silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,738
- 123,885
- 8,399
Recent versions of the open source archiver 7-Zip have a vulnerability that has not been fixed yet. Successful exploitation of the vulnerability allows privilege escalation and the execution of commands; it appears that the issue can be exploited locally only.
Filed under CVE-2022-29072, the vulnerability is using the included 7-Zip Help file, 7-zip.chm, for the exploit. Attackers need to drag and drop files with the 7z extension on to the Help > Contents area in the 7-Zip interface.
Vulnerability details have been published on GitHub. The page provides technical information and a short demonstration video of the exploit.
It is unclear if and when 7-Zip will address the issue. The last update of the application dates back to the release of 7-Zip in December 2021
Users of the application may use the following workaround to mitigate the vulnerability on their devices. Since it is using the included Help file, one way of dealing with the issue is to delete the Help file.
The file is moved to the recycle bin of the operating system by default. 7-Zip functionality is not reduced when you delete the help file. The Help file won't open anymore after the deletion, when you select Help > Contents in the 7-Zip File Manager or press the F1-key on the keyboard.
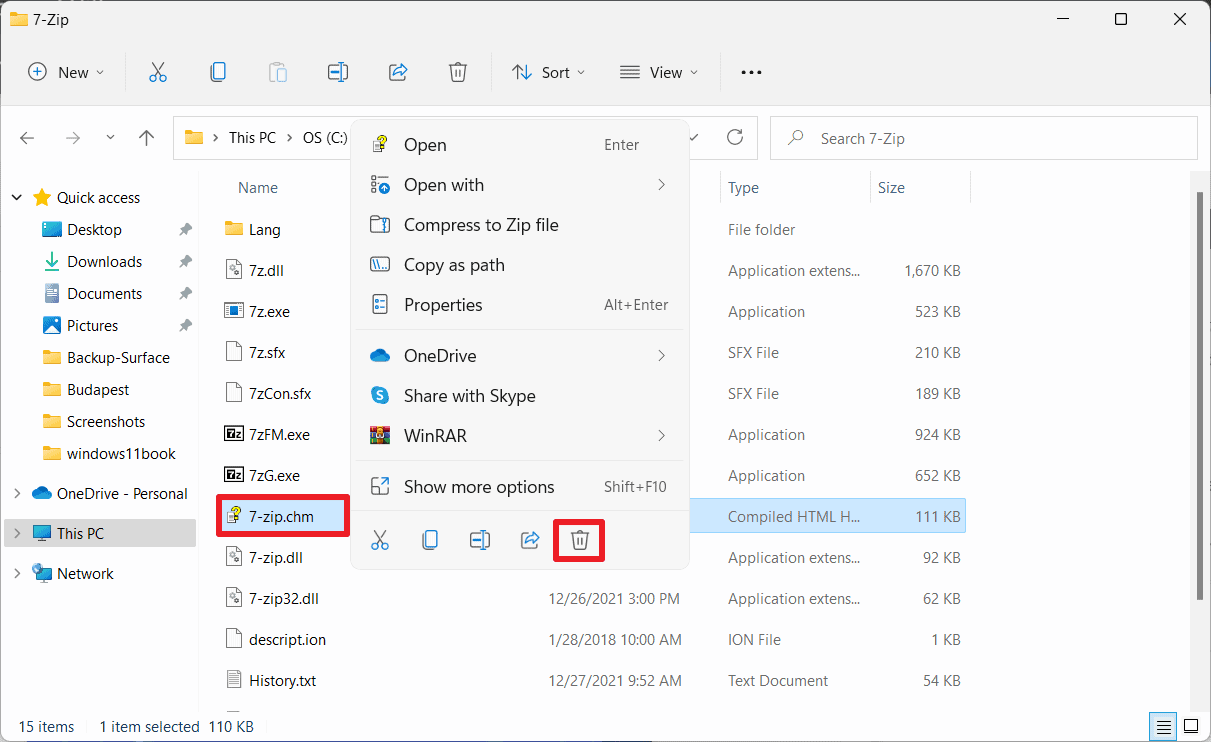
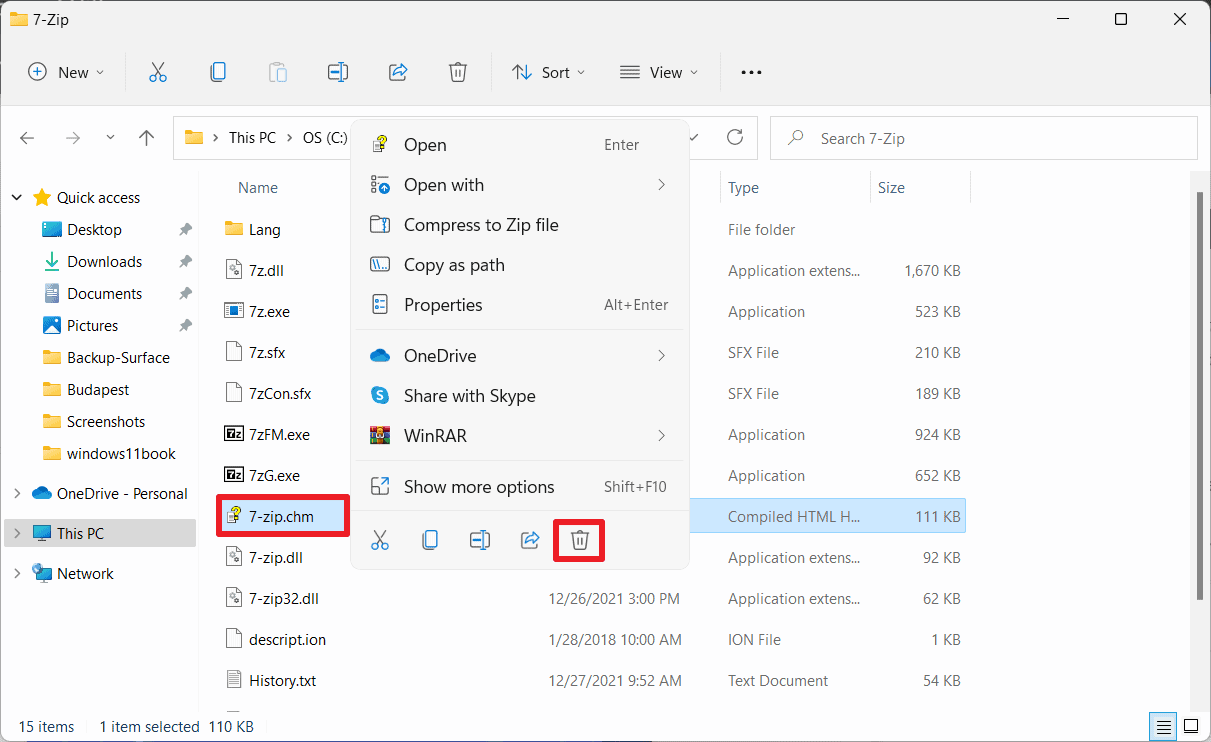
- Open the 7-Zip installation directory or folder on the system. On Windows, these are usually C:\Program Files\7-Zip or C:\Program Files (x86)\7-Zip, depending on whether the 64-bit or the 32-bit version of the application has been installed.
- Locate the file 7-Zip.chm; this is the help file. You can open it directly to display its content.
- Hit the delete button on the keyboard or right-click on the file and select the Delete context menu option, to remove it from the system.
- You may get a prompt, File Access Denied. If that is the case, select Continue.
Workaround for security issue in 7-Zip until it is fixed - gHacks Tech News
Recent versions of the open source archiver 7-Zip have a vulnerability that has not been fixed yet; a workaround is available, however.