A new cryptocurrency scam has emerged on social media platforms like Facebook, Twitter, Instagram and TikTok, falsely claiming to offer free crypto giveaways sponsored by Elon Musk. This comprehensive article will provide an in-depth expose on how this scam works, how to identify fake posts and accounts promoting it, and most importantly, how to avoid falling victim.
Elon Musk ‘New Crypto Exchange Based On Web3’ Scam Overview
A cryptocurrency scam has been spreading across social media platforms like Facebook, TikTok, Twitter, and Instagram. The scam uses Elon Musk’s name and image without his consent to promote a fake cryptocurrency giveaway. This is a classic crypto scam designed to steal money from unsuspecting victims.
Here is the typical text of the scam site:
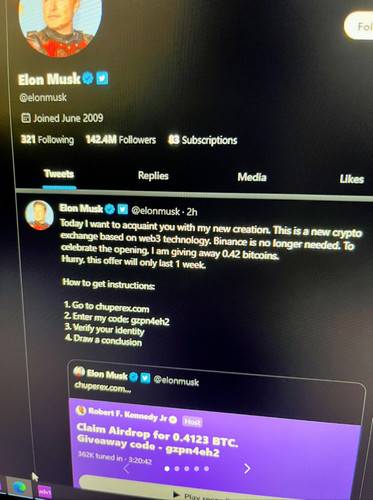
Elon Musk on Twitter: Today I want to acquaint you with my new creation. This is new crypto exchange based on web3 technology. Binance is no longer needed. To celebrate the opening, I’m giving away 0.42 bitcoins. Hurry, this offer will only last 1 week. How to get instructions.
1 Go to [scam site].
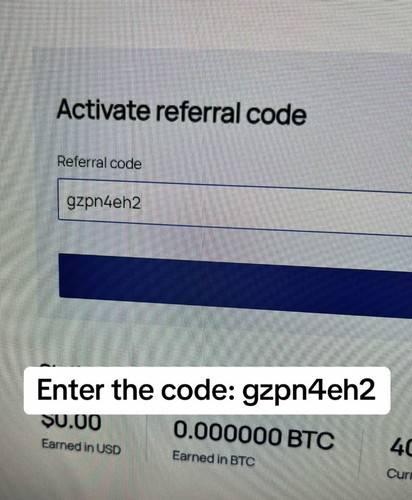
2 Enter my code: gzpn2eh2.
3. Verify your Identity.
4. Draw a conclusion
The scam claims that Elon Musk has created a new cryptocurrency exchange based on web3 technology that makes platforms like Binance obsolete. It states that to celebrate the launch of this non-existent exchange, Elon Musk is giving away 0.42 bitcoins.
The scam instructs targets to visit a website, enter a promotional code, verify their identity, and then collect their cryptocurrency prize. However, the website is fraudulent, designed only to collect personal information and payments from victims. There is no Elon Musk crypto giveaway.
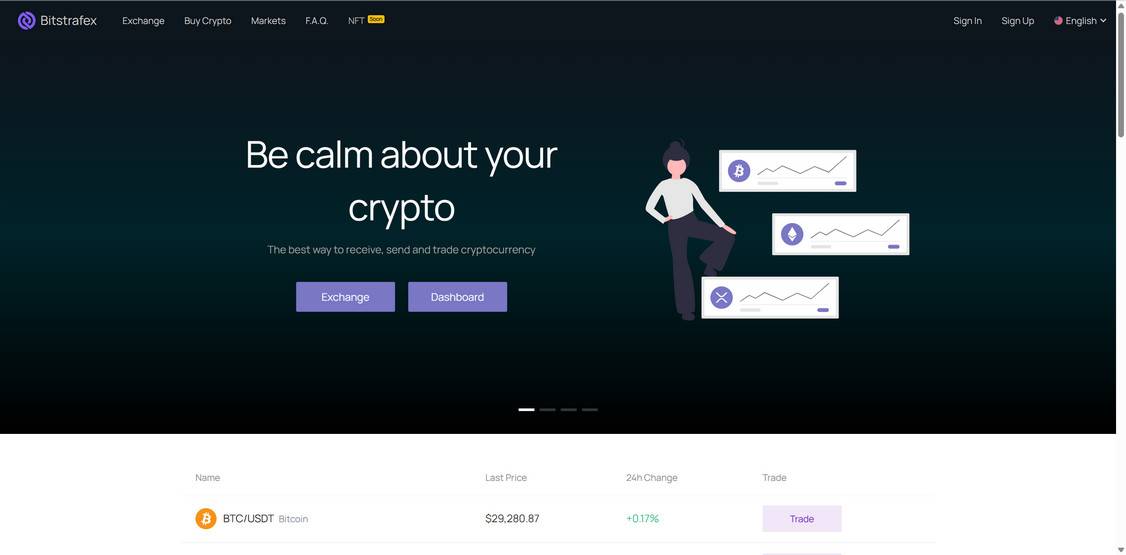
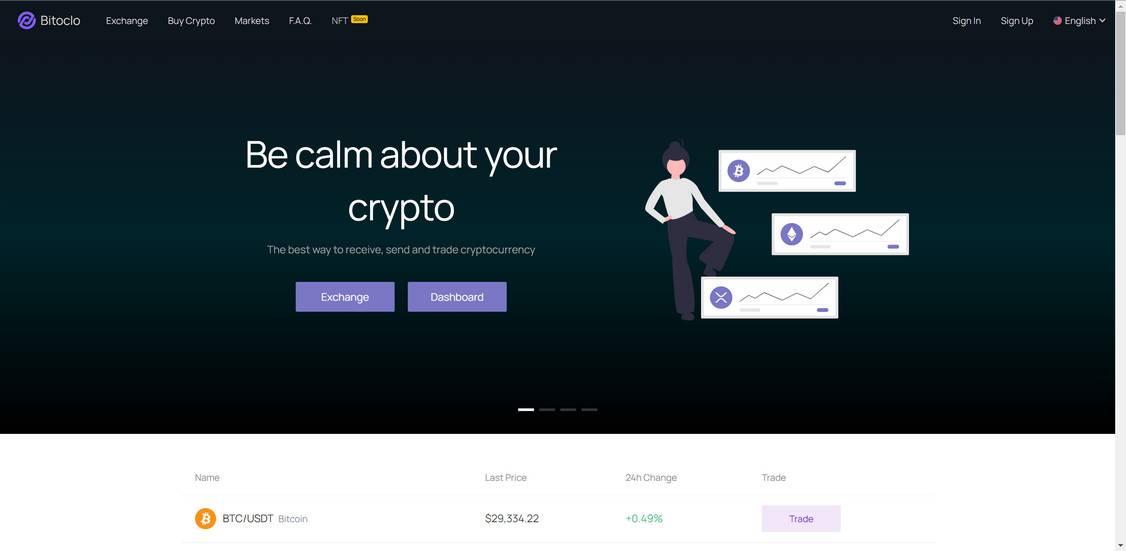
Here is how the scam sites look:
This scam is simply a way for criminals to steal money and personal information from social media users. Do not fall for it under any circumstances.
How the Elon Musk ‘New Crypto Exchange Based On Web3’ Scam Works
The crypto giveaway scam uses social engineering tactics to convince targets that they can get free cryptocurrency if they follow a few simple steps.
Here is how the scam typically works:
- The victim comes across a post on social media (Facebook, Instagram, etc.) advertising a cryptocurrency giveaway sponsored by Elon Musk. The post contains Elon Musk’s name and photo to make it seem legitimate.
- The scam post claims that Elon Musk has created a new cryptocurrency exchange and is giving away cryptocurrency to celebrate. It states that Binance and other popular exchanges are now obsolete thanks to Elon’s new creation. This establishes urgency and excitement.
- The scam instructs the target to visit a website, enter a promotional code, and provide personal information to collect their free crypto prize. The website looks professional but is fake.
- Once on the website, the target is prompted to send a small amount of cryptocurrency to “verify their identity.” They are promised that this amount will be refunded along with the promised giveaway payout. In reality, any cryptocurrency sent is stolen.
- The website also collects personal information from the target through verification forms. This information can be used for identity theft.
- After sending cryptocurrency and providing personal information, the target never receives any giveaway payout. The criminals behind the scam walk away with the cryptocurrency sent and any stolen personal information.
The scam relies entirely on the use of Elon Musk’s name and fake promises to convince targets to willingly send cryptocurrency and give up personal information. No actual giveaway exists.
Targets of the Elon Musk ‘New Crypto Exchange Based On Web3’ Scam
The primary targets of this crypto scam are active social media users who have at least some knowledge or interest in cryptocurrencies. Specific demographics include:
- Young adults aged 18-35 who are active on social media.
- Existing cryptocurrency traders and investors who understand how to send/receive crypto.
- Elon Musk fans who may believe he is truly giving away cryptocurrency.
- Individuals who lack knowledge of common online scams and cybersecurity best practices.
- People experiencing financial distress who desperately hope the scam is real.
The scam targets those who are most likely to know how to transfer cryptocurrency while also being naive enough to fall for the fake promises. Knowledge without wisdom allows this scam to succeed.
How to Spot The Elon Musk ‘New Crypto Exchange Based On Web3’ Scam
While this Elon Musk cryptocurrency giveaway scam can look convincing at first, there are a number of red flags that can help you identify and avoid it:
- Promises of guaranteed massive returns or get-rich-quick schemes should always raise suspicion. If it seems too good to be true, it usually is.
- Elon Musk has never conducted a random cryptocurrency giveaway. Any promotion using his name or likeness without his explicit endorsement should be considered fraudulent.
- Look closely at the website URL – it likely contains typos or odd words and is not an official Elon Musk or company domain.
- The scam website generally looks unprofessional with spelling/grammar errors. Legitimate businesses do not have these issues.
- Claims that you need to send cryptocurrency first in order to “verify” your identity or enable the payout are always scams. Never send currency to “unlock” a fake promotion.
- Aggressive time pressure such as “act fast before time runs out!” is meant to bypass your critical thinking. Don’t fall for it.
- Accounts spreading the scam offer may have been hacked/compromised or have other signs of inauthenticity like being recently created.
Always research any viral promotion thoroughly before taking action. And never provide personal information or currency to an unverified entity.
What to Do if You Are a Victim
If you have fallen victim to the fake Elon Musk cryptocurrency giveaway scam, here are some important steps to take right away:
- Report the scam – Report the social media post, account, and website to the appropriate platform. This helps get fraudulent content shut down quicker.
- Notify your contacts – If the scam originated from a hacked/compromised account of someone you know, notify them so they can regain control of their account.
- Change passwords – Update passwords for any online accounts, particularly your cryptocurrency exchange accounts. Enable 2-factor authentication if possible.
- Monitor accounts – Watch for any suspicious activity in your online accounts in case your personal information was compromised. Freeze credit if needed.
- Contact authorities – File a complaint with the Federal Trade Commission (FTC), Internet Crime Complaint Center (IC3), and local law enforcement. Provide all scam details.
- Dispute unauthorized charges – If the scam involved unauthorized credit card charges, contact your provider immediately to dispute the charges.
- Consult experts – Speak with qualified fraud resolution specialists for advice tailored to your specific situation. They can help maximize recovery efforts.
The most important thing is to act quickly to minimize damage and prevent further losses. Unfortunately, recovery of lost cryptocurrency or personal information is very rare, so vigilance is key.
Frequently Asked Questions
Is Elon Musk really giving away free cryptocurrency?
No, these viral social media posts promising free cryptocurrency giveaways from Elon Musk are all scams designed to steal money and information from victims. Elon Musk is not associated with any online crypto giveaways.
How do I tell if an online crypto promotion is a scam?
Warning signs include promises of guaranteed huge returns, pressure to act quickly, mismatched or unprofessional website URLs, grammar/spelling errors, and any requirement to send cryptocurrency to “verify” your identity or enable withdrawal. If unsure, search online for the company name + words like “scam” or “complaint” to uncover reports.
Can I get back the money I lost to the crypto scam?
Unfortunately, recovery of lost cryptocurrency is very rare since transactions are irreversible. You should still report the scam to relevant authorities in case law enforcement is able to identify the criminals. Avoid further engagement with the scammers as this will likely lead to additional losses.
Is there anything I can do if my information was compromised?
If you provided personal information, immediately change any affected passwords and monitor your accounts closely for suspicious activity. Enable 2FA where possible for additional security. Consider placing a freeze on your credit to prevent identity theft. Be wary of any future contact regarding the scam as scammers may target victims multiple times.
Can I report a scam if I’m not sure the details I have are totally accurate?
Yes, you should still report any details you have including website, social media handles used, cryptocurrency wallet addresses, etc. Law enforcement agencies are skilled at analyzing partial information to join dots and identify criminals. Every little bit helps even if your recall is not perfect.
Conclusion
I hope this detailed overview has provided insight into how the “Elon Musk cryptocurrency giveaway” social media scam operates, as well as recommendations on how to spot, avoid, report, and recover from cryptocurrency scams. Please share this information to help protect others from falling victim to online fraud. Let me know if you have any other questions!