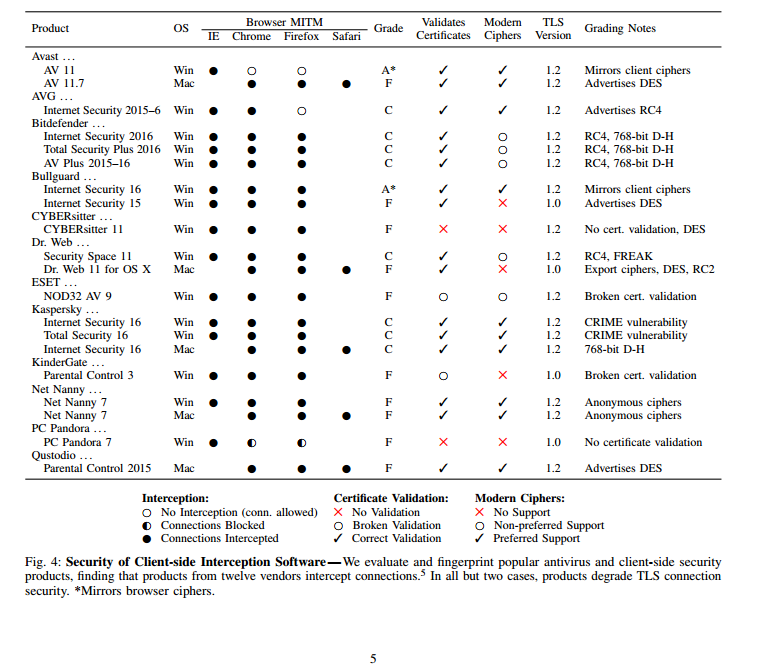
In an advisory sent to enterprises across the US, the Department of Homeland Security’s US-CERT group is warning that security products which perform HTTPS interception might weaken a company's overall security.
HTTPS inspection is a method where security products set up a man-in-the-middle proxy for HTTPS traffic. The proxy stands between the client and the remote server and intercepts HTTPS traffic, inspecting it for malware, and rebuilding the connection.
The issue comes from the fact that many security products, such as firewalls or antivirus products, fail to reconstruct the SSL connections to the same standards clients and servers negotiated.
"Many HTTPS inspection products do not properly verify the certificate chain of the server before re-encrypting and forwarding client data, allowing the possibility of a MiTM attack," US-CERT wrote in its advisory. "Furthermore, certificate-chain verification errors are infrequently forwarded to the client, leading a client to believe that operations were performed as intended with the correct server."
Research paper triggered CERT warning
The CERT advisory came after a group of security experts published a research paper at the start of the month titled "The Security Impact of HTTPS Interception."
More details in the link above
HTTPS inspection is a method where security products set up a man-in-the-middle proxy for HTTPS traffic. The proxy stands between the client and the remote server and intercepts HTTPS traffic, inspecting it for malware, and rebuilding the connection.
The issue comes from the fact that many security products, such as firewalls or antivirus products, fail to reconstruct the SSL connections to the same standards clients and servers negotiated.
"Many HTTPS inspection products do not properly verify the certificate chain of the server before re-encrypting and forwarding client data, allowing the possibility of a MiTM attack," US-CERT wrote in its advisory. "Furthermore, certificate-chain verification errors are infrequently forwarded to the client, leading a client to believe that operations were performed as intended with the correct server."
Research paper triggered CERT warning
The CERT advisory came after a group of security experts published a research paper at the start of the month titled "The Security Impact of HTTPS Interception."
More details in the link above