- Feb 7, 2023
- 2,351
This thread provides release notes for Harmony Endpoint, Infinity Portal and Threat Emulation Engines.
Harmony Endpoint for Windows Client version 87.30 released 9th of May 2023.
Harmony Endpoint for Mac Client version 87.40 released 11th of June 2023
Harmony Endpoint and Infinity Portal Improvements Delivered in First Half of 2023
 community.checkpoint.com
community.checkpoint.com
Threat Emulation Engine:
Release 11.05 from 15th of May 2023
Early Availability:
Smart Exclusions
 community.checkpoint.com
community.checkpoint.com
Harmony Endpoint for Windows Client version 87.30 released 9th of May 2023.
- Added Low Memory Mode, which reduces memory consumption.
- Added Built-in Help to the client UI.
- Added Client Demo and Health Check. The client will open the default browser on a page with various tests for client protections.
- Client notifications are now adapted to high resolution monitors.
- It is now possible to configure the Anti-Malware "Scan On Idle" feature via Endpoint Management.
- Endpoint Client Posture Management support for on-demand installation of patches from the Server is now available for Early Availability (EA) customers.
- Improved interoperability with cloud drives (in Endpoint Security client) and improved handling of exceptions for trusted processes in the Authorization scanning feature.
- Windows update will now be blocked when the firmware boots the computer incorrectly. This prevents Full Disk Encryption blade from crashing during the OS update.
- If some parameter in the trac.defaults file was modified, its new value will now be migrated during the VPN client upgrade.
- New value “default_browser” is available for the “idp_browser_mode” parameter in the trac.defaults file. When this value is set, the default system browser will now be used for SAML-based authentication.
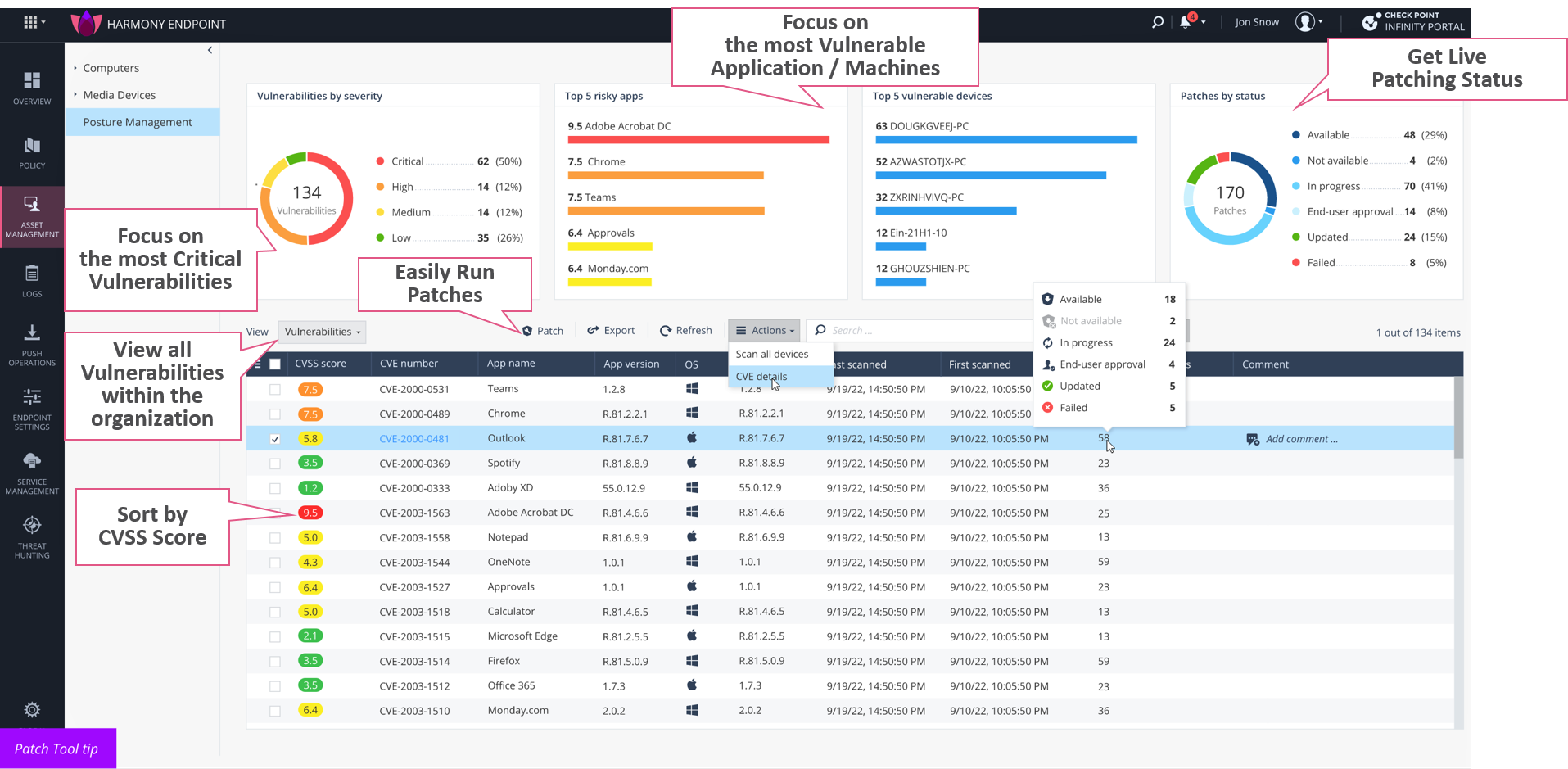
- Posture Management Vulnerability Assessment is now available on macOS for Early Availability (EA) customers. It reduces the attack surface through accurate assessment of vulnerabilities, risky applications, and computers within the organization.
- It is possible now to customize the policy to prevent the installation of the Browser extension on a specific browser, even if Threat Emulation blade is enabled.
- Endpoint Security Browser Extension for macOS with Zero Phishing, Threat Emulation, Threat Extraction and URL Filtering blades is now supported in the Brave browser and Edge browser.
- Admins can now force pinning of the Endpoint Security browser extension in Chromium-based browsers (Chrome, Brave and Edge).

Harmony Endpoint - H1 2023 Product Enhancements
Hi 2023 was a busy year so far, we thought it would be cool to share our latest product enhancements with you. Please see the attached file with our 2023 H1 deliveries – With a deep-dive explanation of our newest capabilities. Posture Management: Customized Dashboard: Widget Catalog...
Threat Emulation Engine:
Release 11.05 from 15th of May 2023
- Threat Emulation now includes a new engine that is capable of statically deobfuscate office files and convicting them faster than before.
- Potential crashes in executable emulations have been fixed.
Early Availability:
Smart Exclusions

Introducing - Smart Exclusion (EA)
We are very happy to announce “Smart Exclusion”! Our new Smart Exclusion is available for EA customers! With this new enhancement, we can save customers 80% of their time spent on creating, deleting, and managing exclusions. You can see more details in the attached demo & attached deck. Please...



