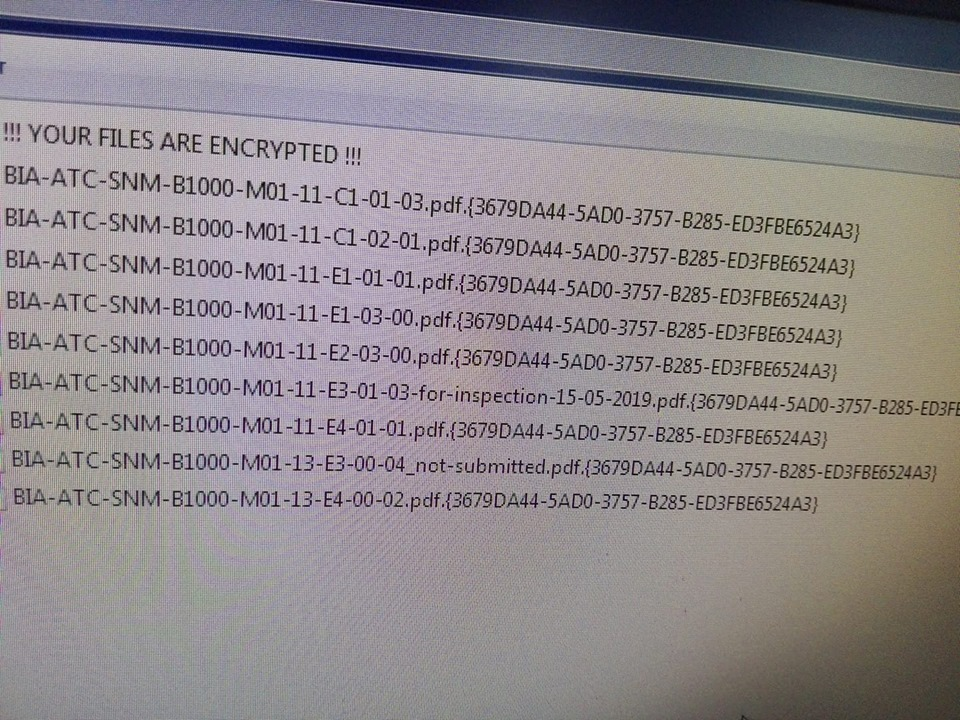
As Jack said the best thing you can do for now is try yo remove the infection and then wait for a decryption tool to be released for that particular ransomware.
I'd run some on demand scanners and, is possible a boot rescue disk such as Kaspersky or Bitdenders rescue disks. I'd make sure connections to you system are as secure as you can make them first. Silly things like using MVPS Hosts file, changing your DNS provider. Then go to work on removing the actual infection. You could also use something like Bitdefender and enter to recovery console, or install Avast and select boot time scan to run at next boot that's if there's no risk of your MBR getting encrypted. I'd also install a firewall that allows you to block unsafe applications from connecting out such as CF or Windows firewall control. The 10 minutes you'll spend making sure you're hosts file, DNS and Firewall are all keeping your systems connections safe will help a lot when you start using on demand scanners.
I'd run:
Eset online scanner.
Kaspersky virus removal tool.
Malwarebytes.
Hitman pro.
And Norton power eraser.
And yes, I'd run them all because that way you can make sure that anything one product misses another will likely catch.
A rescue disk would be a good move. Either Kaspersky's rescue disk or Bitdefenders rescue disk that's if theres no risk of this encrypting your MBR.
Also run Comodo kill switch and check the VT results, and run auto runs.
The very first thing I'd do in your case is use Bleach bit or CCleaner to remove any and all temporary files and obsolete Reg keys. Then, change your Hosts file, change your DNS provider, make sure you've got a firewall installed that can block unknown and/or Malicious files connecting out. Then start with the on demand scanners. Personally I'd start with Eset online scanner or MBAM.
If this Ransomware doesn't encrypt the MBR start with a rescue disk.
I don't know if this is going to be possible in this case or not, but you could also set up another user account as admin, log into that account and change your normal login account to a standard user. The damage is done now, but you can clean your system, get things running properly again and make sure you system is secure and make sure you're using a firewall that will auto block unknown and malicious files such as CF just until you can get your files encrypted then back them up, then wipe your machine.
All the above along with the advice other people have given should get you to the point where you just need to wait for a dycrption tool for this perticluar ransomware. Just make sure that as soon as youve recovered your files and made sure everything you need to back up is clean to wipe your machine. Person8if it was me and this may be a little paranoid but I'd perform a 0 overwrite then a reformat once you've got your files back.
Are there any other systems on your network that could be at risk?
If I can help in anyway just let me know and I'll be more than happy to help you out even if that means me coming in remotely if that's still possible at this point. If it is just let me know.
Where did this ransomware come from? And what security software did you have installed at the time?
I'm typing on my phone at the moment but I'll be home in 30 minutes so I can jump straight onto my main system and see what the latest developments are in this thread.