WhatsApp has unveiled a significant privacy-focused feature for managing and preserving contact lists through Identity Proof Linked Storage (IPLS), a new encrypted storage system.
This innovation, designed to allow seamless
synchronization and recovery of WhatsApp contacts across devices, strengthens privacy protection while maintaining ease of use. The IPLS enables users to securely store, sync, and restore contact lists without WhatsApp having direct access to the metadata, enhancing both flexibility and security.
WhatsApp's IPLS addresses longstanding challenges, such as losing contacts when switching devices. Traditionally, contact management was tethered to a user's phone, with no reliable way to recover the contact list if the phone was lost.
IPLS allows users to securely create and store contacts directly in WhatsApp, which can then be synchronized across multiple devices or selectively kept private to WhatsApp. Notably, IPLS also supports multi-account setups on a single phone, enabling personalized contact lists for different WhatsApp accounts, such as work and personal profiles.
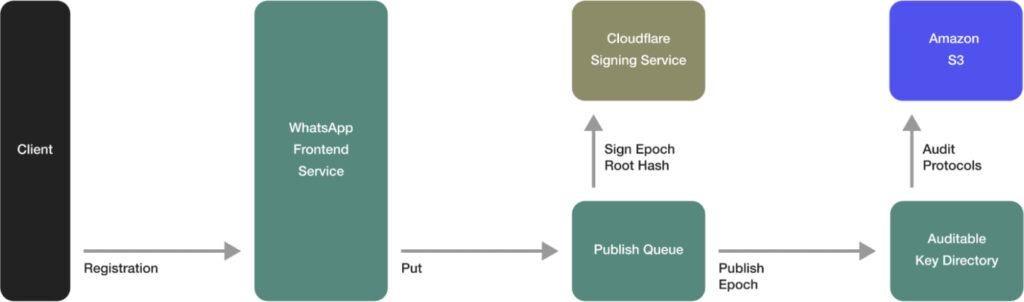
IPLS overview: Meta
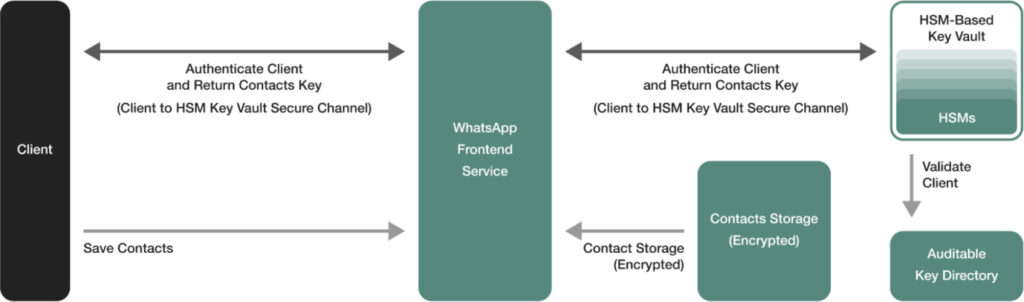
The underlying technology of IPLS combines hardware-based security and key transparency systems. It uses Hardware Security Modules (HSMs) to store encryption keys securely, ensuring that even WhatsApp insiders cannot access the stored data. Contact names are encrypted with a key generated on the client's device, and the system utilizes WhatsApp's key transparency infrastructure to link phone numbers to cryptographic identity keys, ensuring that only verified devices can access the encrypted contacts.
HSM-based Key Vault: Meta
A partnership with Cloudflare ensures additional security through independent auditing of the cryptographic records, with Cloudflare signing every update to the Auditable Key Directory (AKD).
The IPLS system's design incorporates two significant components — Key Transparency and HSMs — to ensure both privacy and security. The AKD, monitored by Cloudflare, is a tamper-resistant directory that logs all key changes, enabling users to verify the authenticity of their cryptographic keys.
Meanwhile, HSMs protect sensitive operations by securing both contact data and cryptographic processes within WhatsApp's infrastructure. This ensures data is opaque even to WhatsApp's own engineers.
In May 2024, Meta Platforms enlisted NCC Group to conduct an independent security audit of the IPLS system. The assessment identified
several security vulnerabilities, including potential misuse of stored keys in HSMs, improper key deletion practices, and potential nonce reuse in encryption.
NCC Group's report highlighted that while the system's design was generally robust, certain weaknesses could allow attackers to access sensitive data under specific conditions. For example, if the cryptographic keys were not properly deleted or if a server manipulated the system's encryption, attackers could intercept user data.
Thanks to those issues being identified prior to roll-out, WhatsApp had the chance to address all 13 security gaps before launching the feature to all users, ensuring that critical problems were fixed.
WhatsApp's implementation of IPLS offers enhanced security for over 2.7 billion users, making it easier to manage contacts across devices and protecting against data loss without sacrificing privacy. This marks a major step forward in privacy-preserving technology, offering users peace of mind while interacting across multiple devices.