A
Alkajak
Thread author
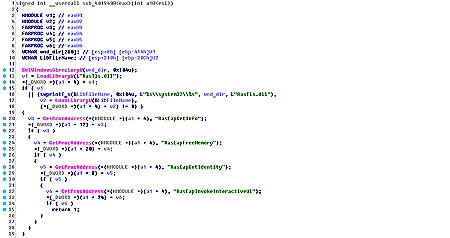
When security researchers discover over 310,000 new malware variants per day, they're bound to stumble upon a dangerous threat once in a while, not just adware, clickfraud, and droppers. The most recent example is BackDoor.Apper, a new spyware variant discovered by Russian security firm Dr.Web.
The company's security experts say this new trojan is distributed via email spam that contains a Microsoft Excel file attachment. When opened, this file will attempt to trick users into enabling the macro feature.
If macros are enabled, the Excel file contains code that downloads a self-extracting RAR file from the Web, unpacks it, and executes the files found inside it.
BackDoor.Apper sends stolen data to a C&C server
As usual with most malware families these days, the first thing it will do is to contact its C&C server. In its first communications, BackDoor.Apper collects information about the local system and sends it to the server.
This information includes data such as computer name, hardware specifications, and hard disk usage statistics. The user's MAC address is also used to generate a unique ID in order for the crook's botnet to distinguish between infected victims.
After this, the truly malicious behavior begins, and BackDoor.Apper starts collecting keystrokes from active windows. The keystrokes are logged locally, along with the name of the window from where they've been collected. At regular intervals, the trojan sends the data to its master's server.
The trojan can also execute code on your computer
Besides this, the trojan can also execute various other operations based on instructions it receives from its C&C server. BackDoor.Apper can download files from the server, launch them into execution, create a list of files found inside a folder and send it to the server, and also steal & upload any file the C&C server deems important.
Further, the trojan can also take snapshots of the user's desktop, and also watch a designated folder for new activity and notify the malware operator.
Dr.Web researchers didn't say if BackDoor.Apper was discovered as part of an APT's malware arsenal or as part of a financially-motivated cyber-crime group's activity, but it surely looks like it has the features to satisfy both use case scenarios.
The company's security experts say this new trojan is distributed via email spam that contains a Microsoft Excel file attachment. When opened, this file will attempt to trick users into enabling the macro feature.
If macros are enabled, the Excel file contains code that downloads a self-extracting RAR file from the Web, unpacks it, and executes the files found inside it.
BackDoor.Apper sends stolen data to a C&C server
As usual with most malware families these days, the first thing it will do is to contact its C&C server. In its first communications, BackDoor.Apper collects information about the local system and sends it to the server.
This information includes data such as computer name, hardware specifications, and hard disk usage statistics. The user's MAC address is also used to generate a unique ID in order for the crook's botnet to distinguish between infected victims.
After this, the truly malicious behavior begins, and BackDoor.Apper starts collecting keystrokes from active windows. The keystrokes are logged locally, along with the name of the window from where they've been collected. At regular intervals, the trojan sends the data to its master's server.
The trojan can also execute code on your computer
Besides this, the trojan can also execute various other operations based on instructions it receives from its C&C server. BackDoor.Apper can download files from the server, launch them into execution, create a list of files found inside a folder and send it to the server, and also steal & upload any file the C&C server deems important.
Further, the trojan can also take snapshots of the user's desktop, and also watch a designated folder for new activity and notify the malware operator.
Dr.Web researchers didn't say if BackDoor.Apper was discovered as part of an APT's malware arsenal or as part of a financially-motivated cyber-crime group's activity, but it surely looks like it has the features to satisfy both use case scenarios.