A deceptive online scam promoting fake Cath Kidston clearance sales has been heavily advertised on social media, tricking customers into purchasing from fraudulent websites. This article explains how the elaborate ruse works, how to avoid becoming a victim, and what to do if you have already fallen for the scam.


Overview of the Cath Kidston Clearance Sale Scam
A clever social media scam has emerged in recent months involving fake Cath Kidston clearance sale promotions used to defraud customers. Highly-targeted sponsored posts on Facebook, Instagram, TikTok, and other platforms bait users with unbelievable discounts over 90% off all products while claiming limited-time offers.
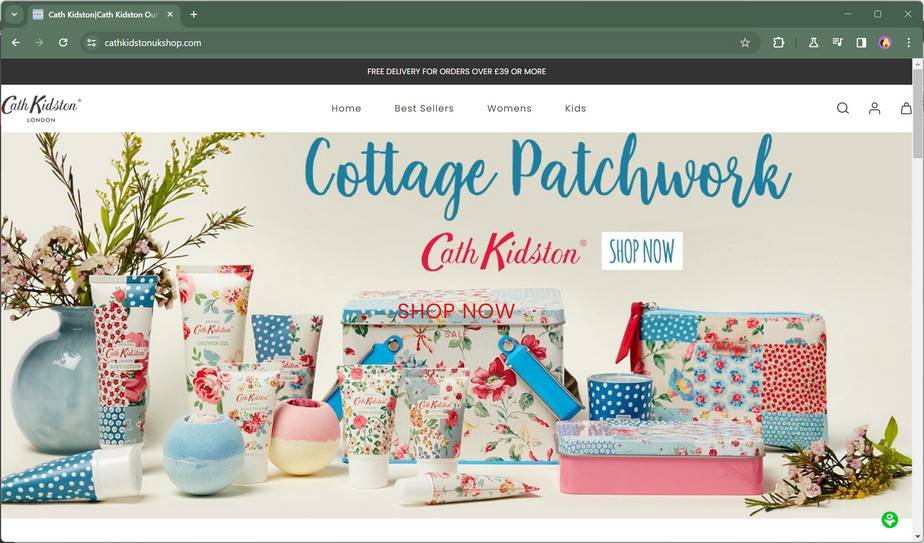
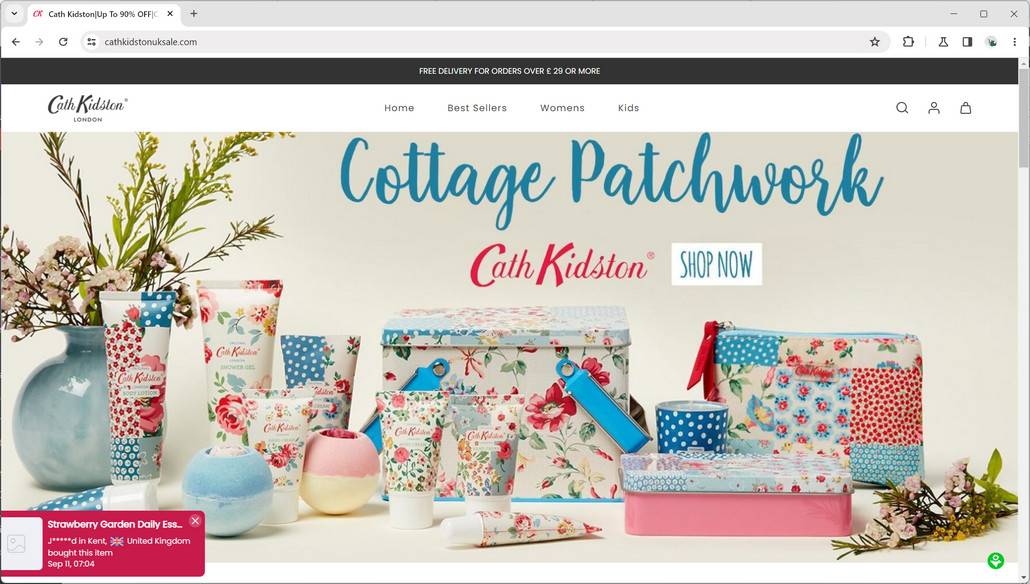
However, unsuspecting shoppers who click on these Cath Kidston ads do not actually arrive at a real clearance event on the brand’s official website. Instead, the links route through multiple redirects to sham ecommerce stores carefully crafted to mimic the look and feel of the genuine UK retailer.
Research reveals that a large network of interconnected fraudulent websites based in China has been specifically targeting Cath Kidston to capitalize on the company’s popularity for quintessentially British floral homewares and accessories. Collectively operating under the control of an unnamed criminal entity, these scam storefronts feature stolen product imagery and expertly copied branding elements, including Cath Kidston’s iconic logo and cheery patterns.
The sophisticated fakes easily dupe visitors upon first glance. But telltale signs exist across the scam sites indicating their illegitimacy to those who scrutinize further. Fictitious business addresses, lack of company history or a social media presence, and missing verifiable contact information beyond dubious email addresses all demonstrate these sham websites and clearance sales completely lack authenticity.
And crucially, while these fraudulent stores gladly accept payment and collect personal data at checkout, they do not actually ship out legitimate products. The vast majority of scammed shoppers end up receiving nothing at all for their money. For unlucky victims who do receive orders, the items tend to be cheap counterfeits made with inferior materials, tampered with or used goods, or entirely incorrect products unrelated to their original purchases.
By advertising fictitious clearance sales through social platforms bursting with deal-seekers, the sophisticated scam operation has devised an extremely effective strategy for cybersquatting a coveted brand, duping enthralled visitors, and scoring big payouts from defrauded online shoppers.
How the Fake Cath Kidston Clearance Sale Scam Works
The criminals behind the operation utilize social media ads to drive traffic to their network of fraudulent stores. Post promote clearance events with deep discounts over 90%, luring in deal-seeking shoppers.
Step 1: Creating Convincing Scam Websites
The fake web stores feature the Cath Kidston logo, brand imagery, and product catalog to make themselves appear as legitimate retailers. However, a closer look exposes multiple issues:
- Recently registered domains and cookie-cutter site templates
- Fictitious business addresses and contact details
- No social media pages or evidence of real-world presence
- Missing or vague “About” and “Terms” pages
Despite lacking transparency and authenticity, these copycat sites sufficiently mimic the look of a reliable online store at first glance.
Step 2: Posting Scam Social Media Ads
Once the scam web stores are online, the scammers launch social media ads to drive visitors. These sponsored posts target platforms like Facebook, Instagram, and TikTok.
The compelling ads boast unbelievable clearance discounts between 50-90% off all Cath Kidston products. Taglines entice users with slogans like “Going Out of Business Sale” and “Last Chance For Huge Savings.”
When users click these ads, the links route to the network’s fake shop websites instead of the real Cath Kidston store.
Step 3: Harvesting Customers’ Data and Money
Upon arriving at the scam sites through the ads, visitors browse what resembles a legitimate Cath Kidston online outlet. Without noticing any immediate irregularities, shoppers add clearance items to their carts.
At checkout, customers enter personal information like names, addresses, contact details. They also submit payment card numbers, security codes, and other sensitive financial data.
After completing orders, victims receive confirmation emails thanking them for their purchase. Yet most customers end up with one of the following disappointing outcomes:
- Receive nothing – The most frequent result, their money simply vanishes.
- Obtain knockoff or faulty goods – Cheap replicas made with inferior materials.
- Get randomly used, broken, or tampered items.
- Acquire completely incorrect products.
On top of selling sham or random wares, the criminals also now possess all the victims’ data to commit identity theft and drain bank accounts.
This data allows scam operators to steal more money, apply for illicit lines of credit, or sell info to other cybercrime rings. Victims soon find themselves battling more frauds and accounts opened illegally in their names – all because they entered details into one of these convincing fake websites.
Identifying Fake Cath Kidston Websites and Sales
While the fraudulent Cath Kidston scam websites put tremendous effort into appearing authentic, common red flags across these sham stores can help savvy shoppers avoid being duped by unbelievable clearance sale offers.
Carefully scrutinizing website elements and assessing validity of unusually deep discounts can protect consumers from surrendering money or personal data to criminal imposters.
Analyzing the Domain Details
One of the easiest initial checks is examining the domain name and registration details itself using an ICANN Whois lookup tool.
- Fake sites often use domain names that sound convincingly similar to the real brand, for example “CathKidsonOutletStore” instead of the real “CathKidston” address.
- Any domain registered very recently, such as within the past 3 months, warrants wariness rather than long-established sites live for years.
- Scam operators also often only register domains for short 1-year periods before abandoning them when the scam gets discovered.
- Domains using masked ownership data or complex corporate nesting structures aim to hide the real criminals perpetrating frauds through the websites.
Scrutinizing Too-Good-to-Be-True Discounts
One of the most obvious indicators involves deals exclusively advertised through social platforms rather than the company’s official channels promising jaw-dropping price slashes unlikely from a luxury brand.
- Genuine high-end companies run sales frequently, but very rarely offer over 50% – 75% off entire product lines or categories together simultaneously.
- Clearance discounts ranging up 90% likely indicate a scam attempt rather than a real promotion.
Checking for Contact and Company Details
Ensure company websites include verified phone numbers, physical addresses, leadership teams, and “About Us” company backgrounds before assuming their legitimacy.
- Scam websites lack the ability to conduct genuine business so frequently fail to provide actual means of contacting company representatives.
- Any company unwilling to openly share basic operational details hides something nefarious.
Assessing Social Media Engagement
Visit all the official brand social media pages to check whether website deals got posted there or seem referenced anywhere else besides the targeted ads driving traffic.
- Scam stores exist solely online as fake fronts without any non-digital presence, while legitimate brands maintain strong real-world followings across multiple channels.
With these warning signs of potentially fraudulent discounts and storefronts in mind, shoppers can more easily single out sophisticated scam attempts and steer clear of online retail fraudsters.
Identifying Scam Cath Kidston Ads on Social Media
In addition to creating entire fake ecommerce stores, the criminal ring behind the fraudulent Cath Kidston clearance sales leverages sponsored social media ads to target deal-seeking users and drive traffic to their scam websites.
Highly compelling posts explicitly promoting unbelievable discounts frequently appear in Facebook feeds, Instagram Stories and Explore pages, and TikTok streams. While seeming legitimate, certain patterns expose their deceitful intentions.
Spotting Sham Facebook Ads
Facebook allows extensive ad targeting options and fraudsters exploit these to precision target ads by interest keywords including “clearance sales,” “limited time offers,” and of course “Cath Kidston discounts.”
Some common features helping distinguish scam Cath Kidston Facebook ads include:
- Exceptionally decreased prices like “Entire Store 90% Off!” trying luring shoppers based on extreme FOMO.
- Urgency messaging like “Going Out of Business Sale – Today Only!” also preys on fear-of-missing bargains.
- Links routing through multiple redirects rather than directly to a retailer website.
- Landing site URLs not containing the actual brand name (e.g. “boutiquestoresale” vs “cathkidston”).
- Ad accounts consistently change names to avoid bans once scam gets reported.
Identifying Fraudulent Instagram Ads
- Heavy use of stock photos rather than real brand imagery due to lack of official approval.
- Tagged posts primarily target middle-aged women based on the brand’s core demographic.
- Video clips rely on clips ripped from authentic brand promos then edited to include scammy text overlays and urgency music.
- Accounts repeatedly change handles once reported but continue running near-identical ads.
Spotting Sham TikTok Ads
- Video ads lifted from vintage brand content now overlaid with huge animated text and arrows highlighting clearance event.
- Constant rotation of new accounts to keep scam ads flowing as previous accounts get banned.
- Designed to trigger intrigue and urgency with rapidly flashing “Last Chance!” messages while displaying massive ~90% discount badges.
What To Do If You Already Fell For the Scam
If you placed an order through one of these fraud Cath Kidston clearance sale websites, take action immediately to protect yourself and minimize damages. Follow this checklist:
Step 1: Contact Banks and Monitoring Agencies
Since the crooks have your financial information, notify your credit card provider and banks of potential identity theft. Place fraud alerts on all accounts and carefully monitor statements for unauthorized charges. Sign up for identity theft protection services for extra surveillance on your credit files and personal data.
Step 2: Watch for Suspicious Activity
Remain vigilant across all accounts, contacts, and communications channels in upcoming weeks. Scammers who stole your information at checkout often wait before using it to avoid detection. Look out for unfamiliar logins, withdrawals, opened accounts, credit hits, and other signs of misuse of your personal or financial data.
Step 3: Report the Incident
File reports about the incident and fraudulent website with various agencies. Submit complaints to the FTC (Federal Trade Commission), IC3 (Internet Crime Complaint Center), and BBB (Better Business Bureau) Scam Tracker. Also contact your local police department to have an official report on file. Provide copies when disputing charges or accounts opened illegally using your identity.
Step 4: Issue Chargebacks
Call your credit card provider and banks to report transactions with the scam website as fraudulent. Request to chargeback any purchases to possibly recoup lost payment funds. Act fast, as many card companies have time limits to dispute charges, often between 90-120 days from the transaction date.
By taking swift action and reporting the scam, you can prevent the stolen data from being used against you in additional cybercrimes. Remain extra vigilant to catch all instances of fraud as information gets sold in black markets. Over time with diligence, you can contain the damage and restore security.
Frequently Asked Questions About the Cath Kidston Scam
Still unsure about the sophisticated Cath Kidston clearance sale scam sweeping social platforms? Read on for simple answers surrounding the fraud’s most common questions.
What makes the Cath Kidston scam so deceiving online?
Highly-convincing fake ecommerce stores mimic the real website to confuse visitors. Scammers also leverage precision-targeted social media ads optimized to entice middle-aged women who align with the brand’s core demographic based on interests like home décor and floral patterns.
How do I identify the name of fraudulent sites?
Fake domains either directly misappropriate the brand’s name and trademarks or choose confusingly similar phrases like “CathKidsonFashion” or “CathKidstonFactoryOutlet” versus the genuine site, CathKidston.com.
Why offer such deep discounts like 90% off?
Extreme discounts beyond 50% exploit human psychology surrounding sales and scarcity. Seeing exaggerated yet believable clearances triggers irresistible urges to snag deals despite limited quantities available.
Are the discounted products shown even real?
No. All product imagery gets stolen directly from the legitimate website. Scammers never actually possess any real Cath Kidston inventory to sell at any price, discounted or not.
What happens if I order from a scam website?
Most likely your money and details disappear with nothing shipped. In rarer cases of items arriving, customers receive cheap knockoffs, broken goods, or random products utterly different than described.
Can I get scammed just by browsing?
Possibly. Merely accessing scam sites exposes devices to potential malware risks if clicking ads or download prompts. Entering information like emails for abandoned carts also flags you for more spam.
How exactly do scammers profit through fake sites?
The criminal networks earn money via payments and bank details collected at misleading checkouts. They also sell personal data taken to shady dark web brokers seeking profiles for identity fraud.
Who actually runs these types of global shopping scams?
Complex interconnected rings coordinated largely from China specialize in mass ecommerce deception through networks of fraudulent storefronts, ads, malware, and identity harvesting funnel money indirectly to ringleaders.
How long do these shopping scams usually last?
Weeks or months typically pass before sites get discovered, blacklisted, and taken down. But the scam operators continue launching new fakes, domains, ads, and redirects in ongoing cycles.
With insight on this rampant social scam, shoppers can dodge traps set by exploitative fraudsters and help curb global ecommerce deception.
Conclusion
Bogus Cath Kidston clearance websites advertise unbelievable discounts across social platforms trying to fool deal-seeking shoppers. But their actual purpose is harvesting customer information and payments without providing products.
If you got scammed, take urgent fraud-prevention measures to contain damages from stolen data. Learn the warning signs like extreme price cuts or missing contact info to dodge the ruse. With caution assessing deals that look too good to be true, you can stop online retail scammers in their tracks.