Installer Packages:

Installer Packages - Red Canary Threat Report
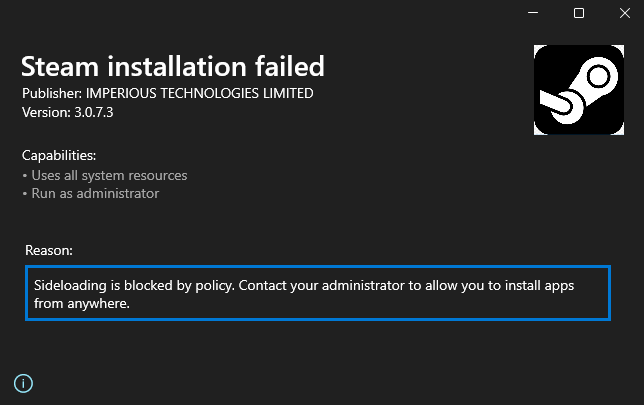
Adversaries are packaging their fake installers with Microsoft’s latest installer format, MSIX, to trick users into downloading malware.
What is MSIX?
MSIX is a packaging format for Windows that eases the packaging, installation, and update process for applications. It is intended to improve upon the limitations of the MSI format. MSIX is an evolution of the APPX format designed originally just for Universal Windows Platform (UWP) applications (i.e., “modern” apps), which were subject to restrictive execution constraints. MSIX makes packaging a software installer easy without imposing execution restraints. As such, it makes for an enticing format for packaging malicious fake installers.
(...)
Why do adversaries use MSIX?
MSIX offers the following advantages to an adversary:
- They can use it to bundle legitimate software alongside malicious code.
- The Windows App Installer app that is responsible for installing MSIX packages offers an easy and consistent installation experience. There aren’t multiple dialog click-throughs like there often are with MSI installers.
- MSIX packages are not subject to SmartScreen inspection when Mark-of-the-Web is applied to an MSIX file.
- Until recently, MSIX packages could be downloaded and installed directly from a web browser using the ms-appinstaller protocol handler.
From an adversary’s perspective though, delivering malicious MSIX packages is not without its risks:
- The installation artifacts must be installed to disk, so they’re subject to additional scrutiny and will leave more forensic artifacts.
- In most cases, MSIX packages must be signed with a valid code-signing certificate, which makes it easier for defenders to track adversary operations.
How do adversaries use MSIX?
Nearly every instance of a malicious MSIX package we’ve encountered tricks a victim into installing what they believe is legitimate software. The malicious MSIX package is packaged in one of two ways most often:
Adversaries may also utilize the DesktopAppMigration element in AppxManifest.xml to persist a shortcut for the app package to the user’s Start Menu Startup directory.
- The legitimate software is included in the MSIX package, but a malicious PowerShell script executes beforehand by employing the Package Support Framework (PSF). In these cases, the MSIX package includes the malicious script, which is executed as specified in an included config.json file.
- The MSIX package only includes a malicious executable without packaging the legitimate software. In these cases, it is unlikely that a PSF PowerShell script will be used.
(...)
See also:

MSIX installer malware delivery on the rise - Red Canary
Red Canary has detected multiple distinct adversaries leveraging MSIX installers to deliver a variety of malware payloads in recent months.
Starting in July 2023, Red Canary began investigating a series of attacks by adversaries leveraging MSIX files to deliver malware. MSIX is a Windows application package installation format that IT teams and developers increasingly use to deliver Windows applications within enterprises.
The adversary in each intrusion appeared to be using malicious advertising or SEO poisoning to draw in victims, who believed that they were downloading legitimate software such as Grammarly, Microsoft Teams, Notion, and Zoom. Victims span multiple industries, suggesting that the adversary’s attacks are opportunistic rather than targeted.