- Jan 24, 2011
- 9,378
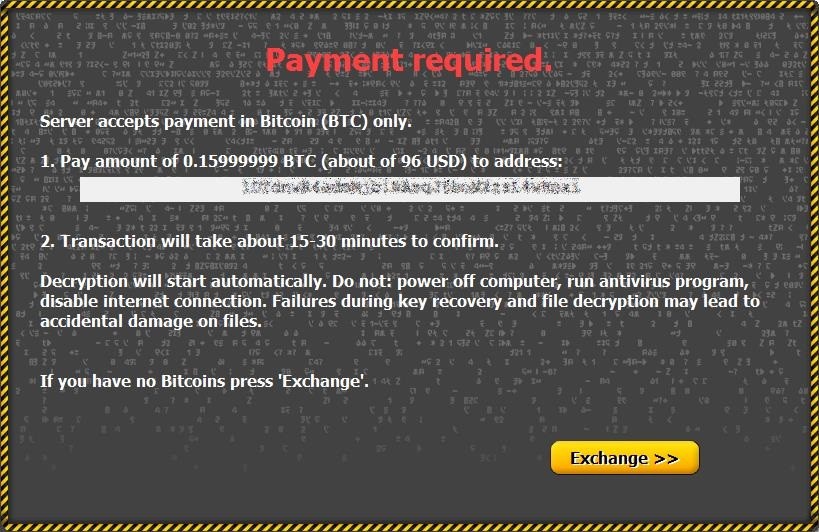
The recently discovered Critoni malware, that relies on a strong encryption method and on TOR network for anonymous communication with the command and control (C&C) server, has been seen to aim primarily at Russian-speaking users.
The sample, analyzed by Kaspersky, sports a number of features that distinguish it from similar file-encrypting malware.
First of all, Critoni, identified by the products of the security firm as “Trojan-Ransom.Win32.Onion,” includes all the necessary code for communication with the C&C server over the TOR (The Onion Router) anonymous network via a separate thread.
Other threats using TOR simply launch the legitimate “tor.exe” file, sometimes injected in other processes, to achieve anonymous communication.
Another particularity is the compression of the targeted files prior to encryption. Each item is moved to a temporary location and they are read one block at a time. The next stage involves compressing each block and then encrypting it.
The result is an encrypted item with the CTLB extension, which has the service information for decryption at the beginning of the file.
Critoni/Onion is also different from malware of the same category in regard to the cryptographic scheme used, since it does not rely on the combination of AES and RSA algorithms, but uses one of the most powerful algorithms, the Elliptic curve Diffie–Hellman (ECDH).
After generating the master public/private encryption keys, each file is locked with a new pair of keys (session public/private) and then the shared secret (session secret) is calculated from the master public and session private. None of the private keys are saved locally, nor is the shared secret.
To better understand the principle, Fedor Sinitsyn of Kaspersky provides the following equality:
ECDH(master-public, session-private) = session-shared = ECDH(master-private, session-public)
As such, the only way to decrypt the data is to have the master private key, which is not available locally but sent after being generated, in a secure manner that relies on the same ECDH principle, to the C&C server of the cybercriminals. The sad conclusion is that the encrypted information cannot be decrypted.
According to telemetry from Kaspersky, most infections are in the Commonwealth of Independent States, Russia being at the top of the list.
Researchers show that on July 20, 2014, the most infected computers were localized in Russia (24), followed by Ukraine (19), Belarus (9) and Kazakhstan (7).
The figures are low at this time, but the new variant is currently just starting to spread, and larger numbers of infected machines are expected in the near future.
Fedor Sinitsyn, who analyzed the new malware strain, says that these results “are provided for the verdict ‘Trojan-Ransom.Win32.Onion’ only. The number of users attacked by the encryptor is in fact greater, as malicious packers with different verdicts are used to spread the malware.”
There are also unknown samples of the encryptor, which are identified with a generic signature name, and these statistics have not been taken into consideration.
Read more: http://news.softpedia.com/news/Crit...ed-Crypto-Malware-Says-Kaspersky-452108.shtml