Hello MalwareTips-Community,
finally I think I found my Config. that changes my whole Network thanks to a few Open-Source Projects and allot of time on my hand coz of COVID-19.
Why is that?
I want to be fair! - and - Want to keep this as short as I can! - So to explain it all it will take hours to write it all down.
How is the concept?
1. ISP function change with Cable Modem Box to Bridge-Mode (Zero Intelligence pure Switch with no NAT)
2. Network Side Security - it all starts from there! (Network Segmentation, Harsh Rules in the Firewall, Secure DNS Communication for all Devices)
3. Communication - Domain Controller (Samba for Raspberry Pi 3) - PBX (3CX for HomeUse License - Free)
4. Computer Security - Windows Configuration thru Policy and Tools - Business Grade Anti-Virus with only needed features (Deep-Learning - Signature - Behavior - Ransomware Protection - URL-Filter - Emulation/Sandboxing - Anti-Phishing Active Module)
5. Backup thru Veeam Agent for Windows and Co.
6. User separation (Admin is Admin and User is the User with almost no Privilege's)
At this Point I would drop down with the Details but as mentioned above I am too lazy for it. I just keep it simple:
My ISP Provided me with a Cable-Modem that was Bridge-Mode compatible like that no Ports coming IN or going OUT are not subject to change. (Example Port 443 remains port 443)
Now a Dilemma comes in to play now you need Network Layered Protection - Of to a Hardware Appliance Firewall - In my case a Open-Hardware Box with Pfsense Community Edition installed. Since I have allot of Devices on my Network I need to segment my Devices. (WAN (Internet) - LAN (HomeNet.) - TV/IoT - Servers (DC/PBX)) This I have done thru IP Segmentation and Rule Definition without VLAN.
Example:
192.168.0.96/28
192.168.100.96/28
192.168.200.96/28
The Firewall setup is a Default Deny on all Interfaces like that there have to be rules for communication. But since all the Networks are known by the Firewall it will route across all Networks by default that need to change and is easily done by Firewall Rules.
Example:
TV/IoT - only can go to the Internet with Ports 80 - 443
DNS and NTP is managed by the Firewall - DNS Traffic gets Forwarded to "NextDNS"
------
Servers - can go to LAN with Ports 88 (Kerberos) - 53 DNS (Domain Controller) - LDAP (389/636 in Future) and so on... This one has a few more Rules coz of the PBX
-----
LAN - Can go to Servers with Ports 88 (Kerberos) - 53 DNS (Domain Controller) - and so on...
HTTP - HTTPS Traffic towards WAN...
Of course there are NAT Rules as well but that has the primary function for the PBX and for a few Games on LAN!
How does your DNS look like traffic wise?! There are two DNS Servers why that?
Good question... -> Since all Networks have there own DHCP Settings I can manipulate what settings get Pushed to a Client per Network Segment!
-> Since all Networks have there own DHCP Settings I can manipulate what settings get Pushed to a Client per Network Segment!
LAN gets the Domain Controller
TV gets the Firewall
Servers get the Domain Controller
Just to mention you got to love DNS Zones and Reverse Lookup Zones
In general all traffic must pass to the Firewall to get forwarded to NextDNS.
LAN -> DC on ServerNet -> Firewall -> NextDNS
Now experienced Admins will jump in and say that is not "best practice" since Pfsense and Co. can forward request to a Domain Controller if needed. (And that is true!) But since I did not use VLAN to disrupt routing between the networks I wanted to prevent conflicts like that all works just fine.
Now to the easy part Computer Security:
Since the Normal User Account has "NO" Install Privilege's and can not run Applications as Admin. the threat scope got a little slimmer just a little. So off to do some Windows 10 tuning...
W10Privacy does allot of the Hard work for you and there are allot of Settings to manage. (Bloatware from a Default Windows 10 install) - (Telemetry) - (Background Process) and allots more...
As a Firewall I use Netlimiter since it shows everything that wants to connect somewhere with IP and Ports makes it easy to manage Firewall Rules on the Windows and Pfsense Box.
Of course the Windows Installation is Domain Joined and has Policy's enforced.
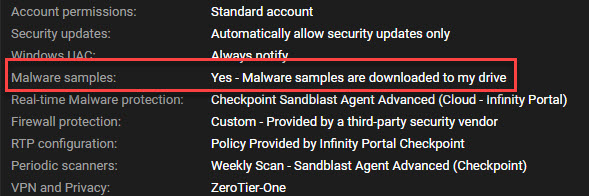
CheckPoint Sandblast Agent Advanced (Engine is partial Kaspersky)
Since I have a Nvidia GPU I use NVCleanInstall to keep the junk out!
RSAT Tools installed to manage Samba AD, GPO and DNS
Total Process count: 76-100
All connections to manage the Servers or Firewall directly are done so with SSH Keys (ONLY) - Authentication on Webinterfaces is handled by the Domain Controller Kerberos. (Sync Pfsense and Sync PBX)
Backup is done Weekly with Veeam - since my important stuff is on my HiDrive on a GDPR compliant Provider!
I would love to go more in to detail but dang this will take forever!
If there are any questions Ill help out as much as I can. ^^
Best regards
Val.
finally I think I found my Config. that changes my whole Network thanks to a few Open-Source Projects and allot of time on my hand coz of COVID-19.
What has changed?
My goal was to recreate a Business Type Network with best practice in mind. That means that allot off things here are for "Advanced Users" that understand the fundamentals of IT-Administration.
My goal was to recreate a Business Type Network with best practice in mind. That means that allot off things here are for "Advanced Users" that understand the fundamentals of IT-Administration.
Why is that?
I want to be fair! - and - Want to keep this as short as I can! - So to explain it all it will take hours to write it all down.
How is the concept?
1. ISP function change with Cable Modem Box to Bridge-Mode (Zero Intelligence pure Switch with no NAT)
2. Network Side Security - it all starts from there! (Network Segmentation, Harsh Rules in the Firewall, Secure DNS Communication for all Devices)
3. Communication - Domain Controller (Samba for Raspberry Pi 3) - PBX (3CX for HomeUse License - Free)
4. Computer Security - Windows Configuration thru Policy and Tools - Business Grade Anti-Virus with only needed features (Deep-Learning - Signature - Behavior - Ransomware Protection - URL-Filter - Emulation/Sandboxing - Anti-Phishing Active Module)
5. Backup thru Veeam Agent for Windows and Co.
6. User separation (Admin is Admin and User is the User with almost no Privilege's)
At this Point I would drop down with the Details but as mentioned above I am too lazy for it. I just keep it simple:
My ISP Provided me with a Cable-Modem that was Bridge-Mode compatible like that no Ports coming IN or going OUT are not subject to change. (Example Port 443 remains port 443)
Now a Dilemma comes in to play now you need Network Layered Protection - Of to a Hardware Appliance Firewall - In my case a Open-Hardware Box with Pfsense Community Edition installed. Since I have allot of Devices on my Network I need to segment my Devices. (WAN (Internet) - LAN (HomeNet.) - TV/IoT - Servers (DC/PBX)) This I have done thru IP Segmentation and Rule Definition without VLAN.
Example:
192.168.0.96/28
192.168.100.96/28
192.168.200.96/28
The Firewall setup is a Default Deny on all Interfaces like that there have to be rules for communication. But since all the Networks are known by the Firewall it will route across all Networks by default that need to change and is easily done by Firewall Rules.
Example:
TV/IoT - only can go to the Internet with Ports 80 - 443
DNS and NTP is managed by the Firewall - DNS Traffic gets Forwarded to "NextDNS"
------
Servers - can go to LAN with Ports 88 (Kerberos) - 53 DNS (Domain Controller) - LDAP (389/636 in Future) and so on... This one has a few more Rules coz of the PBX
-----
LAN - Can go to Servers with Ports 88 (Kerberos) - 53 DNS (Domain Controller) - and so on...
HTTP - HTTPS Traffic towards WAN...
Of course there are NAT Rules as well but that has the primary function for the PBX and for a few Games on LAN!
How does your DNS look like traffic wise?! There are two DNS Servers why that?
Good question...
LAN gets the Domain Controller
TV gets the Firewall
Servers get the Domain Controller
Just to mention you got to love DNS Zones and Reverse Lookup Zones
In general all traffic must pass to the Firewall to get forwarded to NextDNS.
LAN -> DC on ServerNet -> Firewall -> NextDNS
Now experienced Admins will jump in and say that is not "best practice" since Pfsense and Co. can forward request to a Domain Controller if needed. (And that is true!) But since I did not use VLAN to disrupt routing between the networks I wanted to prevent conflicts like that all works just fine.
Now to the easy part Computer Security:
Since the Normal User Account has "NO" Install Privilege's and can not run Applications as Admin. the threat scope got a little slimmer just a little. So off to do some Windows 10 tuning...
W10Privacy does allot of the Hard work for you and there are allot of Settings to manage. (Bloatware from a Default Windows 10 install) - (Telemetry) - (Background Process) and allots more...
As a Firewall I use Netlimiter since it shows everything that wants to connect somewhere with IP and Ports makes it easy to manage Firewall Rules on the Windows and Pfsense Box.
Of course the Windows Installation is Domain Joined and has Policy's enforced.
CheckPoint Sandblast Agent Advanced (Engine is partial Kaspersky)
Since I have a Nvidia GPU I use NVCleanInstall to keep the junk out!
RSAT Tools installed to manage Samba AD, GPO and DNS
Total Process count: 76-100
All connections to manage the Servers or Firewall directly are done so with SSH Keys (ONLY) - Authentication on Webinterfaces is handled by the Domain Controller Kerberos. (Sync Pfsense and Sync PBX)
Backup is done Weekly with Veeam - since my important stuff is on my HiDrive on a GDPR compliant Provider!
I would love to go more in to detail but dang this will take forever!
If there are any questions Ill help out as much as I can. ^^
Best regards
Val.
Last edited: