- Dec 23, 2014
- 8,458
@danb,
I used your POC Test1. After running the shortcut Windows tried to open the ping .png as a photo. I checked this with my shortcut and noticed one difference. In my shortcut the default folder entry is empty and in your shortcut, it is C:\Windows\system32. When I added this path to my shortcut it also tried to open the file as a photo. After removing the folder path from your shortcut it bypassed the command-line check as my shortcut.
I corrected my previous post to include the empty default folder path.
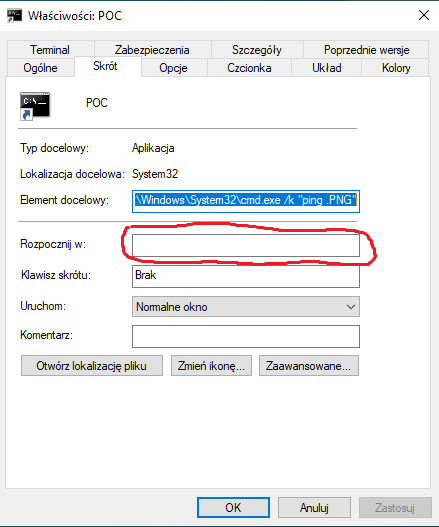
I used your POC Test1. After running the shortcut Windows tried to open the ping .png as a photo. I checked this with my shortcut and noticed one difference. In my shortcut the default folder entry is empty and in your shortcut, it is C:\Windows\system32. When I added this path to my shortcut it also tried to open the file as a photo. After removing the folder path from your shortcut it bypassed the command-line check as my shortcut.
I corrected my previous post to include the empty default folder path.
Last edited: