- May 3, 2011
- 3,893
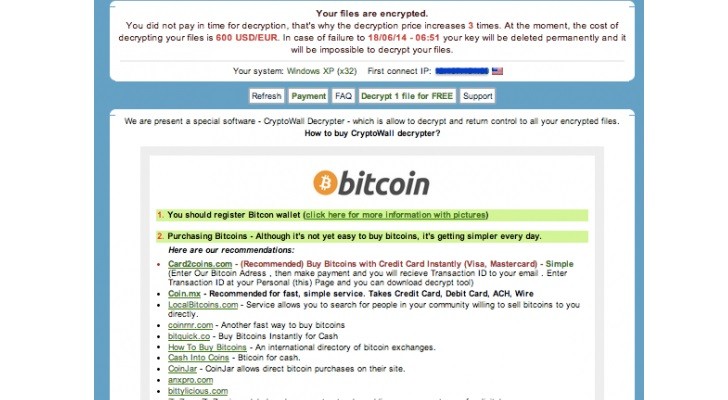
 - Cryptowall ransom message
- Cryptowall ransom messageThe computer system of the police department in Durham, New Hampshire has been infected with Cryptowall, a variant of Cryptodefense ransomware that encrypts data and holds it hostage until money is paid for decrypting it.
Just like in the case of the infamous Cryptolocker, the attack was carried out via email phishing, with the piece of malware disguised into what appeared to be a legitimate file attached to the system.
With Cryptowall loose on the department’s computer system, the affected machines were isolated by being taken offline, to stop the spread and to run disinfection routines.
According to Todd Selig, Town Manager, no ransom is to be paid by the authorities for getting the decryption key, an action recommended by most security experts to discourage data ransom practices of cybercrooks.
This was a fortunate case because the police department had a backup system in place that allows restoring the data. The measure proved to be important because Cryptowall’s encryption cannot be broken.
According to security boffins from Cisco Systems, Cryptowall has been around as part of an exploit kit called RIG since April, when they noticed increased traffic generated by the malicious package and started blocking it.
However, the prevalent attack vector was not email phishing, but advertisements served on numerous sites. Cisco informs that they “blocked requests to over 90 domains.”
Cryptowall targets specific file formats, which include DOC, XLS, and TXT, along with images and videos. The malicious software creates files with instructions to regain access to the content in each folder that holds an encrypted file.
A ransom message is then shown to the user informing that the data can be decrypted by paying a fee, which increases in time.
Source

