- Dec 29, 2014
- 1,717
- 7,419
- 2,679
- 63
First, I will likely be moving from outdated Private Firewall to Comodo Firewall. I am aware of cruelsister's video for this, and thanks to her for that. However, I have so many questions regarding strategies for using Comodo Firewall. I would like to start with ransomeware protection and then build around this protection.
cruelsister's technique for autosanboxing will work for this I see. However, I would like to go further with the settings. What about HIPs? What if anything do they add? Can I use HIPs to have better knowledge of system activity and better control. I will be turning off the a-v this I know.
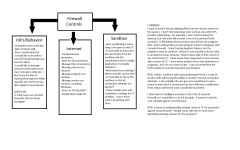
I have a graphic I prepared to try to understand even my questions about CF. Obviously, they make no sense probably. I'm not asking anyone to answer my questions in the graphic, but, if someone would care to look, maybe you would have a comment on CF and something you may have noticed. I know my problems with disappearing files are not "common" to "many" users. I have read some comments of this issue. I am prepared to deal with this, since I have .bat files on the desktop and located in AppData folders and also on attached drives. I don't believe this is the source of the problem, because I wouldn't mind a quarantine if I could find log verfication and something in the quarantine. This has been my biggest issue. No way I will be able to clean up the system in a quick fashion. Ideally, I guess I would turn off HIPs until I have Sandbox settings in place to protect against ransomeware/malware and then I could set up HIPs with some trusted locations.
Still don't know why desktop icons disappeared with CF for me sometimes. I thought I had everything covered. Good HIPs settings should cover me from this I would think.
Please don't think of this as a crazy attempt by myself to solve my problems with CF. Just thought that maybe the graphic and my questions here would help someone think of something about CF that they liked or tried and seemed effective, etc.
cruelsister's technique for autosanboxing will work for this I see. However, I would like to go further with the settings. What about HIPs? What if anything do they add? Can I use HIPs to have better knowledge of system activity and better control. I will be turning off the a-v this I know.
I have a graphic I prepared to try to understand even my questions about CF. Obviously, they make no sense probably. I'm not asking anyone to answer my questions in the graphic, but, if someone would care to look, maybe you would have a comment on CF and something you may have noticed. I know my problems with disappearing files are not "common" to "many" users. I have read some comments of this issue. I am prepared to deal with this, since I have .bat files on the desktop and located in AppData folders and also on attached drives. I don't believe this is the source of the problem, because I wouldn't mind a quarantine if I could find log verfication and something in the quarantine. This has been my biggest issue. No way I will be able to clean up the system in a quick fashion. Ideally, I guess I would turn off HIPs until I have Sandbox settings in place to protect against ransomeware/malware and then I could set up HIPs with some trusted locations.
Still don't know why desktop icons disappeared with CF for me sometimes. I thought I had everything covered. Good HIPs settings should cover me from this I would think.
Please don't think of this as a crazy attempt by myself to solve my problems with CF. Just thought that maybe the graphic and my questions here would help someone think of something about CF that they liked or tried and seemed effective, etc.
Attachments
Last edited: