- Sep 22, 2014
- 1,767
A security vulnerability in the popular password manager KeePass 2 was disclosed recently affecting all versions of the password manager but only if automatic update checks are enabled.
KeePass 2 ships with an option to check periodically for program updates. While update checks are performed if the feature is enabled, automatic downloads and installations of updates is not supported.
Basically, what happens is that KeePass communicates with a service to see if an update is available. Users may then click on the update notification if an update is available to open a page on the Internet that provides them with a download of the new version of the password manager.
The vulnerability exploits the fact that KeePass 2 performs update checks over HTTP and not HTTPS. An attacker could exploit this by intercepting update requests, for instance on a local network, sending manipulated update information to the KeePass 2 client, and getting users to open a site on the Internet where a fake version of KeePass is offered on (or other things happen, e.g. drive by downloads).
The developer of KeePass won’t fix the issue according to the report.
How to protect yourself
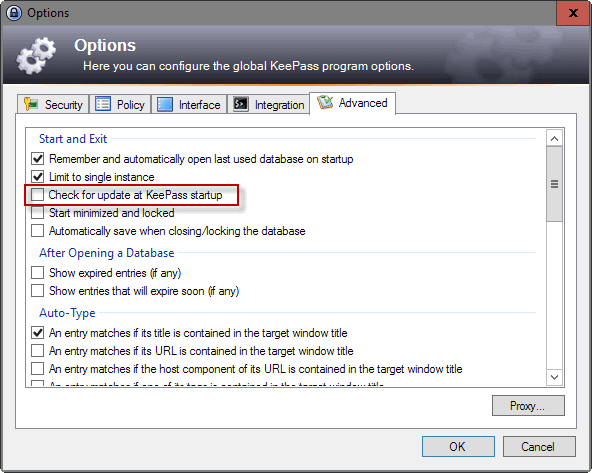
Existing KeePass users have two options when it comes to the issue. The easier option involves disabling update checks in the client.
This is done in the following way:
You could keep update checks enabled on the other hand but instead of clicking on the link provided by KeePass when updates are found, visit the KeePass website manually instead to download updates from it this way.
Both methods work just fine but add a level of inconvenience to the update checking and downloading process. Still, it is recommended to make use of either one of them to protect one of the most important programs on the computer.
KeePass 2 ships with an option to check periodically for program updates. While update checks are performed if the feature is enabled, automatic downloads and installations of updates is not supported.
Basically, what happens is that KeePass communicates with a service to see if an update is available. Users may then click on the update notification if an update is available to open a page on the Internet that provides them with a download of the new version of the password manager.
The vulnerability exploits the fact that KeePass 2 performs update checks over HTTP and not HTTPS. An attacker could exploit this by intercepting update requests, for instance on a local network, sending manipulated update information to the KeePass 2 client, and getting users to open a site on the Internet where a fake version of KeePass is offered on (or other things happen, e.g. drive by downloads).
The developer of KeePass won’t fix the issue according to the report.
How to protect yourself

Existing KeePass users have two options when it comes to the issue. The easier option involves disabling update checks in the client.
This is done in the following way:
- Open the KeePass 2 software on your system.
- Select Tools > Options from the menu at the top.
- Switch to the Advanced tab in the options window, and remove the checkmark from “Check for update at KeePass startup” there.
You could keep update checks enabled on the other hand but instead of clicking on the link provided by KeePass when updates are found, visit the KeePass website manually instead to download updates from it this way.
Both methods work just fine but add a level of inconvenience to the update checking and downloading process. Still, it is recommended to make use of either one of them to protect one of the most important programs on the computer.
Last edited:

