- Jul 22, 2014
- 2,525
An attacker or a rogue employee can create and register custom control panel items and use these files to bypass the Windows AppLocker security feature.
AppLocker is a security service introduced with Windows 7 and Windows Server 2008 R2 that allows system administrators to restrict access to Windows applications based on a rule-based system.
Besides blocking access to games and non-work related applications, system administrators also use AppLocker to set up rules to prevent malware installed on the accounts of low-privileged users from accessing apps that can be abused to carry out attacks, such as cmd.exe, powershell.exe, rundll32.exe, and others.
Researcher bypasses AppLocker using CPL files
...
This bypass technique is possible because both "reg" and "regedit" are Microsoft-signed binaries, located in a trusted folder and allowed by AppLocker by default unless specifically blocked by administrators. Similarly for Control Panel (control.exe), who is also another Windows binary allowed by default AppLocker rules.
While blocking access to utilities like reg, regedit, and the Control Panel is one alternative, Mifsud recommends another method.
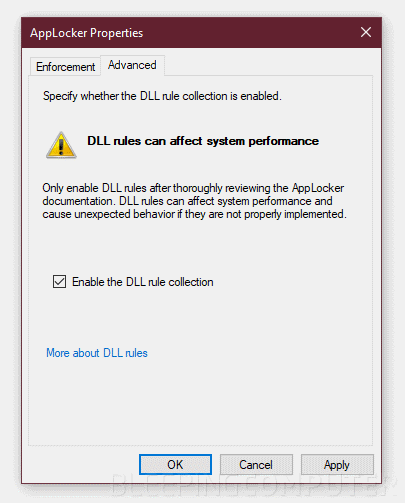
"[T]his attack can be mitigated, at the cost of performance, by enabling the 'DLL Rule Collection' under the AppLocker 'Advanced' tab," Mifsud says.
There are various techniques to execute this attack, all of which are detailed in Mifsud's technical write-up.
AppLocker is a security service introduced with Windows 7 and Windows Server 2008 R2 that allows system administrators to restrict access to Windows applications based on a rule-based system.
Besides blocking access to games and non-work related applications, system administrators also use AppLocker to set up rules to prevent malware installed on the accounts of low-privileged users from accessing apps that can be abused to carry out attacks, such as cmd.exe, powershell.exe, rundll32.exe, and others.
Researcher bypasses AppLocker using CPL files
...
This bypass technique is possible because both "reg" and "regedit" are Microsoft-signed binaries, located in a trusted folder and allowed by AppLocker by default unless specifically blocked by administrators. Similarly for Control Panel (control.exe), who is also another Windows binary allowed by default AppLocker rules.
While blocking access to utilities like reg, regedit, and the Control Panel is one alternative, Mifsud recommends another method.
"[T]his attack can be mitigated, at the cost of performance, by enabling the 'DLL Rule Collection' under the AppLocker 'Advanced' tab," Mifsud says.

There are various techniques to execute this attack, all of which are detailed in Mifsud's technical write-up.