Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
LS,
For people owning a Pro/Business/Ultimate/Enterprise version of their Windows OS and not using the group policy editor to increase security with build in features, here is a simple 10 step tutorial to enable SRP (works for all Windows OS-ses with UAC, so Vista and higher).
SRP stands for Software Restriction Policies. As the name says it can be used to restrict software on your PC. It has basically three modes. This introduction describes how to use Basic User, because Basic User requires little tweaking and still allows to update/install software using Run as Administrator (make sure to create a restore point or have image as backup)
Run as administrator
With these "Basic User default" SRP rules, when you try to run a program in user folders, it will be blocked. You can still update/install software by using the "Run as Administrator" right click context menu in Windows Explorer. Microsoft Installer Packages don't run with elevated (admin) rights by default. Luckily Symantec has provided a registry tweak for that: download MSI "Run as administrator" Context Menu for Vista | Symantec Connect (MsiRunAsAdmin.zip)
Extract the zip file and double click it.
Enabling SRP using Basic User as default level
Click on Windows Start button and choose "Run". Enter secpol.msc and enter. Secpol.msc launches the Local Security Policy management console and follow the instructions on the picture below. Restart your computer when ready and your done.
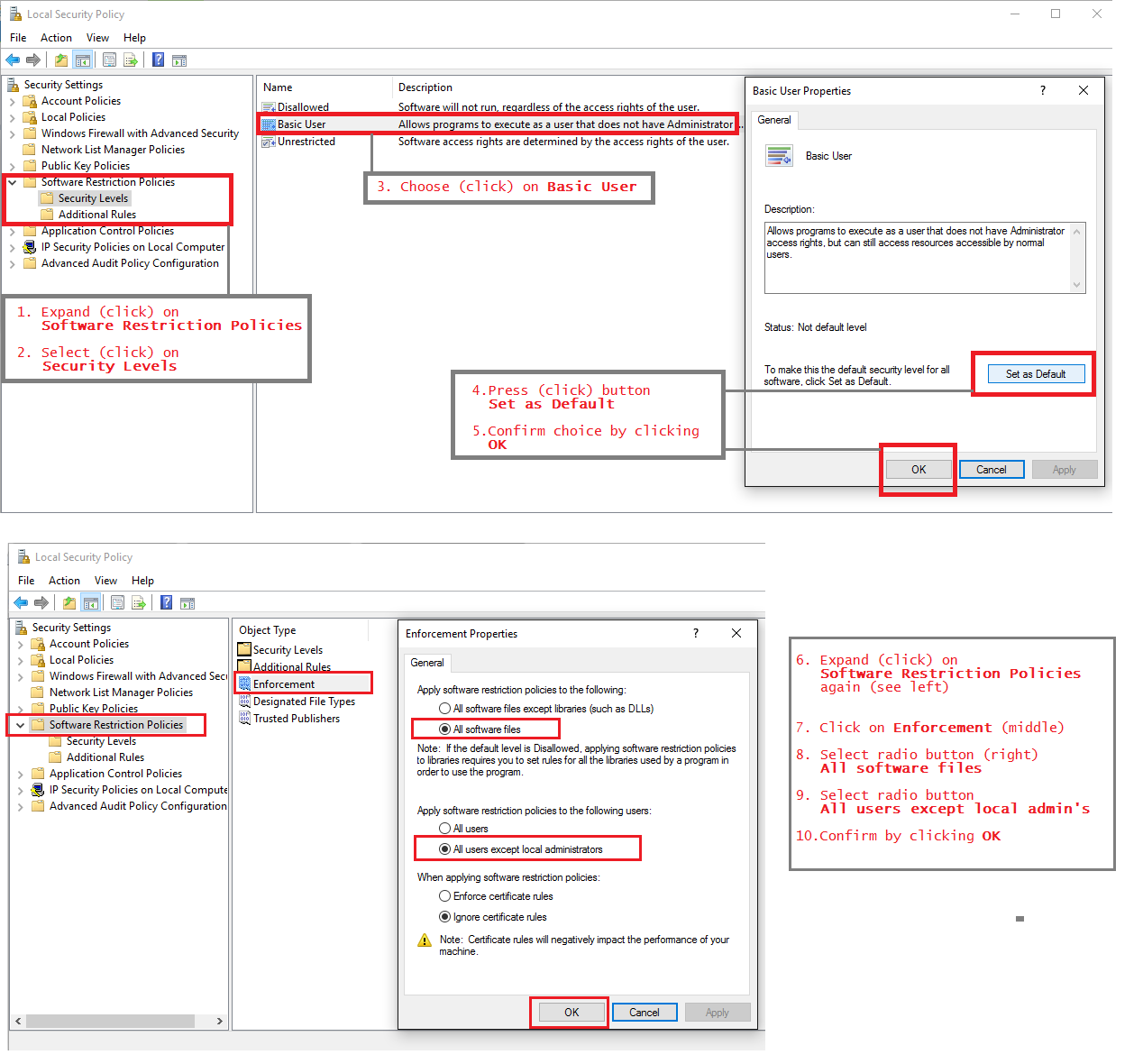
For people owning a Pro/Business/Ultimate/Enterprise version of their Windows OS and not using the group policy editor to increase security with build in features, here is a simple 10 step tutorial to enable SRP (works for all Windows OS-ses with UAC, so Vista and higher).
SRP stands for Software Restriction Policies. As the name says it can be used to restrict software on your PC. It has basically three modes. This introduction describes how to use Basic User, because Basic User requires little tweaking and still allows to update/install software using Run as Administrator (make sure to create a restore point or have image as backup)
Run as administrator
With these "Basic User default" SRP rules, when you try to run a program in user folders, it will be blocked. You can still update/install software by using the "Run as Administrator" right click context menu in Windows Explorer. Microsoft Installer Packages don't run with elevated (admin) rights by default. Luckily Symantec has provided a registry tweak for that: download MSI "Run as administrator" Context Menu for Vista | Symantec Connect (MsiRunAsAdmin.zip)
Extract the zip file and double click it.
Enabling SRP using Basic User as default level
Click on Windows Start button and choose "Run". Enter secpol.msc and enter. Secpol.msc launches the Local Security Policy management console and follow the instructions on the picture below. Restart your computer when ready and your done.
Last edited: