- Sep 23, 2019
- 314
Microsoft now detects HOSTS files that block Windows telemetry
Since the end of July, Windows 10 users began reporting that Windows Defender had started detecting modified HOSTS files as a 'SettingsModifier:Win32/HostsFileHijack' threat.
When detected, if a user clicks on the 'See details' option, they will simply be shown that they are affected by a 'Settings Modifier' threat and has 'potentially unwanted behavior,' as shown below.
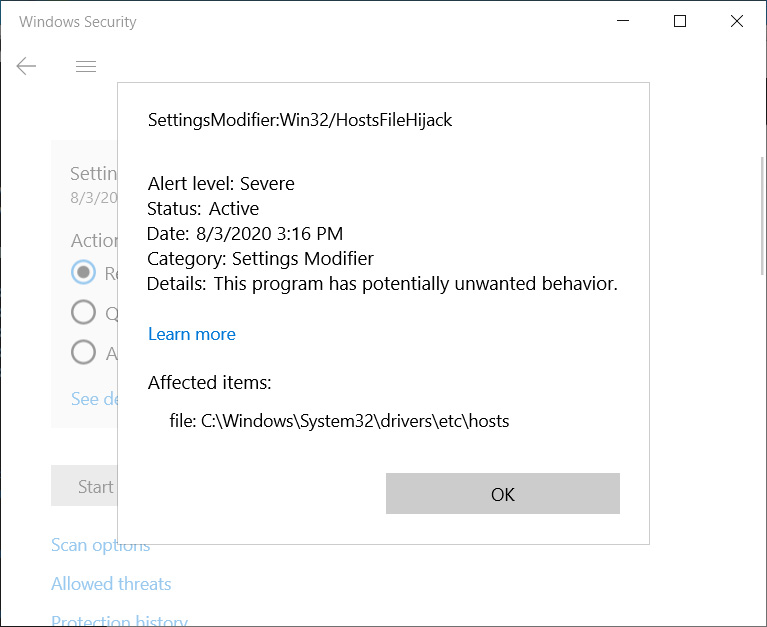
SettingsModifier:Win32/HostsFileHijack detection
BleepingComputer first learned about this issue from BornCity, and while Microsoft Defender detecting HOSTS hijacks is not new, it was strange to see so many people suddenly reporting the detection [1, 2, 3, 4, 5].
While a widespread infection hitting many consumers simultaneously in the past is not unheard of, it is quite unusual with the security built into Windows 10 today.
This led me to believe it was a false positive or some other non-malicious issue.
After playing with generic HOSTS file modifications such as blocking BleepingComputer and other sites, I tried adding a blocklist for Microsoft's telemetry to my HOSTS file.
This list adds many Microsoft servers used by the Windows operating system and Microsoft software to send telemetry and user data back to Microsoft.
As soon as I saved the HOSTS file, I received the following alert stating that I could not save the file as it "contains a virus or potentially unwanted software." I also received alerts that my computer was infected with 'SettingsModifier:Win32/HostsFileHijack.''
HOSTS file blocked from being saved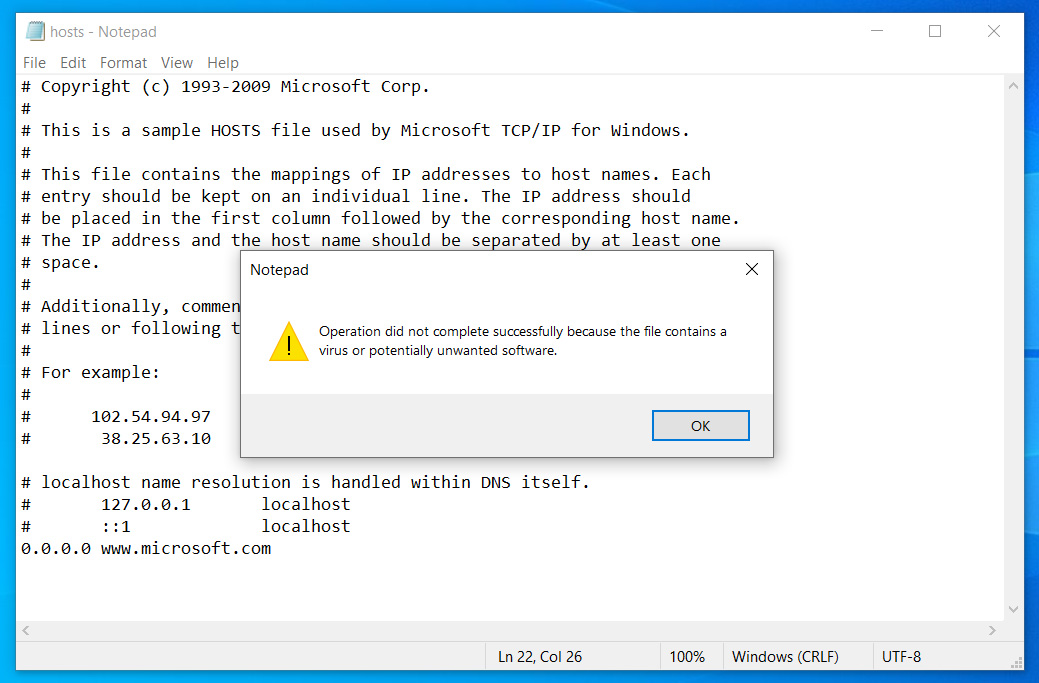
So it seems that Microsoft had recently updated their Microsoft Defender definitions to detect when their servers were added to the HOSTS file.
Users who utilize HOSTS files to block Windows 10 telemetry suddenly caused them to see the HOSTS file hijack detection.
In our tests, some of the Microsoft hosts detected in the Windows 10 HOSTS file include the following:
www.microsoft.com
microsoft.com
telemetry.microsoft.com
wns.notify.windows.com.akadns.net
v10-win.vortex.data.microsoft.com.akadns.net
us.vortex-win.data.microsoft.com
us-v10.events.data.microsoft.com
urs.microsoft.com.nsatc.net
watson.telemetry.microsoft.com
watson.ppe.telemetry.microsoft.com
vsgallery.com
watson.live.com
watson.microsoft.com
telemetry.remoteapp.windowsazure.com
telemetry.urs.microsoft.com
If you decide to clean this threat, Microsoft will restore the HOSTS file back to its default contents.
Default Windows 10 HOSTS file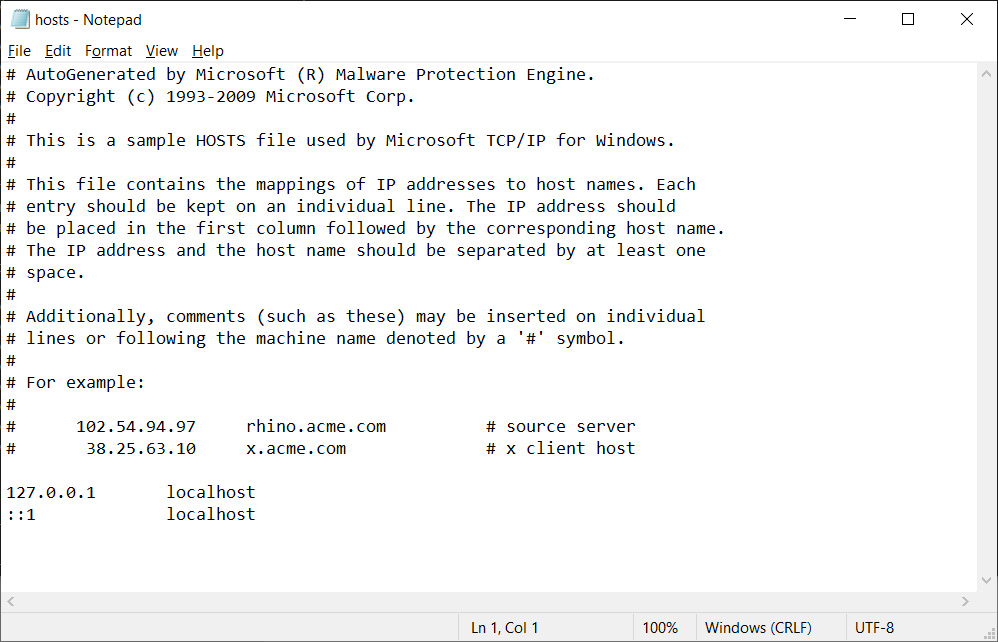
Users who intentionally modify their HOSTS file can allow this 'threat,' but it may enable all HOSTS modifications, even malicious ones, going forward.
So only allow the threat if you 100% understand the risks involved in doing so.
BleepingComputer has reached out to Microsoft with questions regarding this new detection.

Windows 10: HOSTS file blocking telemetry is now flagged as a risk
Starting at the end of July, Microsoft has begun detecting HOSTS files that block Windows 10 telemetry servers as a 'Severe' security risk.
Last edited by a moderator:




