A new viral extortion scam has been making the rounds through spam emails, attempting to extort money from victims by claiming their computer was hacked. The email claims to be from a hacker group called “HazardCC” and threatens to expose private information and adult site browsing history if payment isn’t received.
This type of online extortion scheme has become increasingly common, often using shocking claims and scare tactics to coerce victims into complying. However, following the demands only makes you vulnerable to further extortion attempts.
This article will provide an in-depth look at how the “HazardCC hacker” extortion scam works, what information is really at risk, and most importantly, how to protect yourself from falling victim.
Overview of the Scam
This viral extortion scheme starts with an email claiming to be from the HazardCC hacker group. The message states that they hacked one of your email or social media accounts by exploiting vulnerabilities in a website or app’s servers.
The email goes on to say that through this alleged hack, they installed malware on your phone or computer without your knowledge. This malware supposedly allows them to access your device’s camera, microphone, contacts, instant messaging apps, emails, and browsing history.
According to the scam email, the supposed hackers have been spying on you through your device’s camera and recording your activity. The message claims they have compromising videos of you watching adult content online.
These videos, along with your private conversations and browsing history, are threatened to be sent to all your email and social media contacts if you don’t pay the ransom demanded. This type of online extortion scheme is known as porn blackmail or sextortion.
The email gives a short deadline of around 24-48 hours to pay the ransom, which is demanded in the difficult to trace cryptocurrency Bitcoin. The scammers threaten that if the ransom is not paid in time, the videos and information will be immediately sent to your contacts.
These types of sextortion scams prey on victims’ fears that embarrassing browsing history could be made public to their friends, family, coworkers, and contacts. The scammers exploit feelings of shame, anxiety, and desperation in their victims.
In reality, the likelihood that your device was hacked or compromised based solely on an email from an unknown sender is extremely low. Security experts emphasize these claims of remote hacking, access to accounts, and recording through your camera are completely fabricated.
The scammers behind these schemes rely on the innate discomfort and fear around compromising material being leaked. By threatening exposure, they create an urgent desire in victims to comply with payment demands.
However, the scammers have no proof that any adult content of you exists. There is no leverage over victims aside from false claims designed to install fear. The threats being made through these scam emails are completely empty.
Unfortunately, many victims of sextortion scams are too scared or embarrassed to go to the authorities. Out of fear of exposure, they quietly give in to ransom demands, which only further enables these criminal schemes to spread.
Being informed on common online extortion tactics helps protect yourself and others from falling victim out of knee-jerk reactions. Avoiding reactionary steps like paying the ransom reduces the power these scammers wield through intimidation tactics.
Here is how this email scam looks:
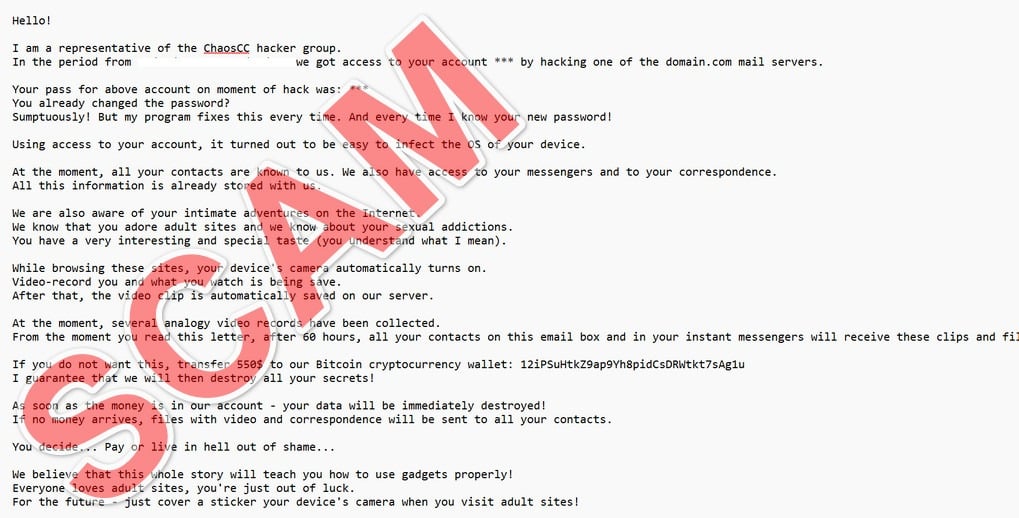
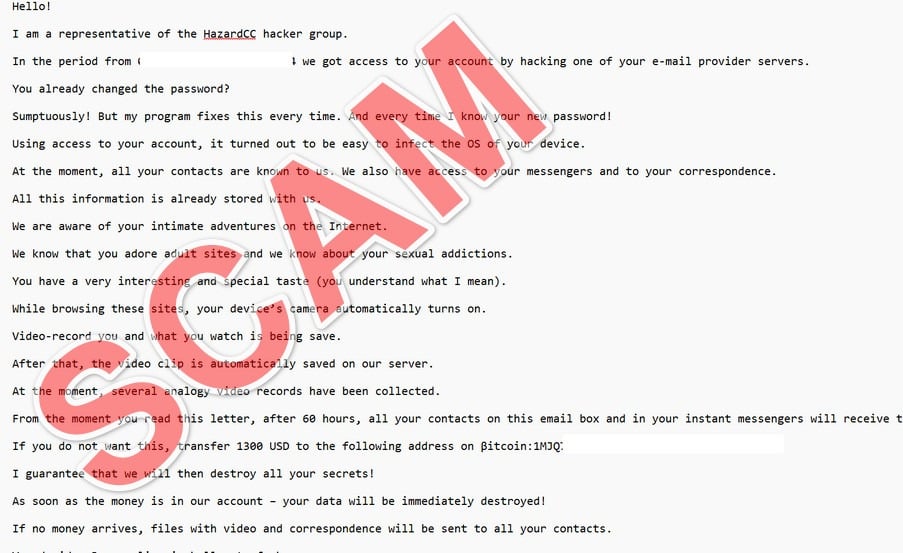
Hello!
I am a representative of the HazardCC hacker group.
In the period from [edited] we got access to your account by hacking one of your e-mail provider servers.
You already changed the password?
Sumptuously! But my program fixes this every time. And every time I know your new password!
Using access to your account, it turned out to be easy to infect the OS of your device.
At the moment, all your contacts are known to us. We also have access to your messengers and to your correspondence.
All this information is already stored with us.
We are aware of your intimate adventures on the Internet.
We know that you adore adult sites and we know about your sexual addictions.
You have a very interesting and special taste (you understand what I mean).
While browsing these sites, your device’s camera automatically turns on.
Video-record you and what you watch is being save.
After that, the video clip is automatically saved on our server.
At the moment, several analogy video records have been collected.
From the moment you read this letter, after 60 hours, all your contacts on this email box and in your instant messengers will receive these clips and files with your correspondence.
If you do not want this, transfer 1300 USD to the following address on βitcoin:1MJQ71oStdEmK7wh7chhAigfF17oFUrMaD
I guarantee that we will then destroy all your secrets!
As soon as the money is in our account – your data will be immediately destroyed!
If no money arrives, files with video and correspondence will be sent to all your contacts.
You decide… Pay or live in hell out of shame…
We believe that this whole story will teach you how to use gadgets properly!
Everyone loves adult sites, you’re just out of luck.
For the future – just cover a sticker your device’s camera when you visit adult sites!
Take care of yourself!
How the Scam Works
The scammers behind this scheme rely on fear and urgency to prevent critical thinking. By walking through how the scam operates, you can see how the claims don’t hold up to scrutiny.
Step 1: Mass Spam Emails Sent Out
The first step is spreading the scam as widely as possible through mass spam emails. The messages are sent from throwaway email accounts through botnets of infected computers. Millions of messages can be sent per day, aiming to reach as large a pool of potential victims as possible.
Step 2: Baseless Claims of Hacking and Spying
The email uses shocking claims of remote hacking, access to your accounts, and recording through your webcam to install fear. However, these claims are completely fabricated. The scammers have no evidence that your device was hacked or that any compromising videos exist.
Step 3: Threats to Release Sensitive Info
By threatening to send adult site browsing history and recordings to all your contacts, the scammers create extreme pressure. Their threats imply they have sensitive and embarrassing information about you, urging you to pay up. In reality, the scammers have no such information.
Step 4: Short Timeframe to Pay Ransom
The scammers give a limited window of 60 hours to pay the ransom before they claim the threats will be carried out. This creates urgency, hoping victims will pay out of fear. If you take time to think it through, their lack of actual leverage becomes clear.
Step 5: Demand for Payment Via Bitcoin
Payment is demanded through Bitcoin, an irreversible cryptocurrency. This makes tracking or recovering payments nearly impossible. Victims who pay have little hope of recouping their money, while the scammers enjoy anonymity.
As you can see, breaking down each step shows that the scammers have no actual means to follow through on their threats of exposing compromising information about you. Their only leverage is smoke and mirrors.
What to Do If You Receive This Email Scam
If you receive an email claiming to be from HazardCC hackers, stay calm and avoid acting rashly out of fear. Take the following steps:
- Do not reply or reach out to the sender in any way. Ignore all communications. Replying confirms you’re a viable target.
- Do not pay anything. Paying any ransom reinforces their scam and could leave you vulnerable to further extortion.
- Check login activity on your accounts. Use account activity to spot any unauthorized access. Update passwords if concerned.
- Run a malware scan on your devices using a trusted antivirus program to check for infections or remote access capabilities.
- Contact the FBI’s Internet Crime Complaint Center to report the scam attempt. Provide email headers and screenshots.
- Notify contacts about the scam if emails are sent to them. Advise them not to open emails from unknown senders.
- File a report with the Anti-Phishing Working Group, providing the malicious email via their online form.
- Block the sender’s email address and ignore any further contact. Delete the scam email to protect yourself from accidental clicks.
The most important step is not giving into fear. The scammers create leverage purely through psychological manipulation, not any actual compromising material. Avoid reactionary steps like paying ransoms and you greatly lower any risks from this scam.
Frequently Asked Questions About the HazardCC Sextortion Scam
1. How do I know if the HazardCC email I received is a scam?
The claims made in the HazardCC extortion email about hacking your device or accounts are completely fabricated. The scammers have no actual proof or access to compromising material as claimed. Threats of leaking videos or information are empty scare tactics meant to extort money.
Other signs it’s a scam: demanding untraceable payment like Bitcoin, threats of immediate harm if you don’t pay quickly, and claiming they can see through your webcam. Real hackers don’t announce themselves or make public threats.
2. What information do the scammers really have about me?
The scammers do not actually have any nude photos/videos, recordings, or access to your online accounts. The claims in their email are false, meant to install fear that private material could leak. No real hacking has occurred.
Your information is not at risk since the scammers have nothing to expose. Do not pay their ransom, as this only funds criminal activity while providing no actual protection of your information.
3. Could my computer really be hacked through visiting adult sites?
It is highly unlikely. While malicious ads/links can exist on adult sites, merely visiting the sites does not give hackers access to your camera, data, or device. Modern operating systems prevent unauthorized access to your webcam.
Run malware scans with security software to check for viruses, but rest assured the HazardCC hackers have no actual access. Visiting adult sites does not directly lead to device takeover.
4. I’m scared my contacts will see the videos. Should I pay?
We understand the fear, but rest assured the scammers have no such videos in their possession. Paying any ransom both funds criminal operations and could open you up to further extortion attempts.
Your information remains secure, so try not to act rashly out of fear. Notify contacts about ignoring suspicious emails instead of giving in to demands.
5. How can I protect myself from this happening again?
- Never click links or open attachments from unknown senders
- Use strong, unique passwords on all accounts and enable two-factor authentication when possible
- Install comprehensive security software to block malware and scan for viruses
- Be wary of any outlandish threats demanding quick payment through Bitcoin or gift cards
- Turn off electronic devices when not in use to limit potential vulnerabilities
- Cover your webcam when not using it for calls to prevent any remote access
6. What should I do if I already paid the ransom?
First, don’t panic. Contact your bank and Bitcoin exchange immediately to try halting the transaction if possible. Report the incident to the FBI’s Internet Crime Complaint Center at ic3.gov and notify your contacts about the scam.
Even if the payment went through, continue ignoring all communications from the scammer. Paying once does not guarantee they won’t threaten you again. Remain vigilant against future extortion attempts.
The Bottom Line on the HazardCC Hacker Extortion Scam
Being targeted by online extortion scams can be extremely frightening due to their invasive threats and ransom demands. However, knowledge is the key to protecting yourself.
By understanding how the scam operates and the false nature of their claims, you can avoid being manipulated through fear and urgency. Never pay ransoms which will only lead to further extortion attempts in the future.
The HazardCC hacker scam exploits common feelings of embarrassment and anxiety around compromising information being leaked publicly. But in reality, the scammers have no leverage over their victims aside from empty threats. Avoid reactionary steps, thoroughly secure accounts, and report the scam to put an end to their operation.
With insight into the psychological tricks and operational tactics used in these viral extortion scams, you can recognize the signs and avoid being caught off guard. Share information with family and friends to prevent scammers from profiting off anyone’s fear or lack of awareness.
Empower yourself with knowledge and reach out for assistance rather than caving to demands. By shedding light on how these schemes work, we can curtail the ability for online extortion scams to successfully manipulate and intimidate the public. Your power lies in recognizing their tactics and refusing to fall victim.