- Sep 17, 2013
- 1,492
Today I will be talking about a very disruptive feature that will be present in AMD’s upcoming compute architecture. Disruptive is probably the most misused word in the history of technology and I do not use it casually. While the readers of this site consist primarily of technology enthusiasts, for whom this news may not mean much. From a company like AMD’s standpoint, a vast majority of revenue will come from the Enterprise segment. For Enterprise users, data security is a very important consideration and on that front AMD Zen will be introducing some very significant advanced encryption features, such as SME and SEV. These features are not present in any competing Intel architecture.
AMD Zen features SME (Secure Memory Encryption), SEV (Secure Encrypted Virtualization) and hardware based SHA powered by a security co-processor
There are two main features that I will be talking about in this article, alongside a third feature which in combination will make Zen a much sought out processor for the Enterprise sector. The first two are called SME and SEV, which stand for Secure memory Encryption and Secure Encrypted Virtualization. The third one is hardware based SHA. As I have mentioned before, at this moment, no competing Intel architecture has any known features to rival these. At the time of release, Zen will primarily compete against Skylake and Kaby Lake based processors, both of which lack the aforementioned features. It is not until Cannonlake and Coffe Lake that any semblance of parity is expected to be present between the two platforms – and even then it won’t be complete.
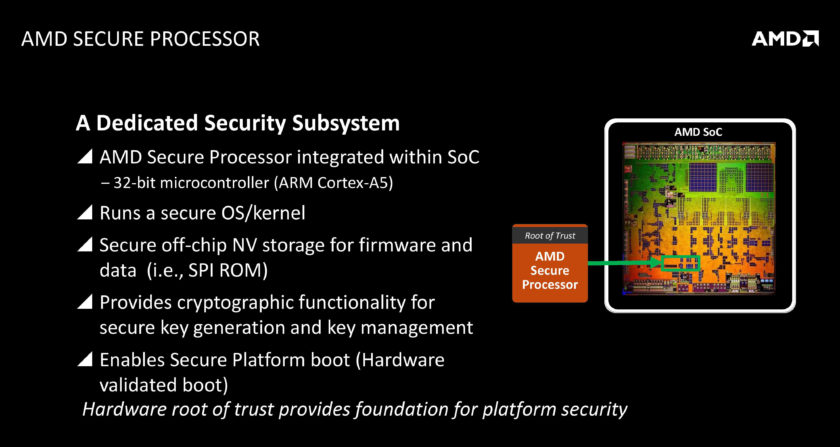
All of this magic will happen, courtesy a “Security Co-Processor” that AMD has included inside of the Zen chip.Before we get into any explicit details – let me explain what all of this fuss is about. Let me explain this by giving you the example of this very publication. WCCFtech is hosted on a VPS based platform that scales according to the traffic we get – in other words, it’s hosted on the cloud. This means that we don’t have to pay for server resources we aren’t using and aren’t left stranded when traffic spikes. When we say it’s hosted on the cloud, what is actually happening is that we are serving our website via an instance of a virtualized server running on a physical server. This virtualized server can scale up or down (depending on the limits of the physical server) dynamically, according to the demand of the client and is hosted primarily in the RAM.
Zen SEV – the holy grail of secure cloud computing?
With the advent of NVDIMM (non volatile memory) however, this is going to become a very big problem, very fast. Unlike inherently volatile DIMMs, non volatile memory does not lose all data and this lowers the difficulty bar for a cyber attack by several orders of magnitude. Since the data is in an unencrypted format in the memory, all an attacker has to do is to kill power to the memory and either physically take the memory or clone its contents. Everything inside it – including passwords, confidential data, hashes – would be in clear text format. To put it bluntly, NVDIMMs are jackpots for physical attack vectors.
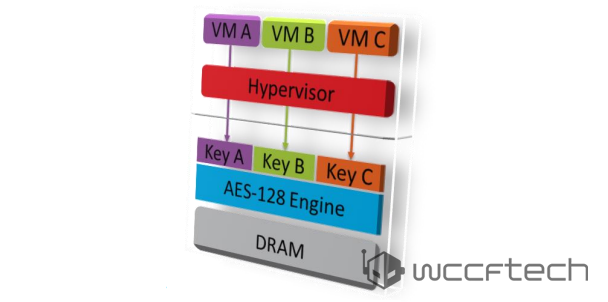
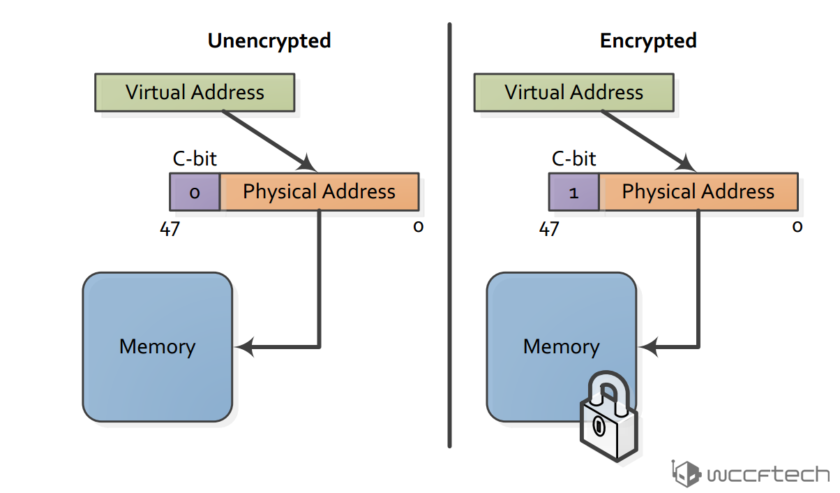
Enter Zen SME. Zen Secure Memory Encryption is something that allows the complete encryption of the memory being used. Your data is encrypted when it’s in transit on the internet. It has always been encrypted when it’s stored on an HDD or SSD in server farms. But the RAM is one place where it has always existed in clear text. With Zen SME, we can close the last remaining “cleartext” portion and enable encryption in the memory as well – for truly end to end security.
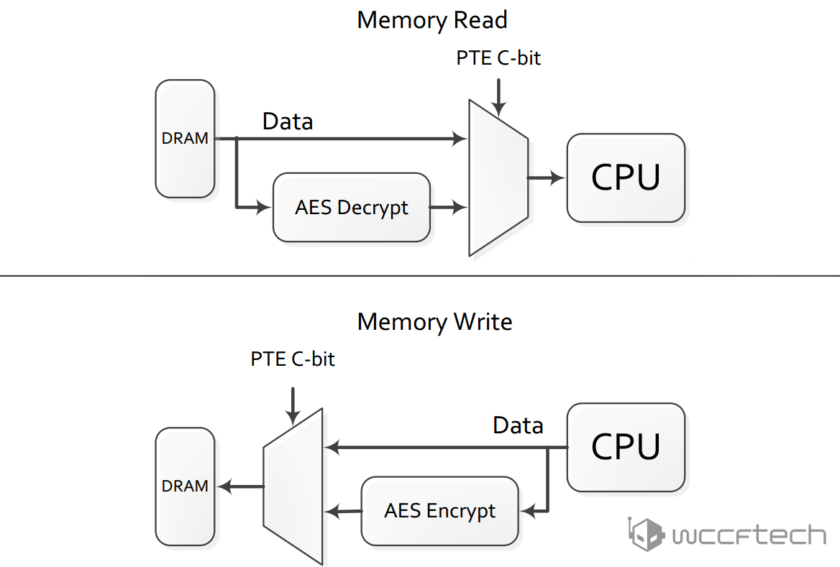
Main memory encryption is performed via dedicated hardware in the on-die memory controllers. Each controller includes a high performance Advanced Encryption Standard (AES) engine that encrypts data when it is written to DRAM, and decrypts it when read as shown. The encryption of data is done with a 128-bit key.
As I have mentioned before, that Intel has something called Software Guard Extensions, but this particular instruction set cannot be virtualized since the silicon giant does not have any complete memory encryption standard. Thanks to SME, we get one more particularly useful feature: Zen SEV or Zen Secure Encrypted Virtualization.
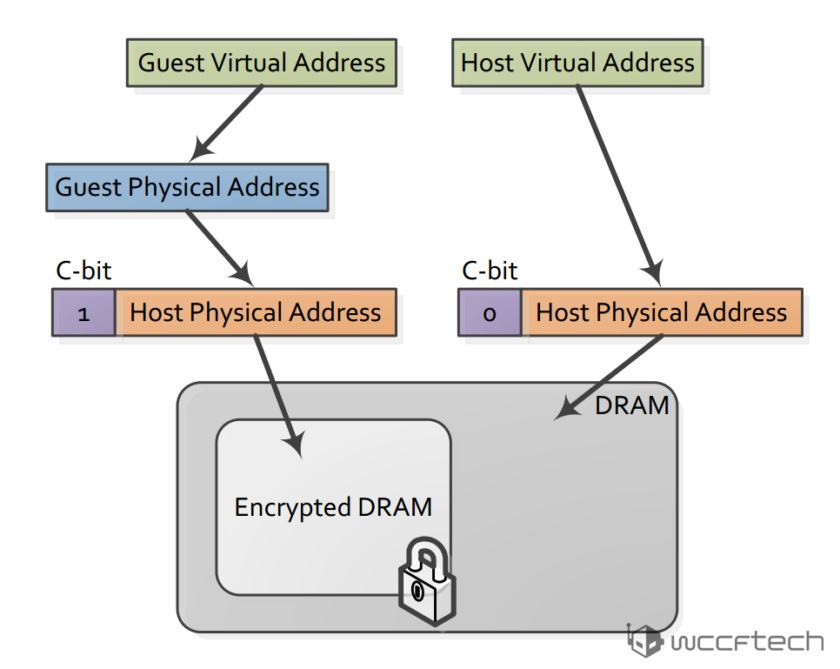
SEV is an extension to the AMD-V architecture which supports running multiple VMs under the control of a hypervisor. When enabled, SEV hardware tags all code and data with its VM ASID which indicates which VM the data originated from or is intended for. This tag is kept with the data at all times when inside the SOC, and prevents that data from being used by anyone other than the owner. While the tag protects VM data inside the SOC, AES with 128 bit encryption protects data outside the SOC.
This is the holy grail of cloud computing (and security conscious individuals) and as the name states, will allow end users to encrypt the entire instance of virtualization. Not even cloud providers (who have physical access to the servers) will be able to carry out any malicious actions against their clients, if they were so inclined. For all intents and purposes, the data of consumers would be well and truly safe.
Zen will also contain hardware SHA – which means it’s going to offer significant performance improvement over previous iterations of AMD architectures and even Intel offerings! As far as we know, hardware based SHA will not be present in Intel offerings till Cannonlake arrives and we have already listed the major disadvantage of SGX – it cannot be virtualized. So at the time of launch, Zen processors will be the only competitive x86 chips around rocking hardware based SHA (and the accelerated performance that comes with it) as well as the security co processor powered SME/SEV security features. It remains to be seen when and if Intel will offer a competing solution to SEV.
AMD Zen features SME (Secure Memory Encryption), SEV (Secure Encrypted Virtualization) and hardware based SHA powered by a security co-processor
There are two main features that I will be talking about in this article, alongside a third feature which in combination will make Zen a much sought out processor for the Enterprise sector. The first two are called SME and SEV, which stand for Secure memory Encryption and Secure Encrypted Virtualization. The third one is hardware based SHA. As I have mentioned before, at this moment, no competing Intel architecture has any known features to rival these. At the time of release, Zen will primarily compete against Skylake and Kaby Lake based processors, both of which lack the aforementioned features. It is not until Cannonlake and Coffe Lake that any semblance of parity is expected to be present between the two platforms – and even then it won’t be complete.
All of this magic will happen, courtesy a “Security Co-Processor” that AMD has included inside of the Zen chip.Before we get into any explicit details – let me explain what all of this fuss is about. Let me explain this by giving you the example of this very publication. WCCFtech is hosted on a VPS based platform that scales according to the traffic we get – in other words, it’s hosted on the cloud. This means that we don’t have to pay for server resources we aren’t using and aren’t left stranded when traffic spikes. When we say it’s hosted on the cloud, what is actually happening is that we are serving our website via an instance of a virtualized server running on a physical server. This virtualized server can scale up or down (depending on the limits of the physical server) dynamically, according to the demand of the client and is hosted primarily in the RAM.
Zen SEV – the holy grail of secure cloud computing?
With the advent of NVDIMM (non volatile memory) however, this is going to become a very big problem, very fast. Unlike inherently volatile DIMMs, non volatile memory does not lose all data and this lowers the difficulty bar for a cyber attack by several orders of magnitude. Since the data is in an unencrypted format in the memory, all an attacker has to do is to kill power to the memory and either physically take the memory or clone its contents. Everything inside it – including passwords, confidential data, hashes – would be in clear text format. To put it bluntly, NVDIMMs are jackpots for physical attack vectors.

Enter Zen SME. Zen Secure Memory Encryption is something that allows the complete encryption of the memory being used. Your data is encrypted when it’s in transit on the internet. It has always been encrypted when it’s stored on an HDD or SSD in server farms. But the RAM is one place where it has always existed in clear text. With Zen SME, we can close the last remaining “cleartext” portion and enable encryption in the memory as well – for truly end to end security.
Main memory encryption is performed via dedicated hardware in the on-die memory controllers. Each controller includes a high performance Advanced Encryption Standard (AES) engine that encrypts data when it is written to DRAM, and decrypts it when read as shown. The encryption of data is done with a 128-bit key.
As I have mentioned before, that Intel has something called Software Guard Extensions, but this particular instruction set cannot be virtualized since the silicon giant does not have any complete memory encryption standard. Thanks to SME, we get one more particularly useful feature: Zen SEV or Zen Secure Encrypted Virtualization.
SEV is an extension to the AMD-V architecture which supports running multiple VMs under the control of a hypervisor. When enabled, SEV hardware tags all code and data with its VM ASID which indicates which VM the data originated from or is intended for. This tag is kept with the data at all times when inside the SOC, and prevents that data from being used by anyone other than the owner. While the tag protects VM data inside the SOC, AES with 128 bit encryption protects data outside the SOC.
This is the holy grail of cloud computing (and security conscious individuals) and as the name states, will allow end users to encrypt the entire instance of virtualization. Not even cloud providers (who have physical access to the servers) will be able to carry out any malicious actions against their clients, if they were so inclined. For all intents and purposes, the data of consumers would be well and truly safe.
Zen will also contain hardware SHA – which means it’s going to offer significant performance improvement over previous iterations of AMD architectures and even Intel offerings! As far as we know, hardware based SHA will not be present in Intel offerings till Cannonlake arrives and we have already listed the major disadvantage of SGX – it cannot be virtualized. So at the time of launch, Zen processors will be the only competitive x86 chips around rocking hardware based SHA (and the accelerated performance that comes with it) as well as the security co processor powered SME/SEV security features. It remains to be seen when and if Intel will offer a competing solution to SEV.