A deceitful clearance scam targeting popular baby brand Chicco has emerged, heavily promoted through sponsored social media posts. The compelling advertisements promise jaw-dropping discounts of up to 90% off all Chicco products. However, unsuspecting parents who click find themselves rerouted to sophisticated but fraudulent websites impersonating the real company.
- Overview of the Fraudulent Chicco Clearance Sale Scam
- How the Chicco Clearance Scam Works to Deceive and Defraud Customers
- Spotting Fraudulent Websites Promoting Fake Chicco Clearance Sales
- Identifying Scam Chicco Ads on Social Media
- What to Do If You Got Scammed By a Fake Chicco Website
- Frequently Asked Questions to Demystify the Fake Chicco Clearance Scam
- The Bottom Line
This article unravels how the elaborate swindle works, how to avoid becoming victimized, and what to do if you already got scammed.
Overview of the Fraudulent Chicco Clearance Sale Scam
In recent months, a surge of social media ads promoting unbelievable Chicco deals has bombarded platforms like Facebook, Instagram and TikTok. The eye-catching posts feature images of strollers, car seats, baby bottles and other popular Chicco items all marked down up to 90% off.
Attention-grabbing slogans also hype once-in-a-lifetime limited-time offers with calls-to-action trying to create intense fear of missing out on amazing savings. “Today Only – Entire Site 75% Off!” and “Going out of Business Sale!” typify the extreme tactics used to whip shoppers into frenzies.
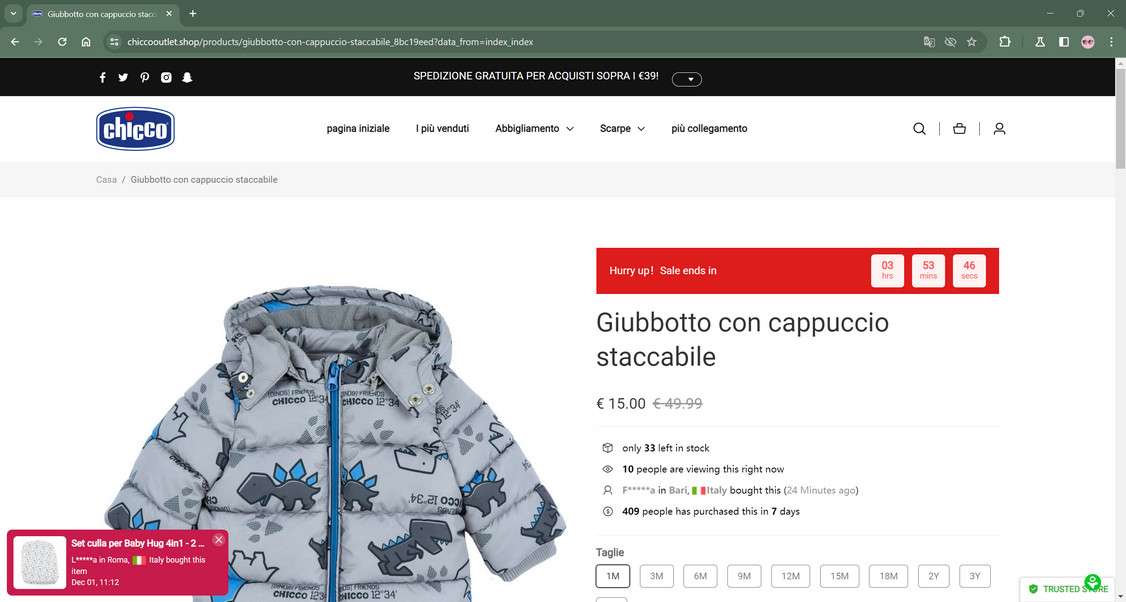
However parents who click expecting real Chicco liquidation events instead get rerouted to fake but very convincing imposter websites that closely mimic the look and feel of the genuine Chicco.com store.
Behind the elaborate deception rests crime rings in China running networks of fraudulent shops targeting Western baby brands through mountain high discounts that lure bargain-seeking parents.
How the Chicco Clearance Scam Works to Deceive and Defraud Customers
The organized scam operations employ sophisticated strategies maximizing both social media and fake ecommerce stores working hand-in-hand to confuse consumers and steal money.
Step 1: Creating Networks of Highly-Convincing Phony Sites
The foundation centers on assembling chains of sham websites emulating trusted retailers. Research reveals the China-based groups have been methodically scrapping and cloning elements of baby brand sites including images, branding materials, and product catalogs.
Their duplicate “Chicco” online shops adeptly replicate the look, feel and functionality of the genuine store. To unwitting consumers first arriving, extremely few initial red flags indicate anything dubious behind the website. Without seeing any obvious misspellings or errors, visitors browse what resembles a familiar ecommerce store.
Yet behind the facade hides multiple deceitful motives:
- Collect payments but ship nothing – the most common outcome scamming customers
- Distribute damaged, inferior or incorrect items
- Steal personal data for identity fraud
- Launder money to shady criminal enterprises
Step 2: Driving Traffic Through Social Media Trickery
The core scheme relies on attracting online shoppers onto the fraudulent websites through aggressive social media marketing pushes. Compelling ads touting clearance discount events specifically target platforms swarming with deal-hunting parents.
These digital ads are the key bait driving traffic precisely into traps set by deceptive websites ready to ambush visitors via tactical psychological manipulation and technical trickery.
Both precise consumer targeting options and the ad content itself tries capitalizing on common Shopping biases and cognitive lapses:
- Appealing Prices – Jaw-dropping discounts up to 90% exploit the irresistible lure of obtaining amazing value.
- Purchase Urgency – Taglines like “Going Out of Business Sale!” trigger fear over the prospect of missing scarcely available deals.
- Social Proof – Ads and websites display fictitious declarations like “Millions in Sales This Week!” to fabricate peer consensus.
- Familiarity Pretext – Brand visual assets used without permission falsely convey official endorsements.
Through ads directly speaking to parental yearnings for better prices on costly baby essentials, the scam machines whip up excitement and instill willingness to impulsively click links without fully rational scrutiny.
Step 3: Stealing Identities, Funds and Crushing Dreams
When lured victims access the swindle sites and eagerly start piling marked-down items into their carts, eventually they reach checkout phases. Here the criminal plot pivots from gentle persuasion to outright extortion.
To finalize orders, the sites force visitors to submit extensive personal details including:
- Full names, home addresses, contact info
- Payment types, credit card and account numbers
- Billing information, security codes and expiration dates
Victims willingly hand over information without realizing it will never result in cheaper baby products. Instead, most buyers end up utterly scammed through one of following outcomes after order “confirmation”:
- No items ever ship – By far the most frequent result, duped shoppers receive nothing despite payments successfully processing. Funds get pocked while hopes get crushed.
- Shoddy, inferior knockoffs arrive – Some unlucky parents receive abysmally poor-quality fakes made with flimsy materials unlike advertised.
- Used, damaged or hazardous items get delivered – In some egregious cases, victims report items arrive clearly used, broken or containing concerning defects making them dangerous for infants.
- Random wrong products appear – Some buyers receive arbitrary items utterly unrelated to original order possibly shipped cheaply in bulk from other scam schemes.
Yet worse than wasting money and receiving nothing, the true injury emerges later when criminals weaponize the stolen data and identities. Swindled users soon encounter added misery through:
- Stolen funds getting drained from bank accounts
- Spiking credit card statements from fraudulent purchases
- Identity theft leading to destroyed credit reports
- Accounts illegally opened using victims’ names and data
Through weeks of emotional turmoil and financial wreckage from single moments of quick clicks lured by savings, dreams of parenting with less financial burden transform into nightmares.
Spotting Fraudulent Websites Promoting Fake Chicco Clearance Sales
Although the bogus Chicco shopping websites appear very convincing initially through stolen branding assets and product imagery, several consistent red flags across these scam platforms empower eagle-eyed shoppers to evade surrendering hard-earned money or sensitive personal data due to unbelievable price cut promotions.
Carefully dissecting website components and questioning validity of extraordinarily deep discounts allows parents to steer clear of potential identity theft dangers while seeking deals on baby essentials.
Auditing Domain Registration Histories
A quick check of domain ownership dates using ICANN lookup tools reveals insightful patterns. Responsible retailers build branded sites intending lengthy lifespans serving customers. Hastily registered domains signal temporarily sham operations. Telltale signs include:
- Domains created within past 1-3 months aiming to capitalize on clearance hype before discovery
- Short ownership durations under 2 years that suggest fly-by-night scam fronts quickly abandoned
- Usage of proxy registration services hiding owners’ true identities
Authentication of Deep Discount Claims
While occasional sales prove common, knowledgeable parents know even beloved brands rarely slash prices past 50-75% thresholds simultaneously across all product lines without valid explanations like inventory overstocks.
Thus view sitewide advertised markdowns hitting 90% automatically with extreme suspicion regardless of company trust or loyalty. Such deals likely indicate outright scams rather than authentic promotions.
Moreover, legitimate limited-time deals highlighted consistently across multiple official advertising channels including social media profiles, websites, direct mailers and email lists.
Deals promoted exclusively through third party media but omit official site mentions indicate likely bait without consistency.
Assessing Company Digital Presence
Unlike short-lived scam websites relying entirely upon mimicking visual branding of trusted retailers, legitimate brands dedicate tremendous efforts building robust multimedia presences highlighting positive sentiments earned from years serving satisfied parents across various platforms.
Thus search rigorously for independent third-party communities and discourse affirming high credibility through authentic reviews, testimonials and demonstrable press coverage. Lack of such artifacts rightfully builds wariness over business legitimacy.
Verifying Company Contact Information
A quick check on provided business details reveals actual legitimacy. Easily contact live personnel willing to openly share backgrounds regarding executive teams, locations and other fundamental corporate descriptors that reputable companies display prominently.
- Unanswered calls and emails bounced back due to fake addresses provide obvious red flags
- Details unwillingly shared signal insincere ploys
With sharpened scrutiny across subtle but consistent patterns found on online clearance scams, informed shoppers can effectively expose disingenuous offers and fraudulent vendors seeking to trick eager visitors.
Identifying Scam Chicco Ads on Social Media
In addition to creating entire fake ecommerce stores, the criminal ring behind the fraudulent Chicco clearance sales leverages sponsored social media ads to target deal-seeking users and drive traffic to their scam websites.
Highly compelling posts explicitly promoting unbelievable discounts frequently appear in Facebook feeds, Instagram Stories and Explore pages, and TikTok streams. While seeming legitimate, certain patterns expose their deceitful intentions.
Spotting Sham Facebook Ads
Facebook allows extensive ad targeting options and fraudsters exploit these to precision target ads by interest keywords including “clearance sales,” “limited time offers,” and of course “Chicco discounts.”
Some common features helping distinguish scam Chicco Facebook ads include:
- Exceptionally decreased prices like “Entire Store 90% Off!” trying luring shoppers based on extreme FOMO.
- Urgency messaging like “Going Out of Business Sale – Today Only!” also preys on fear-of-missing bargains.
- Links routing through multiple redirects rather than directly to a retailer website.
- Landing site URLs not containing the actual brand name (e.g. “boutiquestoresale” vs “Chicco”).
- Ad accounts consistently change names to avoid bans once scam gets reported.
Identifying Fraudulent Instagram Ads
- Heavy use of stock photos rather than real brand imagery due to lack of official approval.
- Tagged posts primarily target middle-aged women based on the brand’s core demographic.
- Video clips rely on clips ripped from authentic brand promos then edited to include scammy text overlays and urgency music.
- Accounts repeatedly change handles once reported but continue running near-identical ads.
Spotting Sham TikTok Ads
- Video ads lifted from vintage brand content now overlaid with huge animated text and arrows highlighting clearance event.
- Constant rotation of new accounts to keep scam ads flowing as previous accounts get banned.
- Designed to trigger intrigue and urgency with rapidly flashing “Last Chance!” messages while displaying massive ~90% discount badges.
With awareness of these common social media scam ad patterns on major platforms, savvy social media users can more readily identify fraudulent Chicco promotions and steer clear of harm.
What to Do If You Got Scammed By a Fake Chicco Website
For victims of online shopping scams, the initial realization induces shock and denial. But accepting quickly what happened proves essential to rapidly protecting assets before fraud worsens. Should you become ensnared by a fake Chicco website demanding money and data, promptly initiate these steps:
Step 1: Contact Financial Institutions to Freeze All Accounts
Since swindlers now possess your sensitive information, immediately call every banking and lending provider to report identity theft. Update contact info for enhanced monitoring and freeze credit lines to block criminals from illegally opening additional accounts. Sign-up for dark web surveillance services to monitor online black markets where personal data gets traded and sold.
Step 2: Monitor All Accounts Closely for Unusual Activity
Carefully scrutinize banking and credit accounts over upcoming weeks ready to spot unauthorized charges. Cyber thieves frequently delay using stolen funds in hopes of avoiding detection, so look for unfamiliar account logins, transfers, withdrawals or bonuses. Ensure also that no services appear opened without your permission like loans, cards or memberships. Remain hyper vigilant across digital life for months following data loss.
Step 3: File Reports on All Aspects of the Fraudulent Event
Submit detailed scam complaints conveying your experience to public consumer protection agencies like BBB Scam Tracker, FTC Complaint Assistant and IC3. Provide also copies to local law enforcement agencies for documenting an official fraud report when disputing damages from identity theft later. Include information on scam websites, social media accounts that promoted them and any companies that brands got stolen through unauthorized use.
Step 4: Begin Dispute and Reimbursement Proceedings
Immediately contact credit card providers and banks to report all transactions with fake websites as fraudulent. Demand they start dispute proceedings, chargebacks and reimbursements right away for any stolen funds. Monitor closely for denial reasons and re-submit updated dispute forms continually until achieving favorable judgment.
Follow a regular routine checking all statements and reporting suspicious charges until all traces of fraud eventually minimize. And crucially, avoid clicking social media clearance deals in the future before thoroughly vetting legitimacy, no matter how spectacular the savings.
Frequently Asked Questions to Demystify the Fake Chicco Clearance Scam
For concerned parents questioning the curious case of too-good-to-be-true Chicco sales permeating social feeds, this FAQ presents simple answers surrounding the rampant swindle and tactics used by scammers to deceive families.
What makes the sham Chicco deals so deceptive for online shoppers?
Fraudsters construct completely fake ecommerce stores impersonating the real Chicco site by perfectly mirroring visual design elements like logo usage, product images and brand textures to suspend visitor disbelief. Scammers also utilize precision-targeted social media advertisements optimized to entice key parent demographics by interest keywords including “baby deals,” “discounted essentials” and “clearance sales events”.
How are the fraudulent websites named?
Scam site domains typically incorporate slight misspellings or abbreviations of the authentic Chicco name. Examples include “Chiccco”, “ChiccosStore” or “ChiccoOutlet”. Minor tweaks aim to confuse visitors through subtly while still benefiting from brand familiarity.
Why do scammers promote such unbelievable discounts up to 90% off?
By advertising exaggerated yet still believable deals, fraudsters exploit cognitive weaknesses that extreme clearances ignite surrounding sales urgency and fear-of-missing bargains which compel hurried purchases before imagined product stockouts.
Does merchandise shown in advertisements actually get sold at scam sites?
No. All product imagery gets stolen from authentic brand catalogs. Scam operators never possess real inventory so nothing gets sold at any price despite displays showing items with steep discounts.
What typically happens after submitting orders at counterfeit sites?
Most victims only lose money as payments get collected but no products ship. In some cases knockoff items arrive, used goods get delivered, or random inexpensive products like electronics instead of actual baby items get sent to maintain loose appearance of legitimacy.
Can customers get scammed without even making purchases?
Yes. Merely accessing fake sites allows device infections from embedded malware redirects that steal data. Entering contact info like emails also flags victims for more spam messages.
How do criminals monetize these shopping scams?
Fraudsters directly profit by pocketing payments from duped shoppers. But larger gains come from reselling stolen personal and financial data on black markets to shadier entities who utilize identities to commit further theft.
Who orchestrates such widespread retail cons against baby brands?
Sophisticated cybercrime rings based largely in China specialize in mass counterfeiting and online fraud. By reverse-engineering legal shopping sites then duplicating at scale, coordinated teams cleanly siphon assets indirectly back to ringleaders often operating internationally to avoid capture.
How long do these baby merchandise scams usually operate before getting shut down?
Weeks or months often pass before sites get blacklisted and removed once discovered. However owners simply modify site details, register new domains and launch redesigned scams in endless cycles targeting the same in-demand brands.
The Bottom Line
In summary, elaborately deceptive clearance sale scams impersonating trusted baby brands like Chicco have emerged to target bargain-seeking parents across social channels. Highly convincing fake website and ads promote jaw-dropping yet unbelievable deals aiming primarily to siphon money and data rather than actual products at discounts.
By learning common patterns these fraudulent operations follow, consumers can more easily identify sham offers and outlets before getting duped. With extra vigilance and rational skepticism assessing deals that feel too good to be true, savvy shoppers can thwart ambushes from criminal teams weaponizing false savings.



