Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,458
FIREWALLHARDENING (new ver. 3.0.0.1, July 2024)
FirewallHardening is a part of the Hard_Configurator project and can be used also as a standalone application among a few others included in the H_C_HardeningTools repository:
https://github.com/AndyFul/ConfigureDefender/tree/master/H_C_HardeningTools
FirewallHardening tool can apply and manage Outbound Block Rules in Windows Firewall by using Windows policies. The restart of Windows is required to apply the configuration changes. On Windows 10, the execution of bitsadmin.exe (LOLBin) can be blocked via Windows built-in Exploit Protection ('Disable win32k system calls').
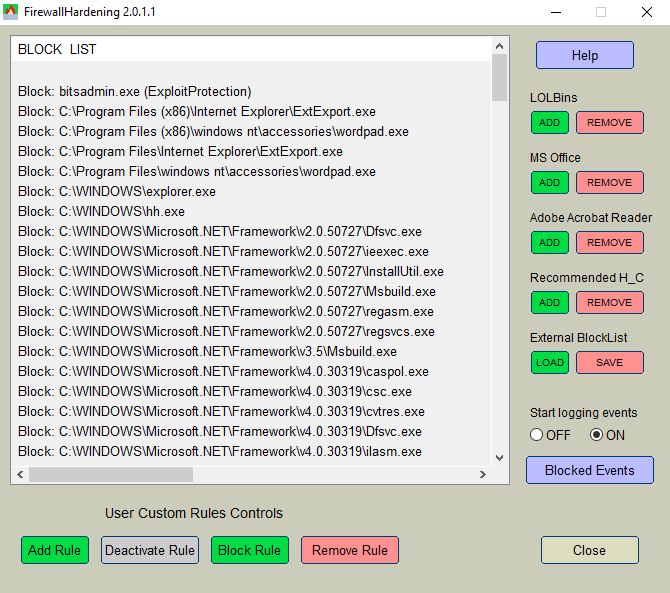
The paths of blocked executables are displayed as a list. Each entry can be managed by using the buttons located at the bottom of the application GUI. The applied rules may be also viewed when using Windows Firewall Advanced settings, but can be managed only by FirewallHardening tool, or by editing the Registry under the key:
User Custom Rules Controls allow the user to manage the rules on the BlockList. Please, use the mouse-click and CTRL key to highlight several items on the BlockList. The block of rules can be selected by using the mouse-click to highlight the beginning of the block and then the combination of <Shift> <Down arrow> to select the block.
<Add Rule> button allows adding the rule for any executable.
<Deactivate Rule> button can make the highlighted rules 'Inactive' on the BlockList, but it does not remove them. If the user does not want to block a particular executable (LOLBin) then the rule should be deactivated, but not removed. The 'Inactive' rule will not be changed when adding/updating the rules.
<Block Rule> button changes highlighted 'Inactive' rules to 'Block' rules.
<Remove Rule> button removes the highlighted rules from the BlockList (and Windows Firewall settings). It can be used to remove the users' custom rules. It should not be used to unblock predefined FirewallHardening rules.
The user can add/remove some predefined rules: 'LOLBins', 'MS Office', 'Adobe Acrobat Reader', 'Recommended H_C'. They are visible on the right of the application GUI.
« 'LOLBins' rules are related to Living Of The Land executables from system folders, which are known to be commonly abused by malc0ders.
« 'MS Office' and 'Adobe Acrobat Reader' rules are related to Word, Excel, PowerPoint, Equation Editor, and Acrobat Reader applications.
« 'Recommended H_C' is a part of 'LOLBins’. These rules are suited to users who installed the Hard_Configurator Windows hardening application and applied the <Recommended Settings>.
Using the FirewallHardening Log of blocked events.
The user can enable auditing Windows Firewall with Advanced Security in the category 'Object Access' and subcategory 'Audit Filtering Platform Connection' (Event Id=5157). This can be done by choosing the radio button 'ON', under 'Start logging events'.
If auditing is enabled, then the blocked events can be filtered from the Windows Security Log by pressing the <Blocked Events> button, visible under the OFF/ON radio buttons. The Security Log can store these events for several hours (usually 48 hours).
Please note, that <Blocked Events> output can show only the events related to the current FirewallHardening BlockRules. After deactivating or removing a particular rule, the blocked events caused by this rule are skipped in the <Blocked Events> output. If the FirewallHardening BlockList is empty or all rules are inactive, then the <Blocked Events> output will not include any blocked event.
Loading and saving BlockLists.
'BlockList' <Load> and <Save> buttons allow using several BlockLists from the *.fhbl files. The new FirewallHardening version is usually published with the file 'UpdateFirewallRules.fhbl' that contains the new rules. Each rule starts with terms: Block : , Inactive : , Block!: , Inactive!:
The exclamation mark means that the file path is not checked, so the rule will be added even if the file does not exist on the disk. The rule without an exclamation mark is checked, and if the file is not on the disk in the required location, the rule will be skipped. But on Windows 32-bit, rules related to Windows 64-bit are always ignored (not loaded), even rules with the exclamation mark.
The rules can include the known Windows environment variables like:
FirewallHardening can also accept a few custom variables like:
It may happen that the rule included in the file 'UpdateFirewallRules.fhbl' may be already on the FirewallHardening BlockList. In such a case the new rule will be skipped. Other new rules are initially added at the end of the FirewallHardening BlockList, but after running the tool a second time all rules are sorted, so the 'Block' rules are at the beginning and 'Inactive' rules are at the end. The 'Inactive' rules are related to LOLBins that are not included in the 'Recommended H_C' preset.
FirewallHardening is a part of the Hard_Configurator project and can be used also as a standalone application among a few others included in the H_C_HardeningTools repository:
https://github.com/AndyFul/ConfigureDefender/tree/master/H_C_HardeningTools
FirewallHardening tool can apply and manage Outbound Block Rules in Windows Firewall by using Windows policies. The restart of Windows is required to apply the configuration changes. On Windows 10, the execution of bitsadmin.exe (LOLBin) can be blocked via Windows built-in Exploit Protection ('Disable win32k system calls').
The paths of blocked executables are displayed as a list. Each entry can be managed by using the buttons located at the bottom of the application GUI. The applied rules may be also viewed when using Windows Firewall Advanced settings, but can be managed only by FirewallHardening tool, or by editing the Registry under the key:
HKLM\SOFTWARE\Policies\Microsoft\WindowsFirewall\FirewallRules
User Custom Rules Controls allow the user to manage the rules on the BlockList. Please, use the mouse-click and CTRL key to highlight several items on the BlockList. The block of rules can be selected by using the mouse-click to highlight the beginning of the block and then the combination of <Shift> <Down arrow> to select the block.
<Add Rule> button allows adding the rule for any executable.
<Deactivate Rule> button can make the highlighted rules 'Inactive' on the BlockList, but it does not remove them. If the user does not want to block a particular executable (LOLBin) then the rule should be deactivated, but not removed. The 'Inactive' rule will not be changed when adding/updating the rules.
<Block Rule> button changes highlighted 'Inactive' rules to 'Block' rules.
<Remove Rule> button removes the highlighted rules from the BlockList (and Windows Firewall settings). It can be used to remove the users' custom rules. It should not be used to unblock predefined FirewallHardening rules.
The user can add/remove some predefined rules: 'LOLBins', 'MS Office', 'Adobe Acrobat Reader', 'Recommended H_C'. They are visible on the right of the application GUI.
« 'LOLBins' rules are related to Living Of The Land executables from system folders, which are known to be commonly abused by malc0ders.
« 'MS Office' and 'Adobe Acrobat Reader' rules are related to Word, Excel, PowerPoint, Equation Editor, and Acrobat Reader applications.
« 'Recommended H_C' is a part of 'LOLBins’. These rules are suited to users who installed the Hard_Configurator Windows hardening application and applied the <Recommended Settings>.
Using the FirewallHardening Log of blocked events.
The user can enable auditing Windows Firewall with Advanced Security in the category 'Object Access' and subcategory 'Audit Filtering Platform Connection' (Event Id=5157). This can be done by choosing the radio button 'ON', under 'Start logging events'.
If auditing is enabled, then the blocked events can be filtered from the Windows Security Log by pressing the <Blocked Events> button, visible under the OFF/ON radio buttons. The Security Log can store these events for several hours (usually 48 hours).
Please note, that <Blocked Events> output can show only the events related to the current FirewallHardening BlockRules. After deactivating or removing a particular rule, the blocked events caused by this rule are skipped in the <Blocked Events> output. If the FirewallHardening BlockList is empty or all rules are inactive, then the <Blocked Events> output will not include any blocked event.
Loading and saving BlockLists.
'BlockList' <Load> and <Save> buttons allow using several BlockLists from the *.fhbl files. The new FirewallHardening version is usually published with the file 'UpdateFirewallRules.fhbl' that contains the new rules. Each rule starts with terms: Block : , Inactive : , Block!: , Inactive!:
The exclamation mark means that the file path is not checked, so the rule will be added even if the file does not exist on the disk. The rule without an exclamation mark is checked, and if the file is not on the disk in the required location, the rule will be skipped. But on Windows 32-bit, rules related to Windows 64-bit are always ignored (not loaded), even rules with the exclamation mark.
The rules can include the known Windows environment variables like:
%SystemRoot%
%ProgramData%
%ProgramFiles%
%ProgramFiles(x86)%
%SystemDrive%
FirewallHardening can also accept a few custom variables like:
%System32% (usually C:\Windows\System32),
%SysWOW64% (usually C:\Windows\SysWOW64),
%Framework% (usually C:\Windows\Microsoft.NET\Framework),
%Framework64% (usually C:\Windows\Microsoft.NET\Framework64),
%PowerShell% (usually C:\Windows\System32\WindowsPowerShell\v1.0),
%PowerShell64% (usually C:\Windows\SysWOW64\WindowsPowerShell\v1.0)
It may happen that the rule included in the file 'UpdateFirewallRules.fhbl' may be already on the FirewallHardening BlockList. In such a case the new rule will be skipped. Other new rules are initially added at the end of the FirewallHardening BlockList, but after running the tool a second time all rules are sorted, so the 'Block' rules are at the beginning and 'Inactive' rules are at the end. The 'Inactive' rules are related to LOLBins that are not included in the 'Recommended H_C' preset.
Last edited:



