What's old is new again, with researchers seeing a threefold increase in malware distributed through USB drives in the first half of 2023
A new report by
Mandiant outlines how two USB-delivered malware campaigns have been observed this year; one named 'Sogu,' attributed to a Chinese espionage threat group 'TEMP.HEX,' and another named 'Snowydrive,' attributed to UNC4698, which targets oil and gas firms in Asia.
Mandiant reports that Sogu is currently the most aggressive USB-assisted cyber-espionage campaign, targeting many industries worldwide and attempting to steal data from infected computers.
The victims of Sogu malware are located in the United States, France, the UK, Italy, Poland, Austria, Australia, Switzerland, China, Japan, Ukraine, Singapore, Indonesia, and the Philippines.
Most victims belong to the pharmaceutical, IT, energy, communications, health, and logistics sectors, but there are victims across the board.
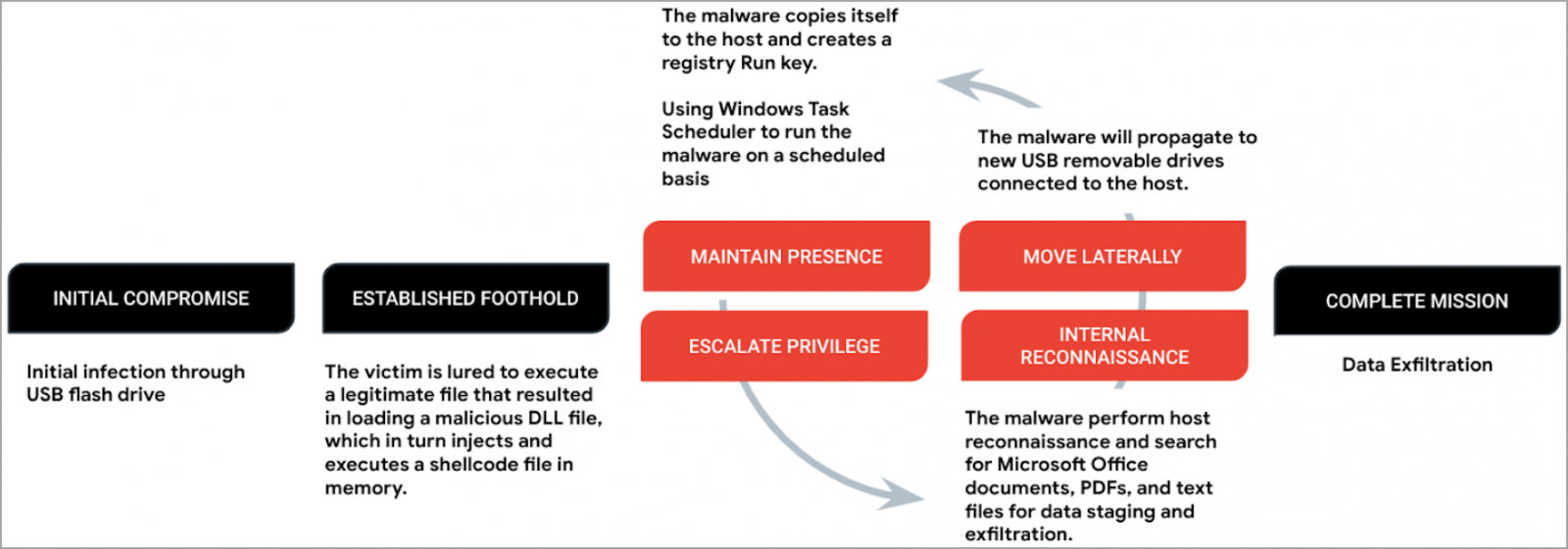
The payload, called 'Korplug,' loads C shellcode (Sogu) into memory via DLL order hijacking, which requires tricking the victim into executing a legitimate file.
Sogu establishes persistence by creating a registry Run key and uses Windows Task Scheduler to ensure it runs regularly.
Sogu attack chain (Mandiant)