Phishing emails have become a common method used by cybercriminals to deceive unsuspecting individuals and gain access to their personal information. One particular type of phishing email that has been circulating recently is the ‘Explain Us About This Unusual Activity’ phishing email. In this article, we will delve into what this phishing email is, how the scam works, what to do if you have fallen victim, technical details, and statistics to support our points.

What is the ‘Explain Us About This Unusual Activity’ Phishing Email?
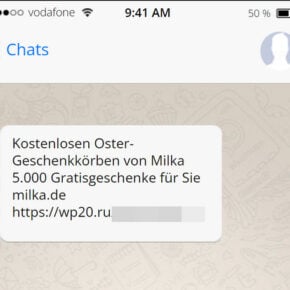
The ‘Explain Us About This Unusual Activity’ phishing email is a fraudulent email that is designed to trick recipients into believing that their account has been compromised or involved in suspicious activities. The email typically appears to be sent from a reputable organization, such as a bank, online payment platform, or social media platform.
The email often includes a sense of urgency, urging the recipient to take immediate action to resolve the alleged issue. It may claim that the recipient’s account has been locked or suspended due to suspicious activity and that they need to verify their account information to regain access.
How Does the Scam Work?
Once a recipient falls for the scam and clicks on the link provided in the email, they are directed to a fake website that closely resembles the legitimate website of the organization being impersonated. The fake website is designed to trick users into entering their login credentials or other sensitive information.
Once the user enters their information, it is captured by the cybercriminals behind the scam. This information can then be used for various malicious purposes, such as identity theft, unauthorized access to financial accounts, or even selling the information on the dark web.
Example:
Let’s consider an example to illustrate how the ‘Explain Us About This Unusual Activity’ phishing email scam works:
- The recipient receives an email that appears to be from their bank, claiming that there has been unusual activity on their account.
- The email states that the recipient’s account has been temporarily locked and provides a link to resolve the issue.
- The recipient, concerned about their account’s security, clicks on the link.
- The link takes them to a fake website that looks identical to the bank’s official website.
- The recipient is prompted to enter their login credentials and other personal information.
- Unbeknownst to the recipient, their information is captured by the cybercriminals.
What to Do If You Have Fallen Victim?
If you have fallen victim to the ‘Explain Us About This Unusual Activity’ phishing email scam, it is crucial to take immediate action to minimize the potential damage:
- Change your passwords: Start by changing the passwords for the affected accounts. Ensure that you create strong, unique passwords that are not easily guessable.
- Contact the organization: Reach out to the legitimate organization being impersonated in the phishing email and inform them about the incident. They can provide guidance on further steps to take and may be able to assist in securing your account.
- Monitor your accounts: Keep a close eye on your financial accounts, credit reports, and any other accounts that may have been compromised. Look for any suspicious activity and report it immediately.
- Scan for malware: Run a scan with a reputable antivirus or anti-malware software, such as Malwarebytes Free, to ensure that your device is not infected with any malicious software.
- Be cautious in the future: Learn from the experience and be more vigilant when it comes to emails and online communications. Be skeptical of any email that asks for personal information or urges immediate action.
Technical Details of the ‘Explain Us About This Unusual Activity’ Phishing Email
The ‘Explain Us About This Unusual Activity’ phishing email is often crafted using advanced techniques to make it appear legitimate. Here are some technical details to be aware of:
- Email spoofing: The email may appear to be sent from a legitimate email address, but it is actually spoofed. Cybercriminals can manipulate the email headers to make it seem like the email is coming from a trusted source.
- Domain spoofing: The link provided in the email may use a domain name that closely resembles the legitimate organization’s domain. However, upon closer inspection, there may be slight variations or misspellings.
- Malicious attachments: Some phishing emails may include attachments that contain malware or viruses. These attachments are often disguised as important documents or invoices, enticing the recipient to open them.
- Social engineering techniques: Phishing emails often employ psychological manipulation to trick recipients into taking action. They may use fear, urgency, or curiosity to prompt the recipient to click on the malicious link or provide their personal information.
Statistics on Phishing Attacks
Phishing attacks, including the ‘Explain Us About This Unusual Activity’ phishing email, continue to be a significant threat in the digital landscape. Here are some statistics that highlight the prevalence and impact of phishing attacks:
- According to the 2021 Verizon Data Breach Investigations Report, phishing was the most common type of social engineering attack, accounting for 36% of all breaches.
- In 2020, the Anti-Phishing Working Group (APWG) reported a 22% increase in phishing websites compared to the previous year.
- A study conducted by Google found that 45% of phishing attacks targeted individuals in the financial industry, while 13% targeted individuals in the technology sector.
- According to the FBI’s Internet Crime Complaint Center (IC3), phishing scams resulted in over $54 million in losses in 2020.
Summary
The ‘Explain Us About This Unusual Activity’ phishing email is a deceptive tactic used by cybercriminals to trick individuals into divulging their personal information. It is crucial to be aware of this scam and take necessary precautions to protect yourself.
If you receive an email claiming unusual


![Remove EliteSearchEApp.com Redirect [Virus Removal Guide] 9 1 1](https://malwaretips.com/blogs/wp-content/uploads/2023/10/1-1-290x290.jpg)